C H A P T E R
12-1
Cisco ASA Series Firewall CLI Configuration Guide
12
Getting Started with Application Layer Protocol
Inspection
The following topics describe how to configure application layer protocol inspection.
•
Application Layer Protocol Inspection, page 12-1
•
Guidelines for Application Inspection, page 12-5
•
Defaults for Application Inspection, page 12-6
•
Configure Application Layer Protocol Inspection, page 12-9
•
Configure Regular Expressions, page 12-15
•
History for Application Inspection, page 12-18
Application Layer Protocol Inspection
Inspection engines are required for services that embed IP addressing information in the user data packet
or that open secondary channels on dynamically assigned ports. These protocols require the ASA to do
a deep packet inspection instead of passing the packet through the fast path (see the general operations
configuration guide for more information about the fast path). As a result, inspection engines can affect
overall throughput. Several common inspection engines are enabled on the ASA by default, but you
might need to enable others depending on your network.
The following topics explain application inspection in more detail.
•
How Inspection Engines Work, page 12-1
•
When to Use Application Protocol Inspection, page 12-2
•
Inspection Policy Maps, page 12-3
How Inspection Engines Work
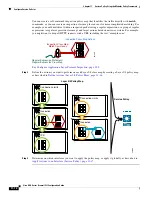
As illustrated in the following figure, the ASA uses three databases for its basic operation:
•
ACLs—Used for authentication and authorization of connections based on specific networks, hosts,
and services (TCP/UDP port numbers).
•
Inspections—Contains a static, predefined set of application-level inspection functions.
Summary of Contents for ASA 5508-X
Page 11: ...P A R T 1 Access Control ...
Page 12: ......
Page 157: ...P A R T 2 Network Address Translation ...
Page 158: ......
Page 233: ...P A R T 3 Service Policies and Application Inspection ...
Page 234: ......
Page 379: ...P A R T 4 Connection Management and Threat Detection ...
Page 380: ......