xStack® DGS-3620 Series Managed Switch Web UI Reference Guide
220
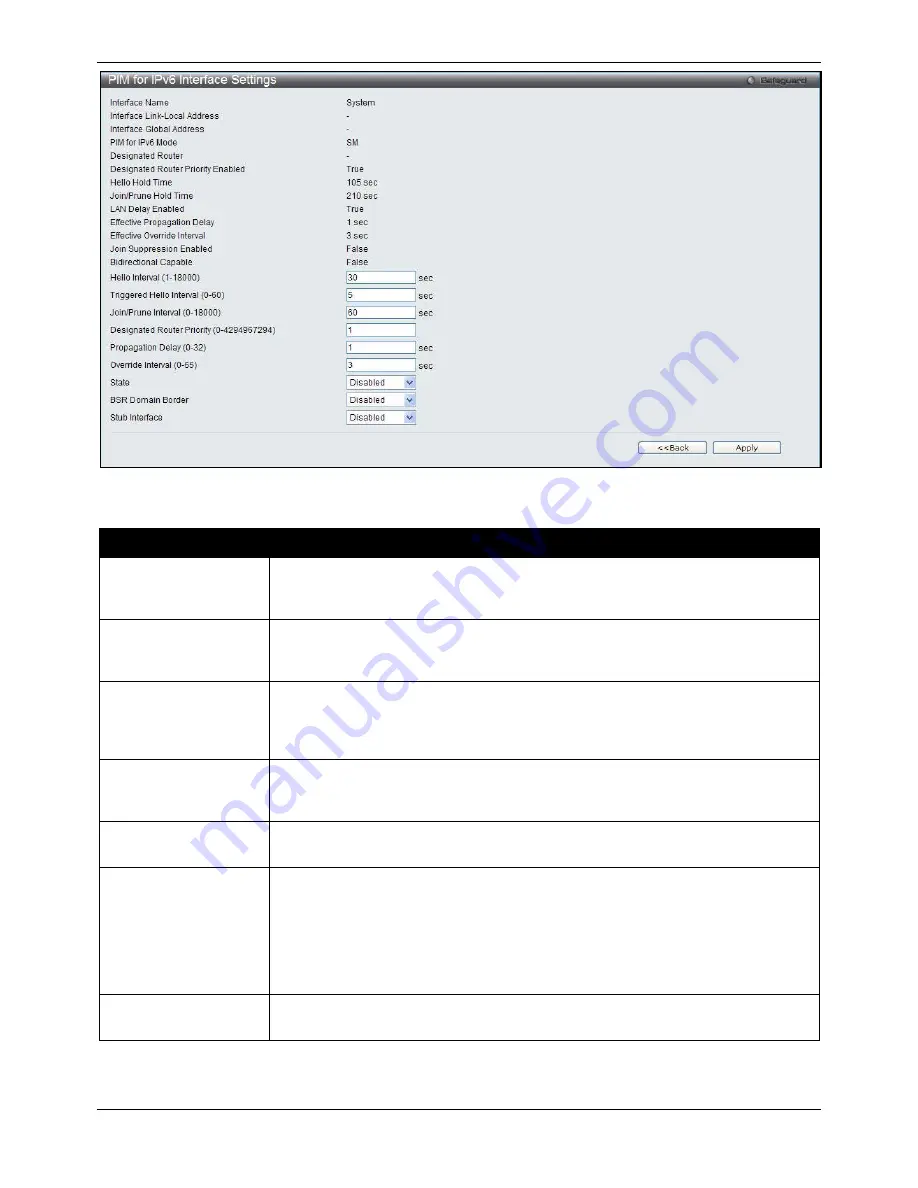
Figure 5-94 PIM for IPv6 Interface Settings – Edit window
The fields that can be configured are described below:
Parameter
Description
Hello Interval (1-18000)
Enter the time between issuing hello packets to find neighboring routers. A value of
zero represents an ‘infinite’ interval, and indicates that periodic PIM for IPv6 Hello
message should not be sent on this interface.
Triggered Hello
Interval (0-60)
Enter the maximum time before the router sends a triggered PIM Hello message on
the specified interface. A value of zero has no special meaning and indicates that
triggered PIM for IPv6 Hello message should always be sent immediately.
Join/Prune Interval
(1-18000)
Enter the frequency at which this router sends PIM for IPv6 Join/Prune messages on
this PIM for IPv6 interface. A value of zero represents an ‘infinite’ interval, and
indicates that periodic PIM for IPv6 Join/Prune messages should not be sent on this
interface.
Designated Router
Priority (0-4294967294)
Enter the Designated Router Priority value inserted into the DR Priority option in PIM
for IPv6 Hello message transmitted on this interface. Numerically higher values for
this parameter indicate higher priorities.
Propagation Delay (0-
32)
Enter the expected propagation delay between the PIM for IPv6 routers on this
network or link.
Override Interval (0-65)
Enter a value that this router inserts into the Override_Interval field of the LAN Prune
Delay option in the PIM for IPv6 Hello messages it sends on this interface. When
overriding a prune, PIM for IPv6 routers pick random time duration up to the value of
this object. The more PIM for IPv6 routers that are active on a network, the more
likely it is that the prune will be overridden after a small proportion of this time has
elapsed. The more PIM for IPv6 routers are active on this network, the larger this
object should be to obtain an optimal spread of prune override latencies.
State
Use the drop-down menu to enable or disable the PIM for IPv6 for the above IPv6
interface. By default, the PIM for IPv6 protocol state is disabled on an interface.
Summary of Contents for DGS-3620-28PC-SI
Page 1: ......






























