117
Password authentication enabled Stelnet server
configuration example
Network requirements
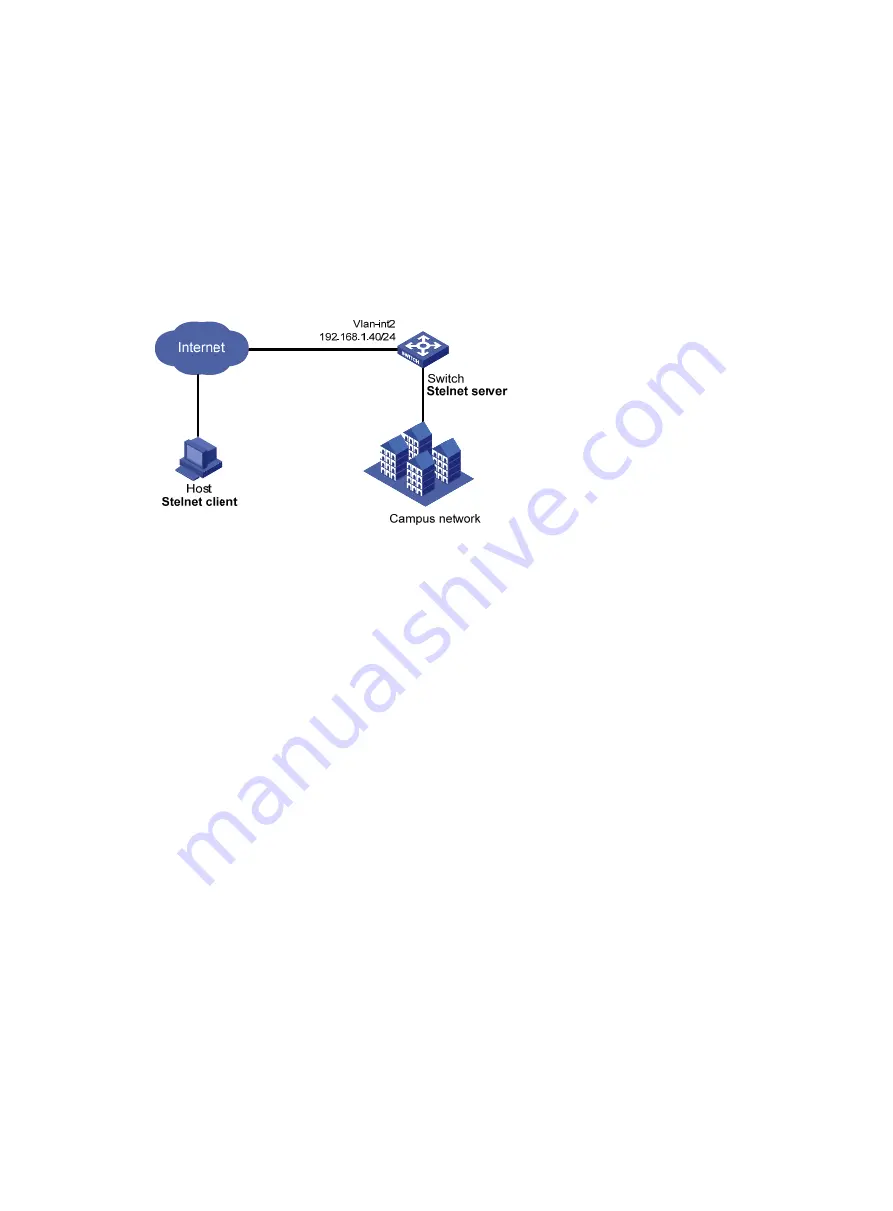
As shown in
, the switch acts as the Stelnet server and uses password authentication. The
username (
client
) and password (
aabbcc
) of the client are saved on the switch.
Establish an Stelnet connection between the host and the switch, so the client can log in to the switch
to configure and manage the switch as a network administrator.
Figure 37 Network diagram
Configuration procedure
1.
Configure the Stelnet server to generate RSA, DSA, and ECDSA key pairs:
From the navigation tree, select
Resources
>
Public key
>
Public key
.
2.
Configure the Stelnet server feature:
a.
From the navigation tree, select
Network
>
Service
>
SSH
.
b.
Enable the Stelnet service.
3.
Configure the VLAN and VLAN interface:
a.
From the navigation tree, select
Network
>
Links
>
VLAN
.
b.
Create VLAN 2.
c.
Add port GigabitEthernet 1/0/2 to the untagged port list of VLAN 2.
d.
Create VLAN-interface 2 and configure its IP address as 192.168.1.40/24.
4.
Configure the Stelnet client login authentication method as
scheme
:
a.
Log in to the switch through the console port.
b.
Configure the Stelnet client login authentication method as
scheme
.
5.
Configure the administrator account:
a.
From the navigation tree, select
Device
>
Maintenance
>
Administrators
.
b.
Add an administrator account.
c.
Configure the username as
client
and password as
aabbcc
.
d.
Select the user role as
network-admin
.
e.
Specify the available service as
SSH
.
Verifying the configuration
There are different types of Stelnet client software, such as PuTTY and OpenSSH. This example
uses an Stelnet client that runs PuTTY version 0.58.
















































