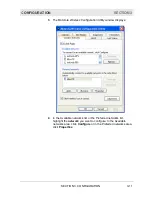
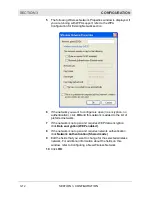
Reviews:
No comments
Related manuals for WPCI180G

ATMLINK 155 PCI
Brand: 3Com Pages: 130

WinFast 4Xsound
Brand: Leadtek Pages: 29

MIMO PCI 2614
Brand: Ansel Pages: 41

PCI-1751U
Brand: Advantech Pages: 38

Radeon X1300PCI
Brand: Diamond Multimedia Pages: 1

RX9600PRO-TD128
Brand: MSI Pages: 2

FZ-VSC402 Series
Brand: Panasonic Pages: 8

FZ-VSC401 Series
Brand: Panasonic Pages: 8

OME-PCI-1602
Brand: Omega Pages: 66

A230
Brand: Kyungwoo Pages: 7

RF30
Brand: NESS ID TECK Pages: 8

PMC-DVI
Brand: ESD electronic Pages: 16

MPG001
Brand: Connect Tech Pages: 16

A1452
Brand: EEG Pages: 15

SW1000XG
Brand: Yamaha Pages: 83

DK175VC
Brand: Deekec Pages: 3

WBT-1200 Series
Brand: WBE Pages: 7

101974
Brand: Manhattan Pages: 2