IAS-2000 v2
User’s Manual
.
73
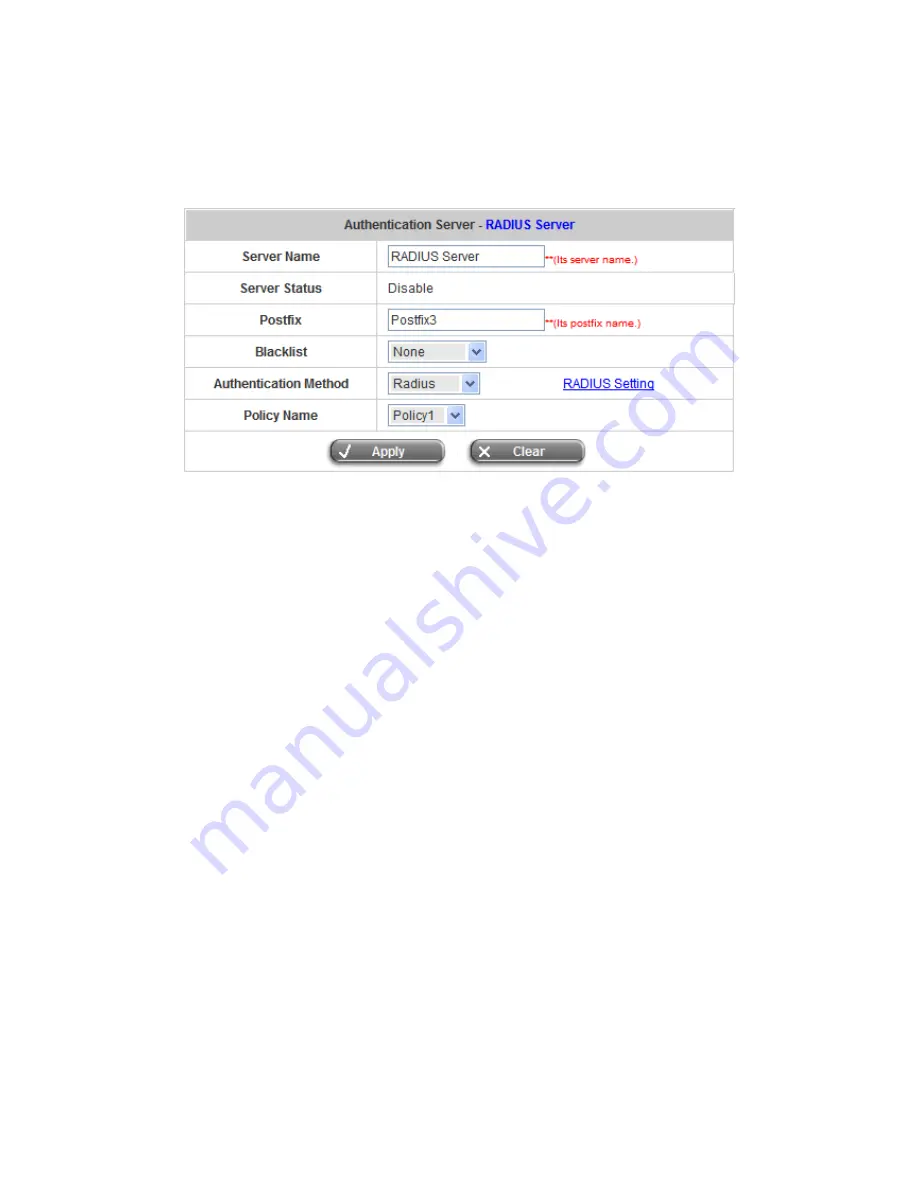
5.3.1.3 Radius
Server
Choose
“Radius”
in the
Authentication Method
field, the hyperlink beside the pull-down menu will become
“RADIUS Setting”
.
y
Server Name:
Set a name for the server using numbers (0 to 9), alphabets (a to z or A to Z), dash (-),
underline (_) and dot (.) with a maximum of 40 characters, all other letters are not allowed.
y
Sever Status:
The status shows that the server is enabled or disabled.
y
Postfix:
Set a postfix that is easy to distinguish (e.g. Local) for the server by using numbers (0 to 9), alphabets
(a to z or A to Z), dash (-), underline (_) and dot (.) with a maximum of 40 characters, all other letters are not
allowed.
y
Blacklist:
There are five sets of the black lists. Select one of them or choose
“None”
. Please refer to
5.3.3
Black List Configuration
y
Authentication Method:
There are four authentication methods,
POP3
,
Radius
,
LDAP
and
NTDomain
to
configure from. Select the desired method and then click the link besides the pull-down menu for more
advanced configuration.
y
Policy Name:
There are ten policies to choose from to apply to this particular server.
Содержание IAS-2000 V2
Страница 1: ...IAS 2000 v2 Internet Access Gateway User s Manual 1 ...
Страница 11: ...IAS 2000 v2 User s Manual 4 ...
Страница 59: ...IAS 2000 v2 User s Manual 52 ...
Страница 100: ...IAS 2000 v2 User s Manual 93 Bandwidth Choose one bandwidth limit for that particular policy ...
Страница 131: ...IAS 2000 v2 User s Manual 124 5 5 1 System Status This section provides an overview of the system for the administrator ...
Страница 163: ...IAS 2000 v2 User s Manual 156 z For Firefox ...






























