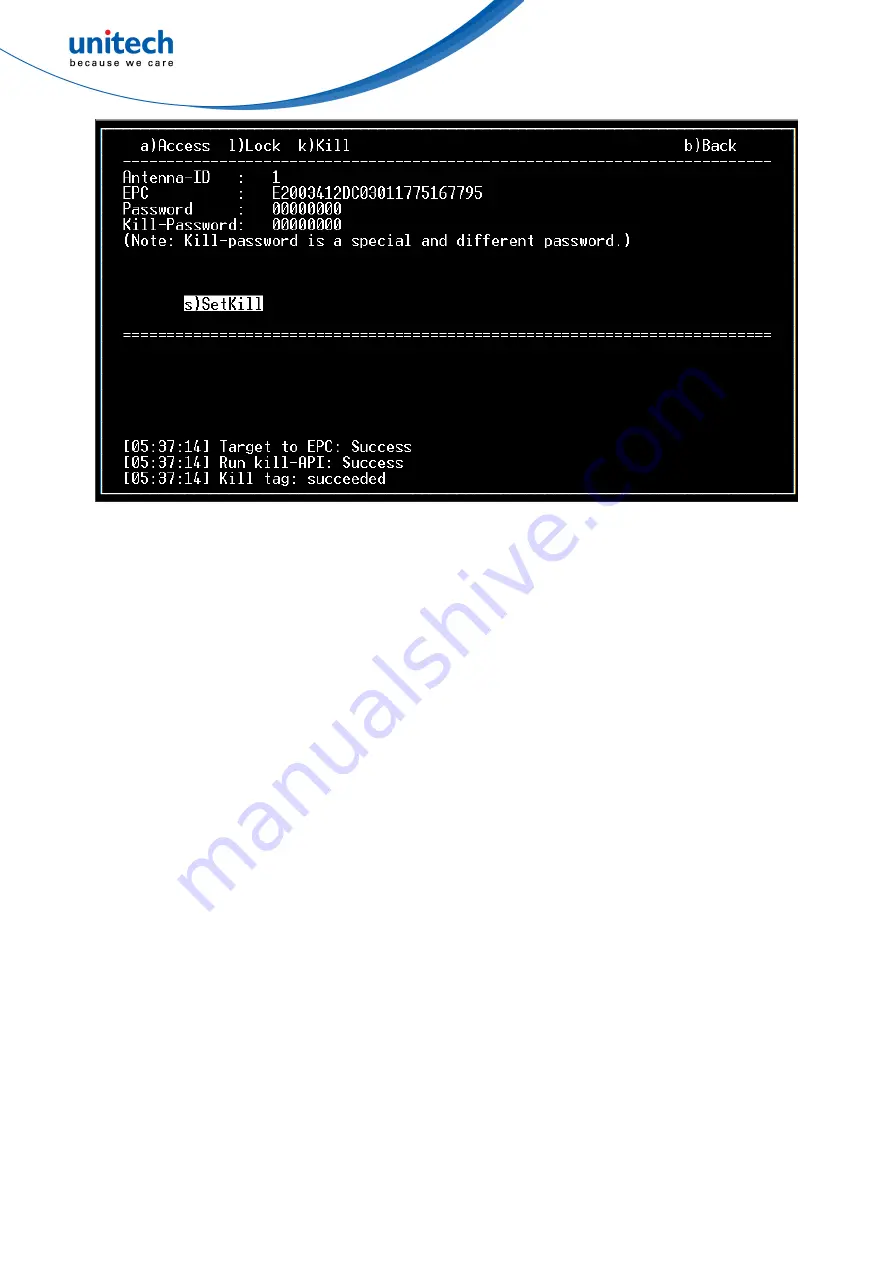
Fig. 84. The Kill operation
5.4. Errors
The two most common errors of Tag-operation are the memory and security issue that
described in the following sub-sections. With no worries, the Log section would also show
other errors as well.
5.4.1. Memory
Like the descriptions in section 0 and 5.1.6, the size of the memory bank of a tag has its
limitation. For instance, when the application attempts to read the memory out of the size of
the EPC bank, the Log section returns the error message, “<ERROR> BACKSCATTER: 0x3
- Memory location doesn't exist,” as shown in Fig. 85.
52













































