Product information Wireless data loggers
Software
The supplied PC basic software
HD35AP-S
, downloadable free of charge from the website, allows configuring all the devic-es of the
system, viewing the connection status, the RF signal level and the battery charge level of each device, viewing the real time
measurements both graphically and numerically, data downloading.
The data can be downloaded:
-
automatically
, at regular intervals;
-
manually
, upon user request.
The data downloaded in the PC are entered in a database. The transfer of the sensor measurements in the database occurs in stages:
1. the HD35ED... data loggers transmit automatically at regular intervals the measurements to the HD35AP... base unit (which stores the
measurements in its internal memory);
2. the data in the memory of the HD35AP... base unit are downloaded in the PC, automatically or upon user request, through the HD35AP-S
software;
3. the HD35AP-S software enters the downloaded data in the database.
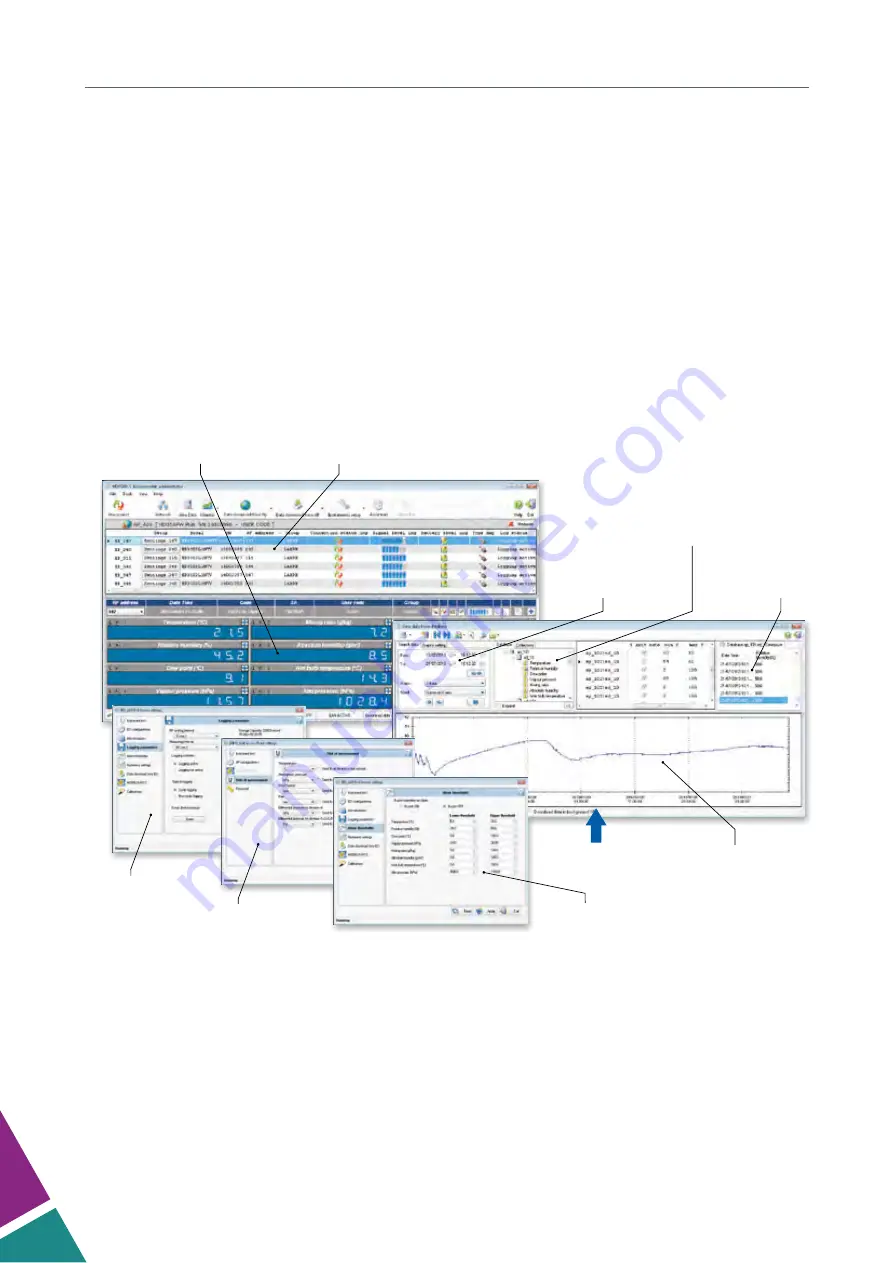
Monitor
of measurements
Information and
status
of the devices
Selection of
time interval
Selection of devices
and quantities
Graph of
measurements
Configuration of
alarm thresholds
DATABASE
Configuration of units
of measurement
Configuration of
logging parameters
Measurements
The connection to the database is
multi-client
: it is possible to store the data in a remote database on the local network to which the PC
is connected and the data can be displayed from any PC on the local network running the software HD35AP-S.
The
HD35AP-CFR21
option (working with hardware key) allows, in addition to the features of the basic software, the protection of
recorded data and configuration of the system in response to
FDA 21 CFR part 11
recommendations. In particular are available:
-
The traceability of activities (audit trail) performed with the software; for example, which users connected and what changes were
possibly made to the configuration of the system.
-
The management of users access for the system configuration and viewing of data in the database. Each user can be assigned a
different password for using the software. There are also three levels of access (Administrator, Super-user and standard User); for each
level, the allowed operations can be defined.
18