ZyWALL 35 User’s Guide
Chapter 9 Firewalls
171
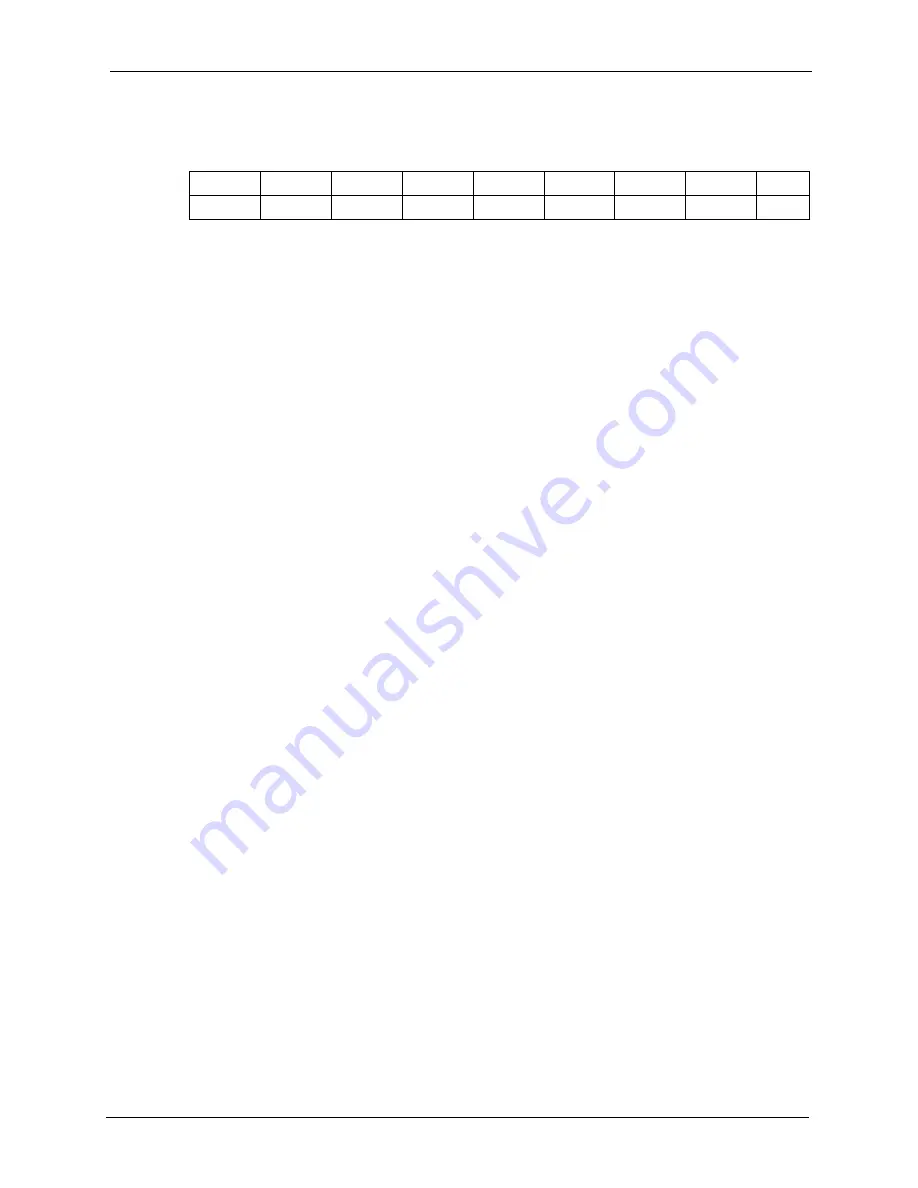
All SMTP commands are illegal except for those displayed in the following tables.
9.4.2.3 Traceroute
Traceroute is a utility used to determine the path a packet takes between two endpoints.
Sometimes when a packet filter firewall is configured incorrectly an attacker can traceroute
the firewall gaining knowledge of the network topology inside the firewall.
Often, many DoS attacks also employ a technique known as "
IP Spoofing
" as part of their
attack. IP Spoofing may be used to break into systems, to hide the hacker's identity, or to
magnify the effect of the DoS attack. IP Spoofing is a technique used to gain unauthorized
access to computers by tricking a router or firewall into thinking that the communications are
coming from within the trusted network. To engage in IP spoofing, a hacker must modify the
packet headers so that it appears that the packets originate from a trusted host and should be
allowed through the router or firewall. The ZyWALL blocks all IP Spoofing attempts.
9.5 Stateful Inspection
With stateful inspection, fields of the packets are compared to packets that are already known
to be trusted. For example, if you access some outside service, the proxy server remembers
things about your original request, like the port number and source and destination addresses.
This remembering is called
saving the state.
When the outside system responds to your
request, the firewall compares the received packets with the saved state to determine if they
are allowed in. The ZyWALL uses stateful packet inspection to protect the private LAN from
hackers and vandals on the Internet. By default, the ZyWALL’s stateful inspection allows all
communications to the Internet that originate from the LAN, and blocks all traffic to the LAN
that originates from the Internet. In summary, stateful inspection:
• Allows all sessions originating from the LAN (local network) to the WAN (Internet).
• Denies all sessions originating from the WAN to the LAN.
