ZyWALL 5 User’s Guide
Chapter 28 LAN Setup
421
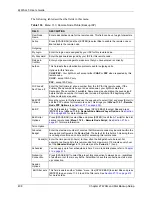
Follow the instructions in the next table on how to configure the wireless LAN parameters.
Note:
The ZyWALL LAN Ethernet and wireless ports can transparently communicate
with each other (transparent bridge).
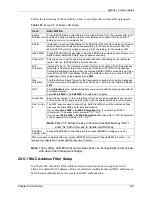
28.5.1 MAC Address Filter Setup
Your ZyWALL checks the MAC address of the wireless station device against a list of
allowed or denied MAC addresses. However, intruders could fake allowed MAC addresses so
MAC-based authentication is less secure than EAP authentication.
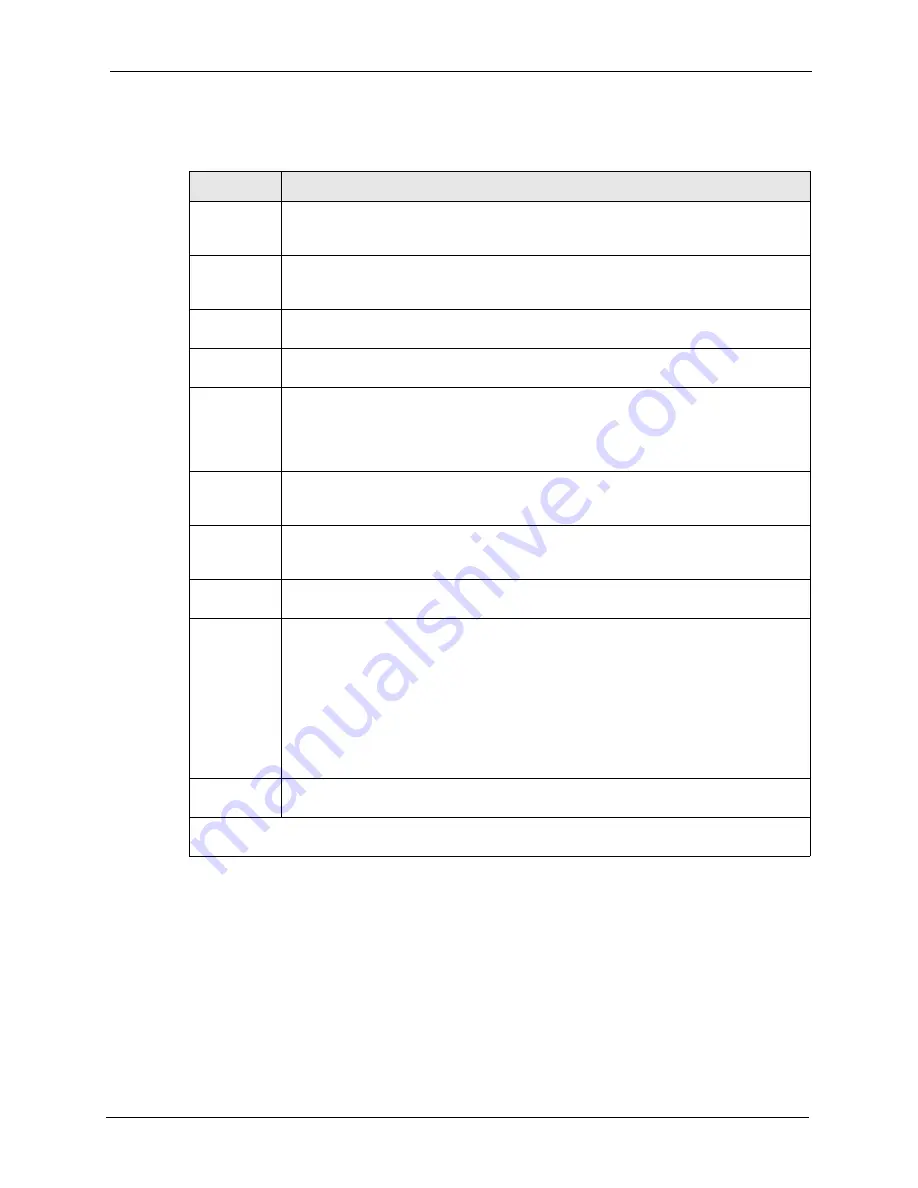
Table 163
Menu 3.5: Wireless LAN Setup
FIELD
DESCRIPTION
Enable
Wireless LAN
Press [SPACE BAR] to select
Yes
to turn on the wireless LAN. The wireless LAN is off
by default. Configure wireless LAN security features such as Mac filters and 802.1X
before you turn on the wireless LAN.
