164
Options List
NTP Authentication
Authentication involves advanced configuration for NTP, and used to prevent tampering with the
timestamps on the logs generated by devices. You can configure a device to authenticate the time
sources to which the local clock is synchronized. When you enable NTP authentication, the device
synchronizes to a time source only if the source carries one of the authentication keys specified by
the ntp trusted-key command. The device drops any packets that fail the authentication check and
prevents them from updating the local clock. NTP authentication is disabled by default.
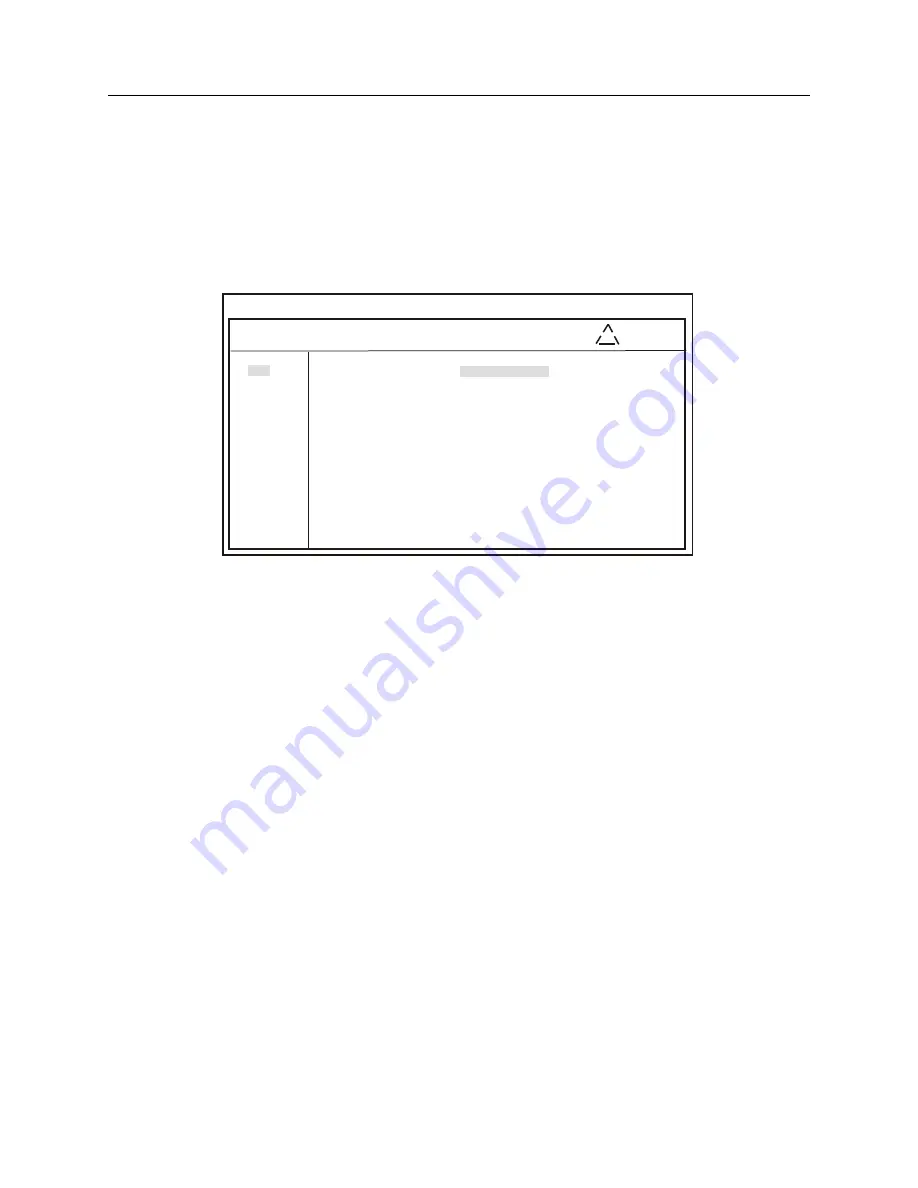
Status Configure [ Authentication ]
[X] Enable Authentication
Key Table
ID Format Key Trusted
[ ] [M] [ ] [ ]
Apply Reset
[ ] [M] [ ] [ ]
[ ] [M] [ ] [ ]
[ ] [M] [ ] [ ]
[ ] [M] [ ] [ ]
ARBITER
SYSTEMS
Option 34 Network Time Module
[NTP]
PTP
SNMP
Clock
Network
System
Support
Logout
Computer Name (or IP address) – ssh – 80x24
Figure C.41: NTP Authentication Page Using SSH
There are four authentication formats (S, N, A, M) with different rules for each of the keys. For
example, a type M format (MD5) allows the key to have up to 31 ASCII characters like a password.
The key ID is an integer and identifies the NTP server key. If authentication is enabled, the client
will only synchronize with the server if it is trusted. Therefore, you must select the ”Trusted” check
box on the authentication page.
Содержание 1092A
Страница 4: ...iv ...
Страница 18: ...xviii LIST OF TABLES ...
Страница 129: ...C 10 Option 20A Four Fiber Optic Outputs 111 Figure C 7 Option 20A Jumper Locations ...
Страница 131: ...C 11 Option 27 8 Channel High Drive 113 Figure C 8 Option 27 Jumper Locations ...
Страница 148: ...130 Options List Figure C 10 Option 29 Connector Signal Locations ...
















































