ZyWALL 5 User’s Guide
Chapter 15 Certificates
251
C
H A P T E R
15
Certificates
This chapter gives background information about public-key certificates and explains how to
use them.
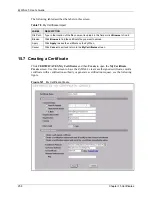
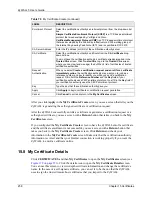
15.1 Certificates Overview
The ZyWALL can use certificates (also called digital IDs) to authenticate users. Certificates
are based on public-private key pairs. A certificate contains the certificate owner’s identity and
public key. Certificates provide a way to exchange public keys for use in authentication.
A Certification Authority (CA) issues certificates and guarantees the identity of each
certificate owner. There are commercial certification authorities like CyberTrust or VeriSign
and government certification authorities. You can use the ZyWALL to generate certification
requests that contain identifying information and public keys and then send the certification
requests to a certification authority.
In public-key encryption and decryption, each host has two keys. One key is public and can be
made openly available; the other key is private and must be kept secure. Public-key encryption
in general works as follows.
1
Tim wants to send a private message to Jenny. Tim generates a public key pair. What is
encrypted with one key can only be decrypted using the other.
2
Tim keeps the private key and makes the public key openly available.
3
Tim uses his private key to encrypt the message and sends it to Jenny.
4
Jenny receives the message and uses Tim’s public key to decrypt it.
5
Additionally, Jenny uses her own private key to encrypt a message and Tim uses Jenny’s
public key to decrypt the message.
The ZyWALL uses certificates based on public-key cryptology to authenticate users
attempting to establish a connection, not to encrypt the data that you send after establishing a
connection. The method used to secure the data that you send through an established
connection depends on the type of connection. For example, a VPN tunnel might use the triple
DES encryption algorithm.
The certification authority uses its private key to sign certificates. Anyone can then use the
certification authority’s public key to verify the certificates.
A certification path is the hierarchy of certification authority certificates that validate a
certificate. The ZyWALL does not trust a certificate if any certificate on its path has expired or
been revoked.
Содержание ZyXEL ZyWALL 5
Страница 1: ...ZyWALL 5 Internet Security Appliance User s Guide Version 3 64 3 2005 ...
Страница 2: ......
Страница 26: ...ZyWALL 5 User s Guide 24 ...
Страница 44: ...ZyWALL 5 User s Guide 42 ...
Страница 86: ...ZyWALL 5 User s Guide 84 Chapter 3 Wizard Setup ...
Страница 96: ...ZyWALL 5 User s Guide 94 Chapter 4 LAN Screens ...
Страница 102: ...ZyWALL 5 User s Guide 100 Chapter 5 Bridge Screens ...
Страница 130: ...ZyWALL 5 User s Guide 128 Chapter 7 WAN Screens Figure 45 WAN PPPoE Encapsulation ...
Страница 138: ...ZyWALL 5 User s Guide 136 Chapter 7 WAN Screens Figure 50 Dial Backup Setup ...
Страница 144: ...ZyWALL 5 User s Guide 142 Chapter 7 WAN Screens ...
Страница 152: ...ZyWALL 5 User s Guide 150 Chapter 8 DMZ Screens ...
Страница 174: ...ZyWALL 5 User s Guide 172 Chapter 10 Firewall Screens Figure 68 Creating Editing A Firewall Rule ...
Страница 179: ...ZyWALL 5 User s Guide Chapter 10 Firewall Screens 177 Figure 73 My Service Rule Configuration ...
Страница 220: ...ZyWALL 5 User s Guide 218 Chapter 13 Introduction to IPSec ...
Страница 238: ...ZyWALL 5 User s Guide 236 Chapter 14 VPN Screens Figure 110 VPN Rules IKE Network Policy Edit ...
Страница 261: ...ZyWALL 5 User s Guide Chapter 15 Certificates 259 Figure 122 My Certificate Details ...
Страница 280: ...ZyWALL 5 User s Guide 278 Chapter 16 Authentication Server Figure 133 Local User Database ...
Страница 317: ...ZyWALL 5 User s Guide Chapter 19 Bandwidth Management 315 ...
Страница 318: ...ZyWALL 5 User s Guide 316 Chapter 19 Bandwidth Management ...
Страница 352: ...ZyWALL 5 User s Guide 350 Chapter 21 Remote Management ...
Страница 366: ...ZyWALL 5 User s Guide 364 Chapter 23 Logs Screens Figure 188 Log Settings ...
Страница 389: ...ZyWALL 5 User s Guide Chapter 24 Maintenance 387 Figure 210 Restart Screen ...
Страница 390: ...ZyWALL 5 User s Guide 388 Chapter 24 Maintenance ...
Страница 416: ...ZyWALL 5 User s Guide 414 Chapter 27 WAN and Dial Backup Setup ...
Страница 432: ...ZyWALL 5 User s Guide 430 Chapter 30 DMZ Setup ...
Страница 492: ...ZyWALL 5 User s Guide 490 Chapter 37 System Information Diagnosis ...
Страница 508: ...ZyWALL 5 User s Guide 506 Chapter 38 Firmware and Configuration File Maintenance ...
Страница 520: ...ZyWALL 5 User s Guide 518 Chapter 40 Remote Management ...
Страница 536: ...ZyWALL 5 User s Guide 534 Chapter 42 Troubleshooting Figure 343 Java Sun ...
Страница 564: ...ZyWALL 5 User s Guide 562 Appendix C IP Subnetting ...
Страница 570: ...ZyWALL 5 User s Guide 568 Appendix E PPTP ...
Страница 571: ...ZyWALL 5 User s Guide 569 ...
Страница 572: ...ZyWALL 5 User s Guide 570 ...
Страница 590: ...ZyWALL 5 User s Guide 588 Appendix G Triangle Route ...
Страница 620: ...ZyWALL 5 User s Guide 618 Appendix J Importing Certificates ...
Страница 622: ...ZyWALL 5 User s Guide 620 Appendix K Command Interpreter ...
Страница 628: ...ZyWALL 5 User s Guide 626 Appendix L Firewall Commands ...
Страница 632: ...ZyWALL 5 User s Guide 630 Appendix M NetBIOS Filter Commands ...
Страница 638: ...ZyWALL 5 User s Guide 636 Appendix O Brute Force Password Guessing Protection ...
Страница 660: ...ZyWALL 5 User s Guide 658 Appendix Q Log Descriptions ...