ESSID
(Extended Service Set IDentification) The ESSID identifies the AP to which the wireless
stations associate. Wireless stations associating to the Access Point must have the
same ESSID. Enter a descriptive name (up to 32 characters) for the wireless LAN.
Hide ESSID
Press [SPACE BAR] to select
Yes
to hide the ESSID in the outgoing beacon frame so a
station cannot obtain the ESSID through passive scanning.
Channel ID
This allows you to set the operating frequency/channel depending on your particular
region. Use the [SPACE BAR] to select a channel.
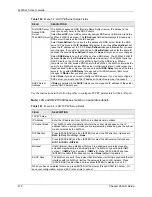
RTS
Threshold
(Request To Send) The threshold (number of bytes) for enabling RTS/CTS handshake.
Data with its frame size larger than this value will perform the RTS/CTS handshake.
Setting this attribute to be larger than the maximum MSDU (MAC service data unit) size
turns off the RTS/CTS handshake. Setting this attribute to zero turns on the RTS/CTS
handshake. Enter a value between
0
and
2432
.
Frag.
Threshold
The threshold (number of bytes) for the fragmentation boundary for directed messages.
It is the maximum data fragment size that can be sent. Enter a value between
256
and
2432
.
WEP
Select
Disable
to allow wireless stations to communicate with the access points without
any data encryption.
Select
64-bit WEP
or
128-bit WEP
to enable data encryption.
Default Key
Enter the key number (1 to 4) in this field. Only one key can be enabled at any one time.
This key must be the same on the ZyWALL and the wireless stations to communicate.
Key 1 to Key
4
The WEP keys are used to encrypt data. Both the ZyWALL and the wireless stations
must use the same WEP key for data transmission.
If you chose
64-bit WEP
in the
WEP Encryption
field, then enter any 5 ASCII
characters or 10 hexadecimal characters ("0-9", "A-F").
If you chose
128-bit WEP
in the
WEP Encryption
field, then enter 13 ASCII characters
or 26 hexadecimal characters ("0-9", "A-F").
Note:
Enter “0x” before the key to denote a hexadecimal key. Don’t
enter “0x” before the key to denote an ASCII key.
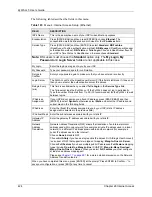
Edit MAC
Address Filter
Press [SPACE BAR] to select
Yes
and
then press [ENTER] to display menu 3.5.1.
When you have completed this menu, press [ENTER] at the prompt “Press ENTER to Confirm…” to
save your configuration, or press [ESC] at any time to cancel.
Содержание ZyXEL ZyWALL 5
Страница 1: ...ZyWALL 5 Internet Security Appliance User s Guide Version 3 64 3 2005 ...
Страница 2: ......
Страница 26: ...ZyWALL 5 User s Guide 24 ...
Страница 44: ...ZyWALL 5 User s Guide 42 ...
Страница 86: ...ZyWALL 5 User s Guide 84 Chapter 3 Wizard Setup ...
Страница 96: ...ZyWALL 5 User s Guide 94 Chapter 4 LAN Screens ...
