Chapter 4. Security Capabilities
18
PACSystems PROFINET IO Devices Secure Deployment Guide
GFK-2904D
Physical Security Perimeter Protection
1)
All ICS hardware should be placed in locked cabinets, with policies and procedures to restrict access
to the key.
2)
Network equipment such as switches, routers, firewalls, and Ethernet cabling should be physically
protected in locked enclosures such as cabinets or closets with policies and procedures to restrict
access to these enclosures.
3)
Whenever possible, there should be no physical network path from an ICS network to the Internet. It
should not be possible for an attacker to reach an ICS network from any Internet-facing computer.
4)
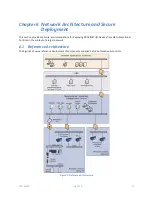
Networks should always be physically segmented as suggested in the Reference Network Architecture
diagram (Figure 1) to avoid exposure to ICS networks.
5)
Each ICS system asset should be visibly labeled by a unique identifier, with all expected asset
identification compiled into an access controlled list.
Electronic Security Perimeter Protection
1)
All external access to an ICS network should be managed through a Virtual Private Network (VPN) or
similar technology leveraging two-factor authentication.
2)
Next-Generation Firewalls should be properly configured and deployed at each conduit between
physical networks that deny all but the specifically allowed protocol families, source addresses, and
destination addresses, and specific application-level commands between the two adjacent networks.
For example, a Next-Generation Firewall could prohibit write operations across networks while
allowing read operations.
3)
If one network node such as a PLC or HMI uses unauthenticated protocols to exchange information or
commands with another network node on the same physical network, a Next-Generation Firewall
could be deployed between the two network nodes. This Next-Generation Firewall should be
configured to explicitly whitelist all expected messages between the two network nodes, and deny all
other unexpected messages.
4)
To detect and alert for unexpected, unauthenticated messages on a given network, an Intrusion
Detection System (IDS) could be configured and deployed. Consider configuring the IDS to log all
events to a Security Information and Event Management (SIEM) system that aggregates all security
information on the ICS network.
5)
To detect and actively prevent unexpected, unauthenticated messages on a given network from
reaching a given network node, an Intrusion Prevention System (IPS) could be configured and
deployed. Consider configuring the IPS to log all events to a Security Information and Event
Management (SIEM) system that aggregates all security information on the ICS network.
6)
To limit the impact of the compromise of any single user account, it is recommended to divide
administrator privileges into several user accounts, each for its own operational function.
7)
To limit the impact of the compromise of any single set of credentials (user name, password) for any
ICS equipment, it is recommended to never re-use credentials for different tools or purposes.
8)
Carefully protect sources of and access to credentials (user names, passwords) for all ICS equipment,
including switches, routers, firewalls, IDS, IPS, etc.
9)
Enforce a policy of rotating credentials for ICS equipment periodically and after personnel changes.
Note that products with no support for enforcement of unique passwords over time should be
compensated for with policies and procedures that require a history of unique passwords.
Recommendations on password complexity and management can be found in NIST 800-118,
Guide to
Enterprise Password Management
.
Summary of Contents for PACSystems* RX3i
Page 6: ...Contents GFK 2904D July 2018 iii Table of Figures Figure 1 Reference Architecture 23...
Page 7: ......
Page 11: ......
Page 21: ......
Page 33: ......