18
Chapter 3: Setting up and Connecting the USB Network Adapter
Setting Up the Adapter
Wireless-G PCI Adapter
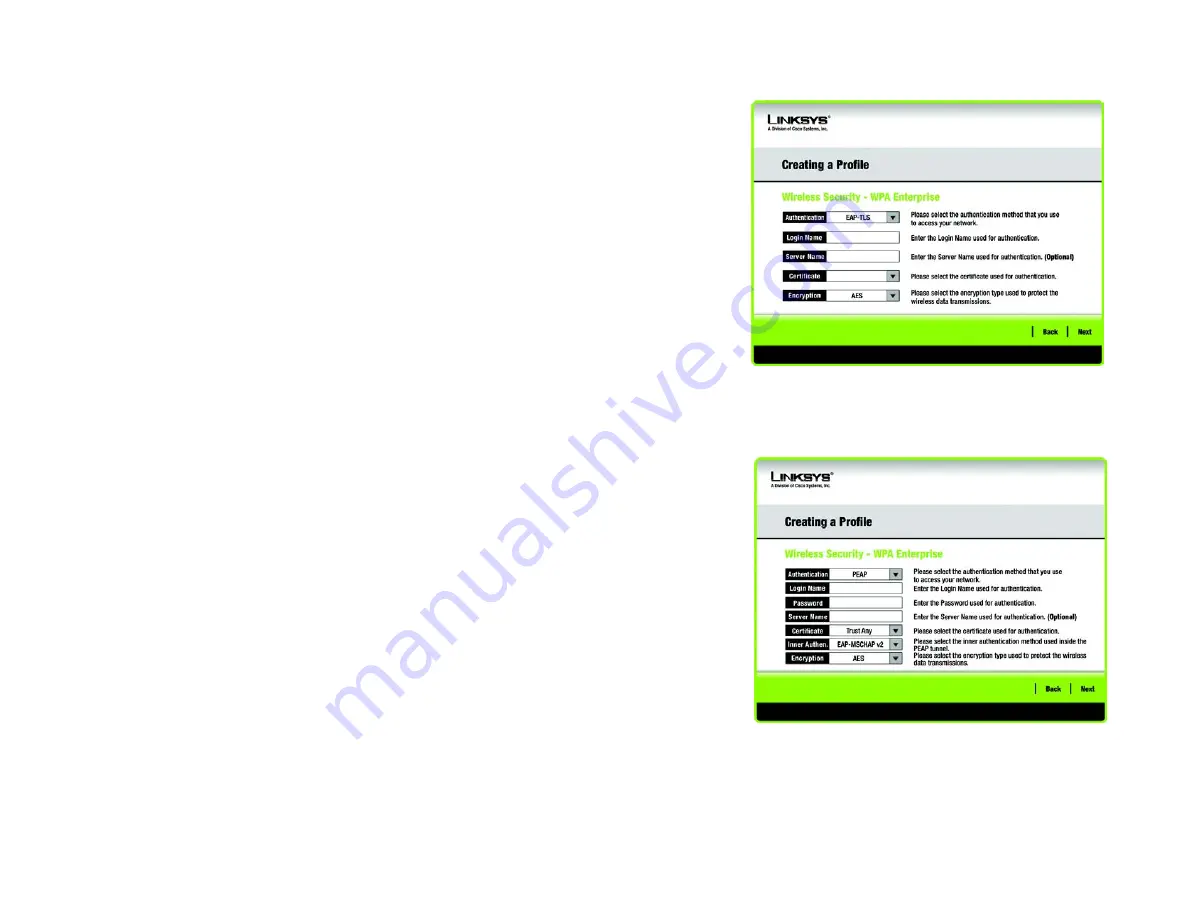
WPA Enterprise
WPA Enterprise features WPA security used in coordination with a RADIUS server. (This should only be used
when a RADIUS server is connected to the Router.) WPA Enterprise offers two authentication methods, EAP-
TLS and PEAP, as well as two encryption methods, TKIP and AES, with dynamic encryption keys.
Authentication
- Select the authentication method your network is using,
EAP-TLS
or
PEAP
.
EAP-TLS
If you selected EAP-TLS, enter the login name of your wireless network in the
Login Name
field. Enter the
name of the authentication server in the
Server Name
field (this is optional). From the
Certificate
drop-down
menu, select the certificate you have installed to authenticate you on your wireless network. Select the type
of encryption,
TKIP
or
AES
,
from the
Encryption
drop-down menu.
Click the
Next
button to continue or the
Back
button to return to the previous screen.
PEAP
If you selected PEAP, enter the login name of your wireless network in the
Login Name
field. Enter the
password of your wireless network in the
Password
field. Enter the name of the authentication server in the
Server Name
field (this is optional). From the
Certificate
drop-down menu, select the certificate you have
installed to authenticate you on your wireless network; if you want to use any certificate, keep the default
setting,
Trust Any
. Then select the authentication method (Inner Authen.) used inside the PEAP tunnel. Select
from
EAP-MSCHAP
v2
. Then, select the type of encryption,
TKIP
or
AES
,
from the
Encryption
drop-down
menu.
Click the
Next
button to continue or the
Back
button to return to the previous screen.
Figure 3-25: Wireless Security - WPA Enterprise - PEAP
Figure 3-24: Wireless Security - WPA Enterprise -
EAP-TLS






























