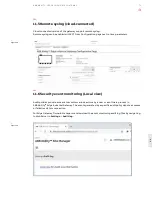
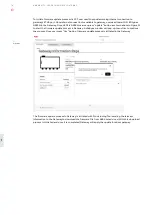
11
A B B A B I L I T Y
T M
ED G E I N D US T R I A L G AT E WAY
64
—
11.1 Secure system setup
11.1.1 Basic system hardening rules
Today's distribution automation systems are basically specialized IT systems. Therefore, several rules
of hardening an automation system apply to these systems, too. Protection and control relays are from
the automation system perspective on the lowest level and closest to the actual primary process.
It is important to apply defense-in-depth information assurance concept where each layer in the
system is capable of protecting the automation system and therefore protection and control relays are
also part of this concept.
The following should be taken into consideration when planning the system protection.
• Recognizing and familiarizing all parts of the system and the system's communication links.
• Removing all unnecessary communication links in the system.
• Rating the security level of remaining connections and improving with applicable methods.
• Hardening the system by removing or deactivating all unused processes, communication ports and
services.
• Checking that the whole system has backups available from all applicable parts.
• Collecting and storing backups of the system components and keeping those up-to-date.
• Removing all unnecessary user accounts.
• Defining password policies.
• Changing default passwords and using strong passwords.
• Checking that the link from substation to upper level system uses strong encryption and
authentication.
• Segregating public network (untrusted) from automation networks (trusted).
• Segmenting traffic and networks.
• Using firewalls and demilitarized zones.
• Assessing the system periodically.
• Using malware protection in workstations and keeping those up-to-date.
It is important to utilize the defence-in-depth concept when designing automation system security.
It is not recommended to connect a device directly to the Internet without adequate additional security
components. The different layers and interfaces in the system should use security controls.
Robust security means, besides product features, enabling and using the available features and also
enforcing their use by company policies. Adequate training is also needed for the personnel accessing
and using the system.
—
Cyber Security Deployment Guideline
Содержание Ability
Страница 1: ... USER MANUAL ABB AbilityTM Edge Industrial Gateway ...
Страница 2: ...ABB ABILIT Y TM EDGE INDUSTRIAL GATEWAY 2 ...
Страница 4: ......
Страница 6: ......
Страница 12: ......
Страница 16: ...ABB ABILIT Y TM EDGE INDUSTRIAL GATEWAY 16 ...
Страница 21: ...ABB ABILIT Y TM EDGE INDUSTRIAL GATEWAY 21 3 ...
Страница 22: ...ABB ABILIT Y TM EDGE INDUSTRIAL GATEWAY 22 4 ...
Страница 28: ...ABB ABILIT Y TM EDGE INDUSTRIAL GATEWAY 28 5 ...
Страница 34: ...6 ABB ABILIT Y TM EDGE INDUSTRIAL GATEWAY 34 ...
Страница 44: ...7 ABB ABILIT Y TM EDGE INDUSTRIAL GATEWAY 44 ...
Страница 48: ...8 ABB ABILIT Y TM EDGE INDUSTRIAL GATEWAY 48 ...
Страница 54: ...9 ABB ABILIT Y TM EDGE INDUSTRIAL GATEWAY 54 ...
Страница 58: ...1 0 ABB ABILIT Y TM EDGE INDUSTRIAL GATEWAY 58 ...
Страница 61: ...ABB ABILIT Y TM EDGE INDUSTRIAL GATEWAY 61 1 0 ...
Страница 62: ...1 1 ABB ABILIT Y TM EDGE INDUSTRIAL GATEWAY 62 ...
Страница 76: ...1 2 ABB ABILIT Y TM EDGE INDUSTRIAL GATEWAY 76 ...
Страница 80: ...1 3 ABB ABILIT Y TM EDGE INDUSTRIAL GATEWAY 80 ...
Страница 84: ...ABB ABILIT Y TM EDGE INDUSTRIAL GATEWAY 84 1 4 ...
Страница 88: ...ABB ABILIT Y TM EDGE INDUSTRIAL GATEWAY 88 1 5 ...
Страница 94: ...ABB ABILIT Y TM EDGE INDUSTRIAL GATEWAY 94 1 6 ...
Страница 99: ...ABB ABILIT Y TM EDGE INDUSTRIAL GATEWAY 99 1 6 ...