Visibility of backed up data
Backing up data means creating a new copy. Therefore, when you deal with
confidential information, it is important to restrict access to both the original data
and to the backup copy itself.
Hiding data from other users
When configuring a backup, you can decide whether during a restore the data is
visible to everyone (public) or only to the owner of the backup (private). For more
information about backup owners, see “
What is backup ownership?
” on page 78.
Data encryption
Open systems and public networking make data security in large enterprises essential.
Data Protector lets you encrypt backed-up data so that it becomes protected from
others. Data Protector offers two data encryption techniques: software-based and
drive-based.
Data Protector software encryption, referred to as
AES 256-bit encryption
, is based
on the AES-CTR (Advanced Encryption Standard in Counter Mode) encryption
algorithm that uses random keys of 256-bit length. The same key is used for both
encryption and decryption. With AES 256-bit encryption, data is encrypted before
it is transferred over a network and before it is written to media.
Data Protector
drive-based encryption
uses the encryption functionality of the drive.
The actual implementation and encryption strength depend on the drive's firmware.
Data Protector only turns on the feature and manages encryption keys.
The key management functionality is provided by the
Key Management Server (KMS)
,
which is located on the Cell Manager. All encryption keys are stored centrally in the
key store file on the Cell Manager and administered by the KMS.
You can encrypt all or selected objects in a backup specification and also combine
encrypted and unencrypted sessions on the same medium.
In addition to the encryption functionality, Data Protector also offers the encoding
functionality that uses a keyless, built-in algorithm for this purpose.
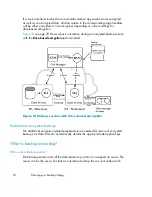
How Data Protector AES 256-bit encryption works
The Backup Session Manager (BSM) reads the backup specification in which the
AES
256-bit
encryption option is selected and requests an active encryption key from the
Key Management Server (KMS). The key is transferred to the Disk Agent (DA), which
Planning your backup strategy
76
Summary of Contents for B6960-96035
Page 17: ...Overview of backup and automated media copy sessions 340 105 Concepts guide 17 ...
Page 20: ...20 ...
Page 22: ...Publication history 22 ...
Page 132: ...Planning your backup strategy 132 ...
Page 182: ...Media management and devices 182 ...
Page 186: ...Users and user groups 186 ...
Page 204: ...The Data Protector internal database 204 ...
Page 218: ...Figure 62 Direct SIP integration example Service management 218 ...
Page 242: ...Integration with database applications 242 ...
Page 264: ...Synthetic backup 264 ...
Page 274: ...Split mirror concepts 274 ...
Page 288: ...Snapshot concepts 288 ...
Page 344: ...Further information 344 ...
Page 402: ...Glossary 402 ...