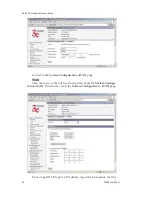
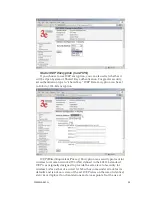
3e-525A Wireless Access Point
10
29000132-001 A
29000132-001 A
11
Installation Instructions
The 3e-525A is intended to be installed as part of a complete wireless design
solution.
This manual deals only and specifically with the single 3e-525A device as a
unit. The purpose of this chapter is the description of the device and its identifi-
able parts so that the user is sufficiently familiar to interact with the physical unit.
Preliminary setup information provided below is intended for information and
instruction of the wireless LAN system administration personnel.
It is intended, and is the philosophy of 3e Technologies International, that
the user not be required to open the individual unit. Any maintenance required
is limited to the external enclosure surface, cable connections, and to the man-
agement software (as described in chapter three through five) only. A failed unit
should be returned to the manufacturer for maintenance. Sites requiring emer-
gency backup should maintain extra units of the device to interchange in case of
failure.
Minimum System and Component Requirements
The 3e-525A is designed to be attached to the wall at appropriate locations.
To complete the configuration, you should have at least the following compo-
nents:
• PCs with one of the following operating systems installed: Windows NT
4.0, Windows 2000 or Windows XP;
• A compatible 802.11b or 802.11g PC Card or 802.11b or 802.11g device
for each computer that you wish to wirelessly connect to your wireless
network. (For wireless cards, and praticularly if you will be using secure
FIPS mode with AES, we recommend that you select the 3e-110 PC
Card with 3e-010F Crypto Client software (sold separately) or install the
3e-010F software with any compatible PC Card. (If you will be using
WEP, the 3e-010F software is not required);
• Access to at least one laptop or PC with an Ethernet card and cable that
can be used to complete the initial configuration of the unit.
• A Web browser program (such as Microsoft Internet Explorer 5.5 or later,
or Netscape 6.2 or later) installed on the PC or laptop you will be using
to configure the Access Point.
• TCP/IP Protocol (usually comes installed on any Windows PC.)
Ensure the Cabling is Correctly Installed
The 3e-525A is well-protected in a metal enclosure which is generally bolted
to a surface. The device should not be opened.
The following illustration shows the external cable connectors on the 3e-
525A.
Содержание 3e-525A
Страница 3: ...This page intentionally left blank ...
Страница 9: ...vi 29000132 0001 A This page intentionally left blank ...
Страница 41: ...3e 525A Outdoor Access Point 32 29000132 001 A ...
Страница 53: ...3e 525A Outdoor Access Point 44 29000132 001 A This page intentionality left blank ...
Страница 105: ...3e 525A Wireless Access Point 96 29000132 001 A This page intentionally left blank ...