Страница 102: ...ZyWALL 5 User s Guide 100 Chapter 5 Bridge Screens ...
Страница 130: ...ZyWALL 5 User s Guide 128 Chapter 7 WAN Screens Figure 45 WAN PPPoE Encapsulation ...
Страница 138: ...ZyWALL 5 User s Guide 136 Chapter 7 WAN Screens Figure 50 Dial Backup Setup ...
Страница 144: ...ZyWALL 5 User s Guide 142 Chapter 7 WAN Screens ...
Страница 152: ...ZyWALL 5 User s Guide 150 Chapter 8 DMZ Screens ...
Страница 174: ...ZyWALL 5 User s Guide 172 Chapter 10 Firewall Screens Figure 68 Creating Editing A Firewall Rule ...
Страница 179: ...ZyWALL 5 User s Guide Chapter 10 Firewall Screens 177 Figure 73 My Service Rule Configuration ...
Страница 220: ...ZyWALL 5 User s Guide 218 Chapter 13 Introduction to IPSec ...
Страница 238: ...ZyWALL 5 User s Guide 236 Chapter 14 VPN Screens Figure 110 VPN Rules IKE Network Policy Edit ...
Страница 261: ...ZyWALL 5 User s Guide Chapter 15 Certificates 259 Figure 122 My Certificate Details ...
Страница 280: ...ZyWALL 5 User s Guide 278 Chapter 16 Authentication Server Figure 133 Local User Database ...
Страница 317: ...ZyWALL 5 User s Guide Chapter 19 Bandwidth Management 315 ...
Страница 318: ...ZyWALL 5 User s Guide 316 Chapter 19 Bandwidth Management ...
Страница 352: ...ZyWALL 5 User s Guide 350 Chapter 21 Remote Management ...
Страница 366: ...ZyWALL 5 User s Guide 364 Chapter 23 Logs Screens Figure 188 Log Settings ...
Страница 389: ...ZyWALL 5 User s Guide Chapter 24 Maintenance 387 Figure 210 Restart Screen ...
Страница 390: ...ZyWALL 5 User s Guide 388 Chapter 24 Maintenance ...
Страница 416: ...ZyWALL 5 User s Guide 414 Chapter 27 WAN and Dial Backup Setup ...
Страница 432: ...ZyWALL 5 User s Guide 430 Chapter 30 DMZ Setup ...
Страница 492: ...ZyWALL 5 User s Guide 490 Chapter 37 System Information Diagnosis ...
Страница 508: ...ZyWALL 5 User s Guide 506 Chapter 38 Firmware and Configuration File Maintenance ...
Страница 520: ...ZyWALL 5 User s Guide 518 Chapter 40 Remote Management ...
Страница 536: ...ZyWALL 5 User s Guide 534 Chapter 42 Troubleshooting Figure 343 Java Sun ...
Страница 564: ...ZyWALL 5 User s Guide 562 Appendix C IP Subnetting ...
Страница 570: ...ZyWALL 5 User s Guide 568 Appendix E PPTP ...
Страница 571: ...ZyWALL 5 User s Guide 569 ...
Страница 572: ...ZyWALL 5 User s Guide 570 ...
Страница 590: ...ZyWALL 5 User s Guide 588 Appendix G Triangle Route ...
Страница 620: ...ZyWALL 5 User s Guide 618 Appendix J Importing Certificates ...
Страница 622: ...ZyWALL 5 User s Guide 620 Appendix K Command Interpreter ...
Страница 628: ...ZyWALL 5 User s Guide 626 Appendix L Firewall Commands ...
Страница 632: ...ZyWALL 5 User s Guide 630 Appendix M NetBIOS Filter Commands ...
Страница 638: ...ZyWALL 5 User s Guide 636 Appendix O Brute Force Password Guessing Protection ...
Страница 660: ...ZyWALL 5 User s Guide 658 Appendix Q Log Descriptions ...