50
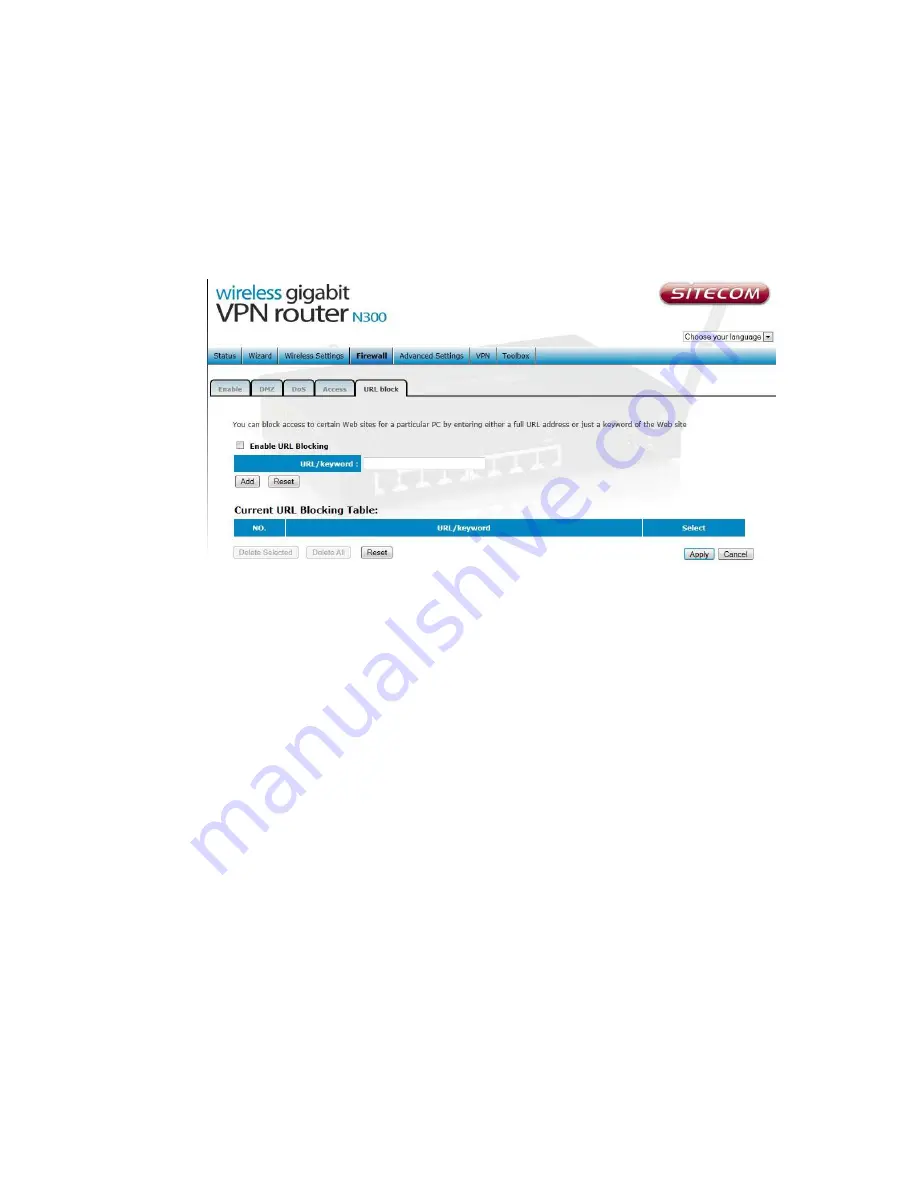
URL block
You can block access to some Web sites from particular PCs by entering a full
URL address or just keywords of the Web site.
Enable URL
Blocking Enable/disable URL Blocking
Add URL Keyword
Fill in “URL/Keyword” and then click “Add”. You can enter
the full URL address or the keyword of the web site you want to block.
Remove URL Keyword
If you want to remove some URL keywords from the
"Current URL Blocking Table", select the URL keyword you want to remove in
the table and then click "Delete Selected". If you want remove all URL
keywords from the table, just click "Delete All" button. If you want to clear
the selection and re-select again, just click “Reset”.
Click <
Apply
> at the bottom of the screen to save the above configurations
Summary of Contents for N300
Page 1: ...WLR 4002B ...
Page 5: ......
Page 15: ...15 7 Setup LAN WAN WAN connection ...
Page 16: ...16 LAN connection ...
Page 29: ...29 Statistics Shows the counters of packets sent and received on WAN LAN WLAN ...
Page 37: ...37 Disable When you choose to disable encryption it is very insecure to operate the router ...
Page 65: ...65 8 Enable the VPN policy and then click Apply to save the VPN profile ...
Page 68: ...68 8 Enable the VPN policy and then click Apply to save the VPN profile ...
Page 72: ...72 5 Click Connect to a workplace and click Use my internet connection VPN ...
Page 86: ...86 3 Click on the sign on the bottom left 4 Select the VPN interface ...
Page 91: ...91 3 Click on VPN 4 click on Add VPN Configuration ...
Page 93: ...93 4 Set the Switch to ON to connect to the VPN Network ...
Page 96: ...96 4 Click on the VPN network you have just created to connect ...
Page 115: ...115 Or click License to renew your subscription ...
Page 124: ...124 ...
Page 125: ...125 ...
















































