ZyWALL 35 User’s Guide
Chapter 13 Introduction to IPSec
231
NAT is incompatible with the
AH
protocol in both
Transport
and
Tunnel
mode. An IPSec
VPN using the
AH
protocol digitally signs the outbound packet, both data payload and
headers, with a hash value appended to the packet. When using
AH
protocol, packet contents
(the data payload) are not encrypted.
A NAT device in between the IPSec endpoints will rewrite either the source or destination
address with one of its own choosing. The VPN device at the receiving end will verify the
integrity of the incoming packet by computing its own hash value, and complain that the hash
value appended to the received packet doesn't match. The VPN device at the receiving end
doesn't know about the NAT in the middle, so it assumes that the data has been maliciously
altered.
IPSec using
ESP
in
Tunnel
mode encapsulates the entire original packet (including headers)
in a new IP packet. The new IP packet's source address is the outbound address of the sending
VPN gateway, and its destination address is the inbound address of the VPN device at the
receiving end. When using
ESP
protocol with authentication, the packet contents (in this case,
the entire original packet) are encrypted. The encrypted contents, but not the new headers, are
signed with a hash value appended to the packet.
Tunnel
mode
ESP
with authentication is compatible with NAT because integrity checks are
performed over the combination of the "original header plus original payload," which is
unchanged by a NAT device.
Transport
mode
ESP
with authentication is not compatible with
NAT, although NAT traversal provides a way to use
Transport
mode
ESP
when there is a
NAT router between the IPSec endpoints (See
for details).
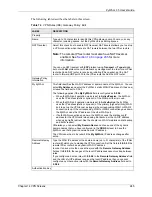
Table 67
VPN and NAT
SECURITY PROTOCOL
MODE
NAT
AH
Transport
N
AH
Tunnel
N
ESP
Transport
N
ESP
Tunnel
Y
Содержание ZyXEL ZyWALL 35
Страница 1: ...ZyWALL 35 Internet Security Appliance User s Guide Version 3 64 3 2005 ...
Страница 2: ......
Страница 38: ...ZyWALL 35 User s Guide 36 ...
Страница 46: ...ZyWALL 35 User s Guide 44 ...
Страница 74: ...ZyWALL 35 User s Guide 72 Chapter 2 Introducing the Web Configurator ...
Страница 90: ...ZyWALL 35 User s Guide 88 Chapter 3 Wizard Setup ...
Страница 100: ...ZyWALL 35 User s Guide 98 Chapter 4 LAN Screens ...
Страница 106: ...ZyWALL 35 User s Guide 104 Chapter 5 Bridge Screens ...
Страница 128: ...ZyWALL 35 User s Guide 126 Chapter 6 Wireless LAN ...
Страница 135: ...ZyWALL 35 User s Guide Chapter 7 WAN Screens 133 Figure 47 General ...
Страница 152: ...ZyWALL 35 User s Guide 150 Chapter 7 WAN Screens Figure 57 Dial Backup Setup ...
Страница 158: ...ZyWALL 35 User s Guide 156 Chapter 7 WAN Screens ...
Страница 166: ...ZyWALL 35 User s Guide 164 Chapter 8 DMZ Screens ...
Страница 188: ...ZyWALL 35 User s Guide 186 Chapter 10 Firewall Screens Figure 75 Creating Editing A Firewall Rule ...
Страница 193: ...ZyWALL 35 User s Guide Chapter 10 Firewall Screens 191 Figure 80 My Service Rule Configuration ...
Страница 234: ...ZyWALL 35 User s Guide 232 Chapter 13 Introduction to IPSec ...
Страница 246: ...ZyWALL 35 User s Guide 244 Chapter 14 VPN Screens Figure 116 VPN Rules IKE Gateway Policy Edit ...
Страница 252: ...ZyWALL 35 User s Guide 250 Chapter 14 VPN Screens Figure 117 VPN Rules IKE Network Policy Edit ...
Страница 275: ...ZyWALL 35 User s Guide Chapter 15 Certificates 273 Figure 129 My Certificate Details ...
Страница 294: ...ZyWALL 35 User s Guide 292 Chapter 16 Authentication Server Figure 140 Local User Database ...
Страница 314: ...ZyWALL 35 User s Guide 312 Chapter 17 Network Address Translation NAT ...
Страница 318: ...ZyWALL 35 User s Guide 316 Chapter 18 Static Route ...
Страница 324: ...ZyWALL 35 User s Guide 322 Chapter 19 Policy Route ...
Страница 340: ...ZyWALL 35 User s Guide 338 Chapter 20 Bandwidth Management ...
Страница 376: ...ZyWALL 35 User s Guide 374 Chapter 22 Remote Management ...
Страница 390: ...ZyWALL 35 User s Guide 388 Chapter 24 Logs Screens Figure 198 Log Settings ...
Страница 413: ...ZyWALL 35 User s Guide Chapter 25 Maintenance 411 Figure 220 Restart Screen ...
Страница 414: ...ZyWALL 35 User s Guide 412 Chapter 25 Maintenance ...
Страница 440: ...ZyWALL 35 User s Guide 438 Chapter 28 WAN and Dial Backup Setup ...
Страница 456: ...ZyWALL 35 User s Guide 454 Chapter 31 DMZ Setup ...
Страница 460: ...ZyWALL 35 User s Guide 458 Chapter 32 Route Setup ...
Страница 470: ...ZyWALL 35 User s Guide 468 Chapter 33 Remote Node Setup ...
Страница 522: ...ZyWALL 35 User s Guide 520 Chapter 39 System Information Diagnosis ...
Страница 538: ...ZyWALL 35 User s Guide 536 Chapter 40 Firmware and Configuration File Maintenance ...
Страница 550: ...ZyWALL 35 User s Guide 548 Chapter 42 Remote Management ...
Страница 558: ...ZyWALL 35 User s Guide 556 Chapter 43 IP Policy Routing ...
Страница 574: ...ZyWALL 35 User s Guide 572 Chapter 45 Troubleshooting Figure 364 Java Sun ...
Страница 602: ...ZyWALL 35 User s Guide 600 Appendix C IP Subnetting ...
Страница 608: ...ZyWALL 35 User s Guide 606 Appendix E PPTP ...
Страница 626: ...ZyWALL 35 User s Guide 624 Appendix G Triangle Route ...
Страница 656: ...ZyWALL 35 User s Guide 654 Appendix J Importing Certificates ...
Страница 658: ...ZyWALL 35 User s Guide 656 Appendix K Command Interpreter ...
Страница 664: ...ZyWALL 35 User s Guide 662 Appendix L Firewall Commands ...
Страница 668: ...ZyWALL 35 User s Guide 666 Appendix M NetBIOS Filter Commands ...
Страница 674: ...ZyWALL 35 User s Guide 672 Appendix O Brute Force Password Guessing Protection ...
Страница 696: ...ZyWALL 35 User s Guide 694 Appendix Q Log Descriptions ...