11-18
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 11 Service Policy Using the Modular Policy Framework
Monitoring Service Policies
Examples
For example, the following command enables the inbound_policy policy map on the outside interface:
hostname(config)#
service-policy inbound_policy interface outside
The following commands disable the default global policy, and enables a new one called
new_global_policy.
hostname(config)#
no service-policy global_policy global
hostname(config)#
service-policy new_global_policy global
Monitoring Service Policies
To monitor service policies, enter the following command:
•
show service-policy
Displays the service policy statistics.
Examples for Service Policies (Modular Policy Framework)
This section includes several Modular Policy Framework examples.
•
Applying Inspection and QoS Policing to HTTP Traffic, page 11-18
•
Applying Inspection to HTTP Traffic Globally, page 11-19
•
Applying Inspection and Connection Limits to HTTP Traffic to Specific Servers, page 11-19
•
Applying Inspection to HTTP Traffic with NAT, page 11-20
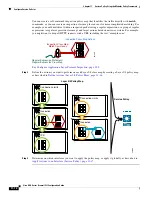
Applying Inspection and QoS Policing to HTTP Traffic
In this example, any HTTP connection (TCP traffic on port 80) that enters or exits the ASA through the
outside interface is classified for HTTP inspection. Any HTTP traffic that exits the outside interface is
classified for policing.
Figure 11-1
HTTP Inspection and QoS Policing
See the following commands for this example:
hostname(config)#
class-map http_traffic
143356
in
s
ide
port
8
0
o
u
t
s
ide
A
Ho
s
t A
Ho
s
t B
port
8
0
Security
appliance
in
s
p.
in
s
p.
police
Summary of Contents for ASA 5508-X
Page 11: ...P A R T 1 Access Control ...
Page 12: ......
Page 157: ...P A R T 2 Network Address Translation ...
Page 158: ......
Page 233: ...P A R T 3 Service Policies and Application Inspection ...
Page 234: ......
Page 379: ...P A R T 4 Connection Management and Threat Detection ...
Page 380: ......