Serie 750, 753
Planning
32
System manual | Version: 3.0.2
•
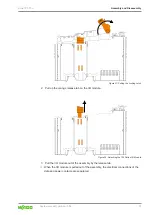
Improve shielding performance with a large contact area
Greater shielding performance is achieved via low-impedance connection between
shielding and ground. To achieve this, connect the shielding over a large surface area,
e.g., using the WAGO 790 Shield Connection System. This is especially recommended
for large-scale systems where equalizing or high impulse currents may occur.
4.2.8 Data Security
Professional planning and design is an important requirement for securing data confiden-
tiality, availability and integrity.
Random Influences
Data transmission and processing can be disrupted by random influences, such as tem-
porary electromagnetic disturbances. Proper setup can significantly reduce the likelihood
of corruption or destruction of data.
More information about this topic:
8
Deliberate Influences
Use in ETHERNET Areas
ETHERNET products are designed for use in local networks. Please note the following
when using ETHERNET products in your system:
• Do not connect control components and control networks to an open network such as
the Internet or an office network.
WAGO recommends putting control components and control networks behind a fire-
wall.
• In the control components, close all ports and services (e.g., for WAGO-I/O-
CHECK
and CODESYS) not required by your application to minimize the risk of cyber attacks
and to enhance cybersecurity.
Only open the ports and services for the duration of the commissioning/configuration.
• Limit physical and electronic access to all automation components to authorized per-
sonnel only.
• To reduce the risk of unauthorized access to your system, change the default pass-
words before first use.
• To reduce the risk of unauthorized access to your system, regularly change the pass-
words used.
• To verify that the measures taken meet your security requirements, regularly perform
threat analyses.
• To restrict access to and control of individual products and networks, employ a “de-
fense-in-depth” mechanism in your system’s security configuration (
&
White Paper
Cybersecurity in Production Facilities
).
Table 8: Additional documentation
Document Type
Name
&
Manual
Cybersecurity for PFC100 / PFC200 Controllers
&
White Paper
Cybersecurity in Production Facilities