Chapter 17
Advanced security features
220
Note:
1.
If a user who is allowed to use
P2P
networks (see chapter
) is connected to the fire-
wall from a certain host, no
P2P
restrictions are applied to this host. Settings in the
P2P
Eliminator
tab are always applied to unauthorized users.
2.
Information about
P2P
detection and blocked traffic can be viewed in the
Status
→
Hosts /
users
section (for details, refer to chapter
).
3.
If you wish to notify also another person when a
P2P
network is detected (e.g. the
WinRoute
administrator), define the alert on the
Alerts Settings
tab of the
Configuration
→
Account-
ing
section. For details, see chapter
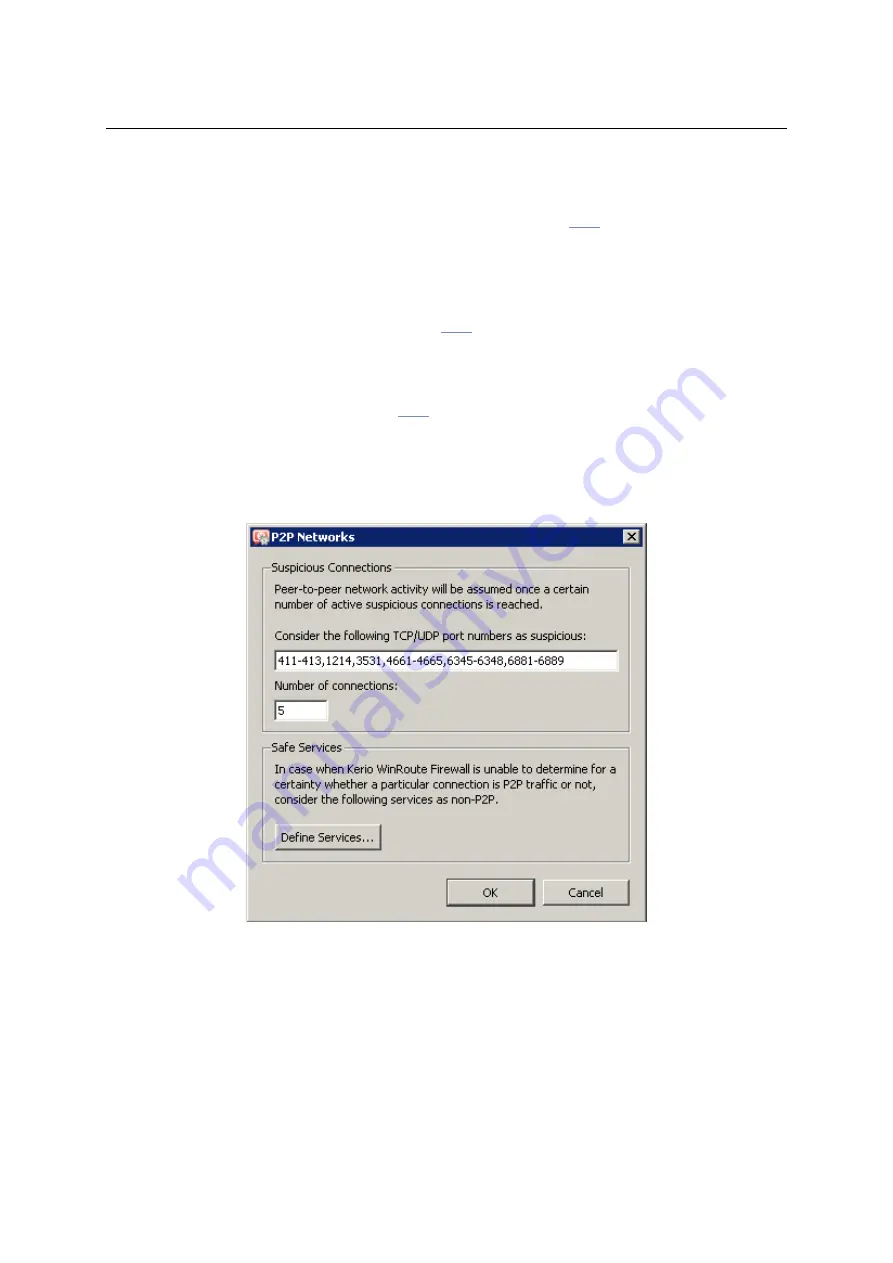
Parameters for detection of P2P networks
Click
Advanced
to set parameters for
P2P
detection.
Figure 17.3
Settings of P2P networks detection
Ports of P2P networks
List of ports which are exclusively used by
P2P
networks. These ports are usually ports for
control connections — ports (port ranges) for data sharing can be set by users themselves.
Ports in the list can be defined by port numbers or by port ranges. Individual values are
separated by commas while dash is used for definition of ranges.
Summary of Contents for KERIO WINROUTE FIREWALL 6
Page 1: ...Kerio WinRoute Firewall 6 Administrator s Guide Kerio Technologies s r o...
Page 157: ...12 3 Content Rating System Kerio Web Filter 157 Figure 12 7 Kerio Web Filter rule...
Page 247: ...19 4 Alerts 247 Figure 19 14 Details of a selected event...
Page 330: ...Chapter 23 Kerio VPN 330 Figure 23 55 The Paris filial office VPN server configuration...
Page 368: ...368...
















































