11
4.1.2.1 Type of scan
Two types of On-demand computer scans are
available.
Smart scan
quickly scans the system with
no need for further configuration of the scan
parameters.
Custom scan
allows you to select any of
the predefined scan profiles, as well as choose specific
scan targets.
4.1.2.1.1 Smart scan
Smart scan allows you to quickly launch a computer
scan and clean infected files with no need for user
intervention. Its main advantages are easy operation
with no detailed scanning configuration. Smart scan
checks all files in all folders and automatically cleans or
deletes detected infiltrations. The cleaning level is
automatically set to the default value. For more
detailed information on types of cleaning, see the
section on
Cleaning
.
4.1.2.1.2 Custom scan
Custom scan
is optimal if you would like to specify
scanning parameters such as scan targets and
scanning methods. The advantage of running a
Custom scan is the ability to configure the parameters
in detail. Different configurations can be saved as user-
defined scan profiles, which can be useful if scanning is
repeatedly performed with the same parameters.
To select scan targets, select
Computer scan
>
Custom scan
and select specific
Scan Targets
from
the tree structure. A scan target can also be more
precisely specified by entering the path to the folder or
file(s) you wish to include. If you are only interested in
scanning the system without additional cleaning
actions, select the
Scan without cleaning
option.
Furthermore, you can choose from three cleaning
levels by clicking
Setup...
>
Cleaning
.
Performing computer scans with Custom scan is
recommended for advanced users with previous
experience using antivirus programs.
4.1.2.2 Scan targets
The Scan targets tree structure allows you to select
files and folders to be scanned for viruses. Folders may
also be selected according to a profile's settings.
A scan target can be more precisely defined by
entering the path to the folder or file(s) you wish to
include in scanning. Select targets from the tree
structure that lists all available folders on the
computer.
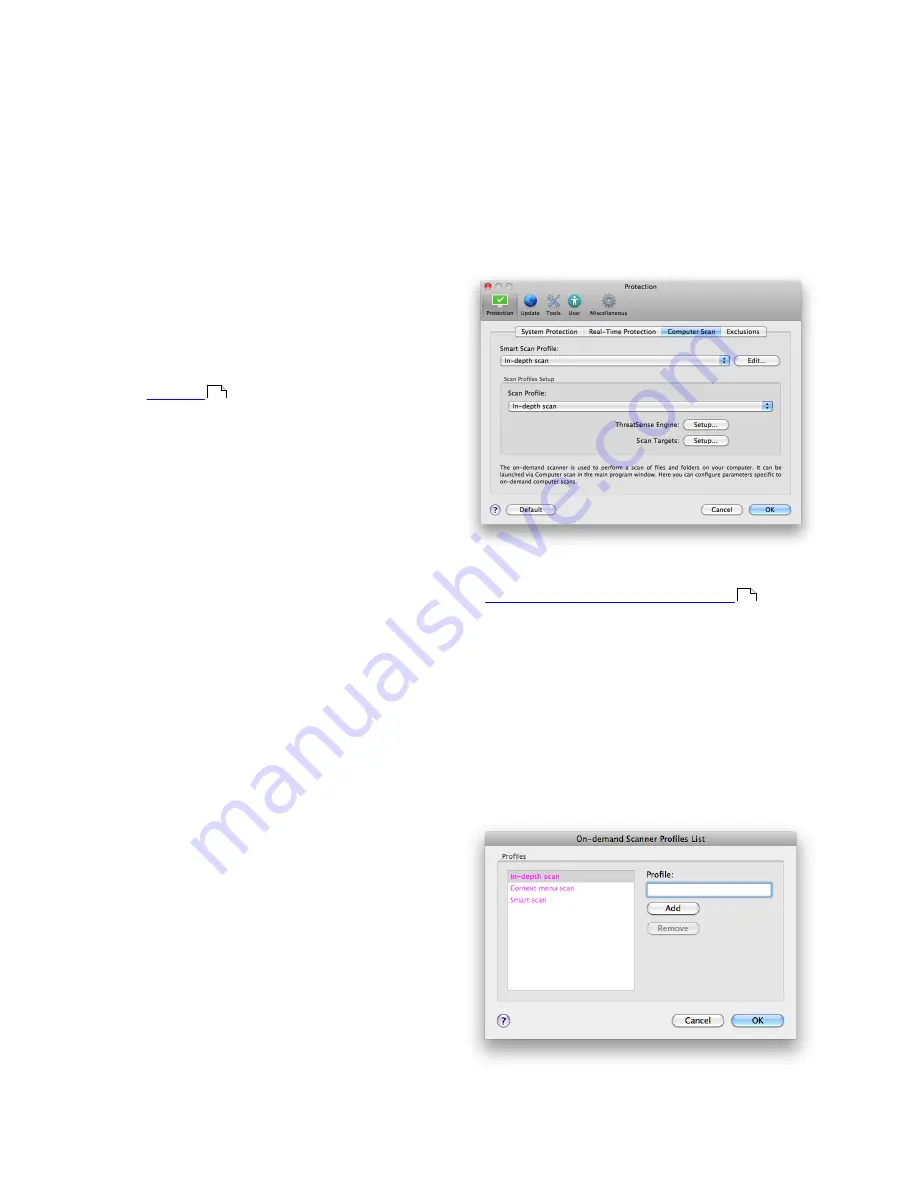
4.1.2.3 Scan profiles
Your preferred scan settings can be saved for future
scanning. We recommend that you create a different
profile (with various scan targets, scan methods and
other parameters) for each regularly used scan.
To create a new profile, go to
Setup
>
Enter
application preferences ...
>
Protection
>
Computer
Scan
and click
Edit...
next to the list of current
profiles.
To help you create a scan profile to fit your needs, see
the
ThreatSense engine parameters setup
section
for a description of each parameter of the scan setup.
Example: Suppose that you want to create your own
scan profile and the Smart scan configuration is
partially suitable, but you do not want to scan runtime
packers or potentially unsafe applications and you also
want to apply Strict cleaning. In the
On-demand
Scanner Profiles List
window, write the profile name,
click the
Add
button and confirm by
OK
. Then adjust
the parameters to meet your requirements by setting
ThreatSense Engine
and
Scan Targets
.
13
12









