Table 53
Legal SMTP Commands
AUTH
DATA
EHLO
ETRN
EXPN
HELO
HELP
NOOP
QUIT
RCPT
RSET
SAML
SEND
SOML
TURN
VRFY
Содержание ZyXEL ZyWALL 35
Страница 1: ...ZyWALL 35 Internet Security Appliance User s Guide Version 3 64 3 2005 ...
Страница 2: ......
Страница 38: ...ZyWALL 35 User s Guide 36 ...
Страница 46: ...ZyWALL 35 User s Guide 44 ...
Страница 74: ...ZyWALL 35 User s Guide 72 Chapter 2 Introducing the Web Configurator ...
Страница 90: ...ZyWALL 35 User s Guide 88 Chapter 3 Wizard Setup ...
Страница 100: ...ZyWALL 35 User s Guide 98 Chapter 4 LAN Screens ...
Страница 106: ...ZyWALL 35 User s Guide 104 Chapter 5 Bridge Screens ...
Страница 128: ...ZyWALL 35 User s Guide 126 Chapter 6 Wireless LAN ...
Страница 135: ...ZyWALL 35 User s Guide Chapter 7 WAN Screens 133 Figure 47 General ...
Страница 152: ...ZyWALL 35 User s Guide 150 Chapter 7 WAN Screens Figure 57 Dial Backup Setup ...
Страница 158: ...ZyWALL 35 User s Guide 156 Chapter 7 WAN Screens ...
Страница 166: ...ZyWALL 35 User s Guide 164 Chapter 8 DMZ Screens ...
Страница 188: ...ZyWALL 35 User s Guide 186 Chapter 10 Firewall Screens Figure 75 Creating Editing A Firewall Rule ...
Страница 193: ...ZyWALL 35 User s Guide Chapter 10 Firewall Screens 191 Figure 80 My Service Rule Configuration ...
Страница 234: ...ZyWALL 35 User s Guide 232 Chapter 13 Introduction to IPSec ...
Страница 246: ...ZyWALL 35 User s Guide 244 Chapter 14 VPN Screens Figure 116 VPN Rules IKE Gateway Policy Edit ...
Страница 252: ...ZyWALL 35 User s Guide 250 Chapter 14 VPN Screens Figure 117 VPN Rules IKE Network Policy Edit ...
Страница 275: ...ZyWALL 35 User s Guide Chapter 15 Certificates 273 Figure 129 My Certificate Details ...
Страница 294: ...ZyWALL 35 User s Guide 292 Chapter 16 Authentication Server Figure 140 Local User Database ...
Страница 314: ...ZyWALL 35 User s Guide 312 Chapter 17 Network Address Translation NAT ...
Страница 318: ...ZyWALL 35 User s Guide 316 Chapter 18 Static Route ...
Страница 324: ...ZyWALL 35 User s Guide 322 Chapter 19 Policy Route ...
Страница 340: ...ZyWALL 35 User s Guide 338 Chapter 20 Bandwidth Management ...
Страница 376: ...ZyWALL 35 User s Guide 374 Chapter 22 Remote Management ...
Страница 390: ...ZyWALL 35 User s Guide 388 Chapter 24 Logs Screens Figure 198 Log Settings ...
Страница 413: ...ZyWALL 35 User s Guide Chapter 25 Maintenance 411 Figure 220 Restart Screen ...
Страница 414: ...ZyWALL 35 User s Guide 412 Chapter 25 Maintenance ...
Страница 440: ...ZyWALL 35 User s Guide 438 Chapter 28 WAN and Dial Backup Setup ...
Страница 456: ...ZyWALL 35 User s Guide 454 Chapter 31 DMZ Setup ...
Страница 460: ...ZyWALL 35 User s Guide 458 Chapter 32 Route Setup ...
Страница 470: ...ZyWALL 35 User s Guide 468 Chapter 33 Remote Node Setup ...
Страница 522: ...ZyWALL 35 User s Guide 520 Chapter 39 System Information Diagnosis ...
Страница 538: ...ZyWALL 35 User s Guide 536 Chapter 40 Firmware and Configuration File Maintenance ...
Страница 550: ...ZyWALL 35 User s Guide 548 Chapter 42 Remote Management ...
Страница 558: ...ZyWALL 35 User s Guide 556 Chapter 43 IP Policy Routing ...
Страница 574: ...ZyWALL 35 User s Guide 572 Chapter 45 Troubleshooting Figure 364 Java Sun ...
Страница 602: ...ZyWALL 35 User s Guide 600 Appendix C IP Subnetting ...
Страница 608: ...ZyWALL 35 User s Guide 606 Appendix E PPTP ...
Страница 626: ...ZyWALL 35 User s Guide 624 Appendix G Triangle Route ...
Страница 656: ...ZyWALL 35 User s Guide 654 Appendix J Importing Certificates ...
Страница 658: ...ZyWALL 35 User s Guide 656 Appendix K Command Interpreter ...
Страница 664: ...ZyWALL 35 User s Guide 662 Appendix L Firewall Commands ...
Страница 668: ...ZyWALL 35 User s Guide 666 Appendix M NetBIOS Filter Commands ...
Страница 674: ...ZyWALL 35 User s Guide 672 Appendix O Brute Force Password Guessing Protection ...
Страница 696: ...ZyWALL 35 User s Guide 694 Appendix Q Log Descriptions ...