Chapter 11
Web Interface
144
SSL Certificate for the Web Interface
The principle of an encrypted
WinRoute
Web interface is based on the fact that all communi-
cation between the client and server is encrypted to protect it from wiretapping and misuse
of the transmitted data. The SSL protocol uses an asymmetric encryption first to facilitate
exchange of the symmetric encryption key which will be later used to encrypt the transmitted
data.
The asymmetric cipher uses two keys: a public one for encrypting and a private one for de-
crypting. As their names suggest, the public (encrypting) key is available to anyone wishing to
establish a connection with the server, whereas the private (decrypting) key is available only
to the server and must remain secret. The client, however, also needs to be able to identify
the server (to find out if it is truly the server and not an impostor). For this purpose there is
a certificate, which contains the public server key, the server name, expiration date and other
details. To ensure the authenticity of the certificate it must be certified and signed by a third
party, the certification authority.
Communication between the client and server then follows this scheme: the client generates
a symmetric encryption key for and encrypts it with the public server key (obtained from the
server certificate). The server decrypts it with its private key (kept solely by the server). Thus
the symmetric key is known only to the server and client. This key is then used for encryption
and decipher any other traffic.
Generate or Import Certificate
During
WinRoute
installation, a testing certificate for the SSL-secured Web interface is created
automatically (it is stored in the
sslcert
subdirectory under the
WinRoute’s
installation di-
rectory, in the
server.crt
file; the private key for the certificate is saved as
server.key
).
The certificate created is unique. However, it is issued against a non-existing server name and
it is not issued by a trustworthy certificate authority. This certificate is intended to ensure
functionality of the secured Web interface (usually for testing purposes) until a new certificate
is created or a certificate issued by a public certificate authority is imported.
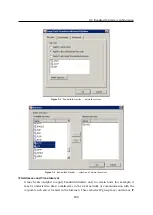
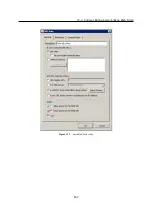
Click on the
Change SSL certificate
(in the dialog for advanced settings for the Web interface)
to view the dialog with the current server certificate. By selecting the
Field
(certificate en-
try) option you can view information either about the certificate issuer or about the subject
represented by your server.
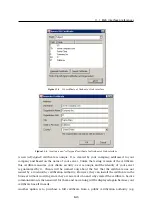
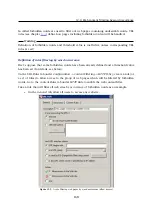
You can obtain your own certificate, which verifies your server’s identity, by two means.
You can create your own self-signed certificate. Click
Generate Certificate
in the dialog where
current server status is displayed. Insert required data about the server and your company
into the dialog entries. Only entries marked with an asterisk (
*
) are required.
Click on the
OK
button to view the
Server SSL certificate
dialog. The certificate will be started
automatically (you will not need to restart your operating system). When created, the certifi-
cate is saved as
server.crt
and the corresponding private key as
server.key
.
Summary of Contents for KERIO WINROUTE FIREWALL 6
Page 1: ...Kerio WinRoute Firewall 6 Administrator s Guide Kerio Technologies s r o...
Page 157: ...12 3 Content Rating System Kerio Web Filter 157 Figure 12 7 Kerio Web Filter rule...
Page 247: ...19 4 Alerts 247 Figure 19 14 Details of a selected event...
Page 330: ...Chapter 23 Kerio VPN 330 Figure 23 55 The Paris filial office VPN server configuration...
Page 368: ...368...