Backup Data
There are 3 configuration modes for data backup which are Auto Backup, Manual Backup and FTP
Backup.
Auto Backup
Auto Backup will automatically backup the reconstructed data files (DBtag files) into ISO file. It
contains 3 sections: Scheduling, Selection of Backup Modules and Notification.
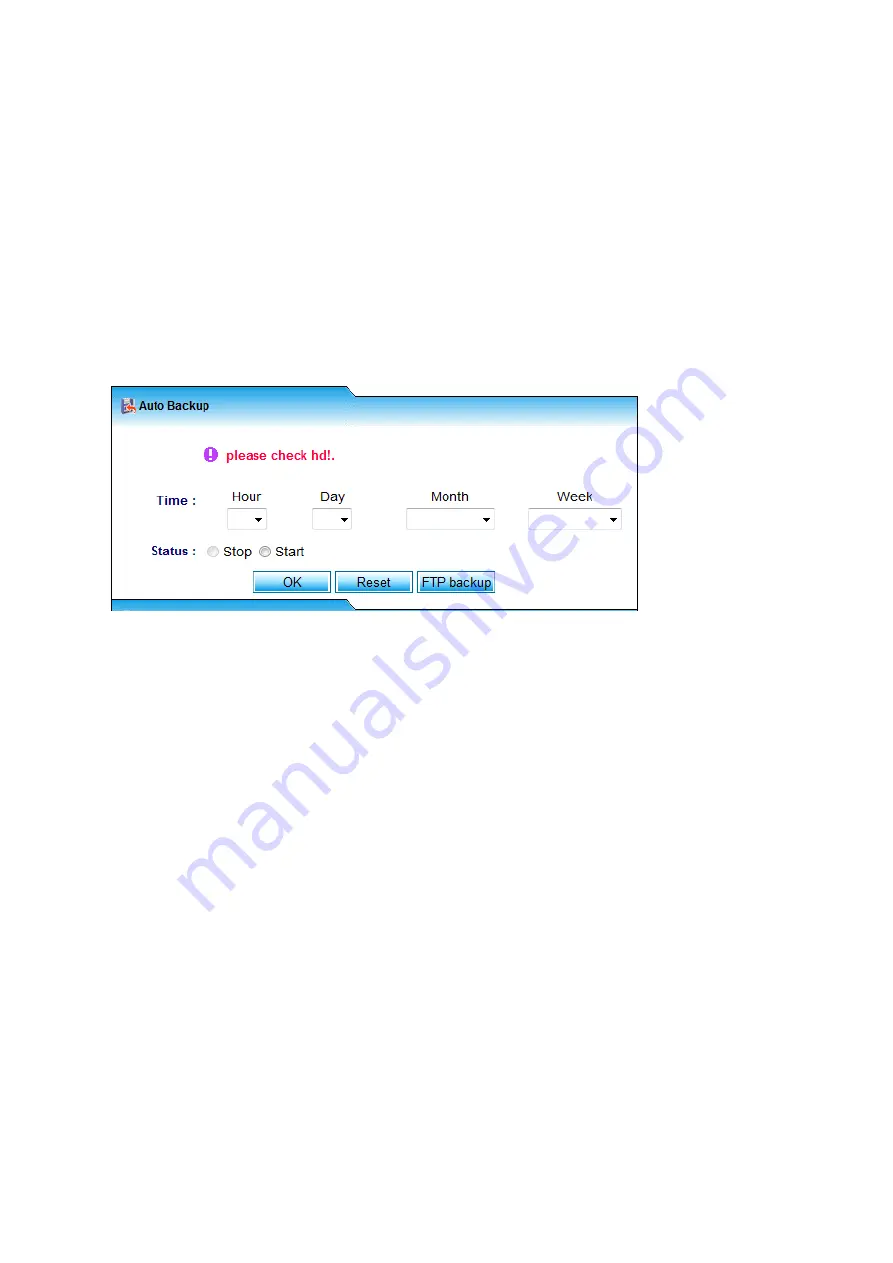
Auto Backup – Schedule
On this section, the Administrator can setup the schedule to enable the system to start the backup
process automatically at pre-defined date-time. It allows the Administrator to schedule the auto
backup by hour (0-24 Hour of the Day), day (1-31 Day of the Month), week (Sunday-Saturday) and
month (January-December). It also allows the Administrator to upload this auto backup reconstructed
data to FTP server for storage.
Summary of Contents for ICI-1000
Page 1: ...Internet Content Inspector ICI 1000 ICI 2000 User Manual v1 00...
Page 20: ...Besides generating report by IP Administrator can also generate report by Account basis...
Page 38: ...4 Click on Play to play back the record MSN webcam session...
Page 58: ...Source Code When click on the following UI will pop up to display the source code of webpage...
Page 63: ...Sample HTTP Upload Download...
Page 65: ...Sample HTTP Video Stream...
Page 67: ...Sample HTTP Request Content...
Page 159: ...Step 2 Click Show Chart...






























