SIEMENS 5930/5935 Business Gateway
User’s Guide
Chapter 4 User Setup
User Management
SIEMENS
33
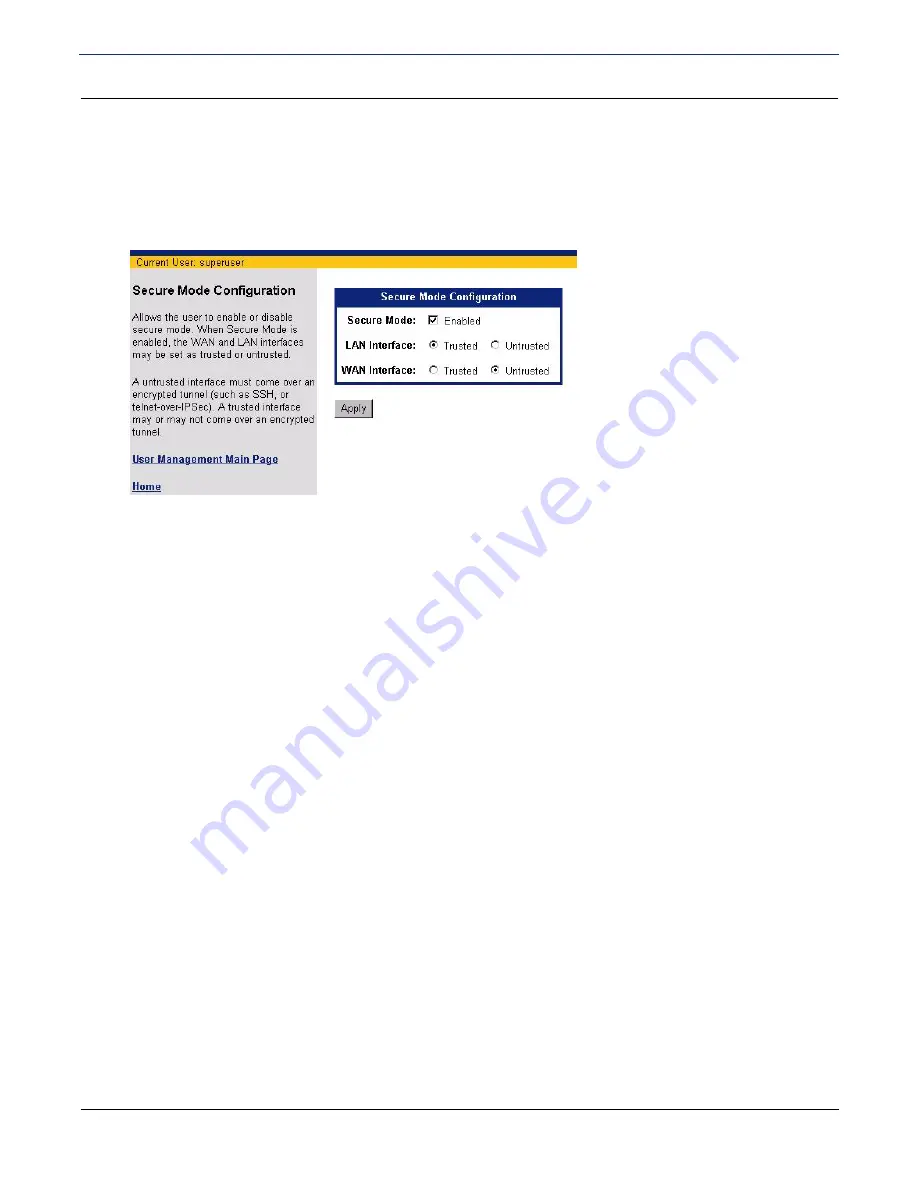
Secure Mode Configuration
You can enable secure mode to control whether an interface is trusted or untrusted. To configure Secure
Mode:
1. Click
Secure Mode Configuration
on the left navigation pane of the User Management page. This
displays the Secure Mode Configuration page.
2. Do one of the following for
Secure Mode
:
•
Click the box next to
Enabled
so a check mark appears. This enables secure mode.
•
Click the box next to
Enabled
so there is no check mark. This disables secure mode.
3. If you enabled secure mode, select one of the following for
LAN Interface
and
WAN Interface
:
•
Trusted
:
A trusted interface does not have to come over an encrypted tunnel.
•
Untrusted
:
An untrusted interface must come over an encrypted tunnel, such as SSH or telnet-over-IPSec.






























