Preface
ix
Document Set
The following documents are provided with your product.
Documentation and Software Updates
For the latest documentation and software updates, visit the Trend Micro Download
Center at:
http://downloadcenter.trendmicro.com/
T
ABLE
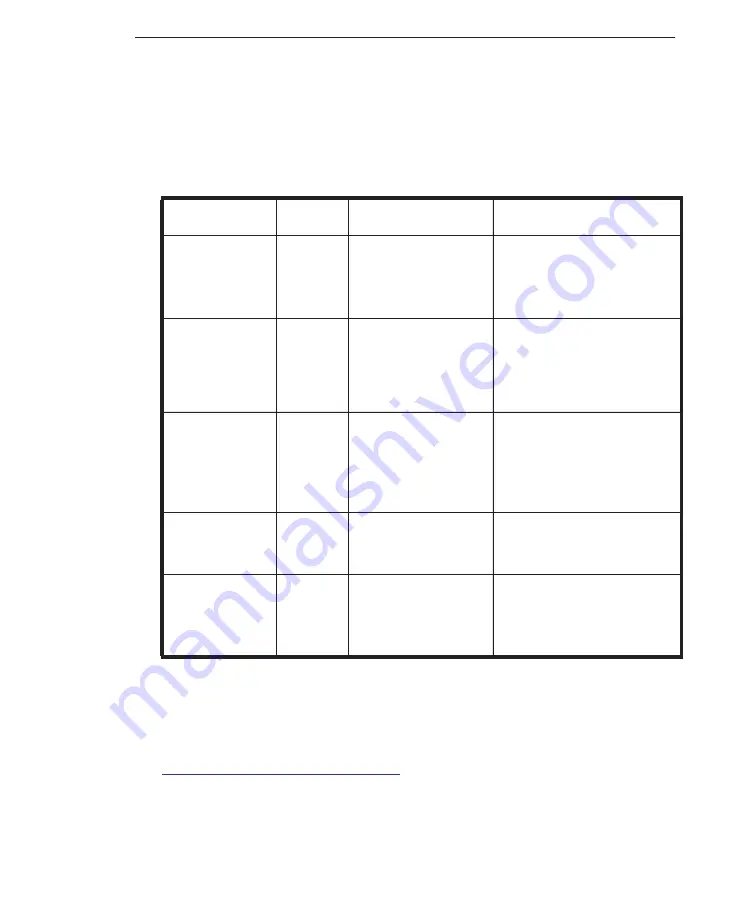
P-2.
Product documentation
D
OCUMENT
F
ORMAT
L
OCATION
C
OVERAGE
Installation and
Deployment
Guide
•
USB flash drive
•
Trend Micro
Download
Center
Guides you through device
installation, deployment,
and initial configuration
Administra-
tor’s Guide
•
USB flash drive
•
Trend Micro
Download
Center
Explains features and
guides your through man-
aging policies, administra-
tive tasks, and
troubleshooting
Quick Start
Guide
PDF
and
print
•
USB flash drive
•
Trend Micro
Download
Center
•
Product package
Provides an overview of
the device and initial tasks
Online Help
Web
pages
•
Web console
Explains options on the
web console and relevant
tasks
Readme
Text
•
USB flash drive
•
Trend Micro
Download
Center
Provides late-breaking
news and software build
information
Summary of Contents for viruswall enforcer 1500i
Page 1: ......
Page 7: ...Trend Micro Network VirusWall Enforcer 1500i Installment and Deployment Guide vi...
Page 13: ...Trend Micro Network VirusWall Enforcer 1500i Installment and Deployment Guide xii...
Page 30: ...Getting Started 2 11 FIGURE 2 7 Standard four port configuration Port 1 Port 3 Port 4 Port 2...
Page 59: ...Trend Micro Network VirusWall Enforcer 1500i Installment and Deployment Guide 3 20...
Page 78: ......