Chapter 27 Security Policy
ZyWALL USG Series User’s Guide
575
Global Security Policies
Security Policies with
from any
and/or
to any
as the packet direction are called global Security Policies.
The global Security Policies are the only Security Policies that apply to an interface that is not included in
a zone. The
from any
policies apply to traffic coming from the interface and the
to any
policies apply to
traffic going to the interface.
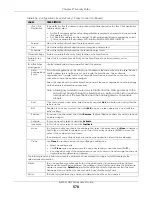
Security Policy Rule Criteria
The Zyxel Device checks the schedule, user name (user’s login name on the Zyxel Device), source IP
address and object, destination IP address and object, IP protocol type of network traffic (service) and
UTM profile criteria against the Security Policies (in the order you list them). When the traffic matches a
policy, the Zyxel Device takes the action specified in the policy.
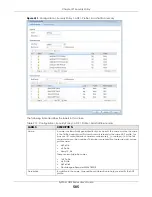
User Specific Security Policies
You can specify users or user groups in Security Policies. For example, to allow a specific user from any
computer to access a zone by logging in to the Zyxel Device, you can set up a policy based on the user
name only. If you also apply a schedule to the Security Policy, the user can only access the network at
the scheduled time. A user-aware Security Policy is activated whenever the user logs in to the Zyxel
Device and will be disabled after the user logs out of the Zyxel Device.
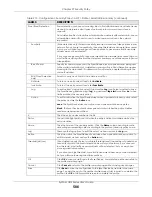
Session Limits
Accessing the Zyxel Device or network resources through the Zyxel Device requires a NAT session and
corresponding Security Policy session. Peer to peer applications, such as file sharing applications, may
use a large number of NAT sessions. A single client could use all of the available NAT sessions and
prevent others from connecting to or through the Zyxel Device. The Zyxel Device lets you limit the
number of concurrent NAT/Security Policy sessions a client can use.
27.4 The Security Policy Screen
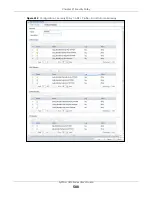
Asymmetrical Routes
If an alternate gateway on the LAN has an IP address in the same subnet as the Zyxel Device’s LAN IP
address, return traffic may not go through the Zyxel Device. This is called an asymmetrical or “triangle”
route. This causes the Zyxel Device to reset the connection, as the connection has not been
acknowledged.
You can have the Zyxel Device permit the use of asymmetrical route topology on the network (not reset
the connection). However, allowing asymmetrical routes may let traffic from the WAN go directly to the
LAN without passing through the Zyxel Device. A better solution is to use virtual interfaces to put the Zyxel
Device and the backup gateway on separate subnets. Virtual interfaces allow you to partition your
network into logical sections over the same interface. See the chapter about interfaces for more
information.
By putting LAN 1 and the alternate gateway (
A
in the figure) in different subnets, all returning network
traffic must pass through the Zyxel Device to the LAN. The following steps and figure describe such a
scenario.
Содержание USG110
Страница 27: ...27 PART I User s Guide ...
Страница 67: ...Chapter 2 Initial Setup Wizard ZyWALL USG Series User s Guide 67 Figure 41 Object Service Service Group HTTPS ...
Страница 195: ...195 PART II Technical Reference ...
Страница 282: ...Chapter 9 Wireless ZyWALL USG Series User s Guide 282 Figure 229 Configuration Wireless AP Management AP Group Add Edit ...
Страница 309: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 309 ...
Страница 310: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 310 Configuration Network Interface Ethernet Edit External Type ...
Страница 312: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 312 Configuration Network Interface Ethernet Edit Internal Type ...
Страница 313: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 313 ...
Страница 314: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 314 Figure 246 Configuration Network Interface Ethernet Edit OPT ...
Страница 315: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 315 Configuration Network Interface Ethernet Edit OPT ...
Страница 334: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 334 Figure 255 Configuration Network Interface PPP Add ...
Страница 342: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 342 Figure 257 Configuration Network Interface Cellular Add Edit ...
Страница 357: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 357 Figure 267 Configuration Network Interface VLAN Add Edit ...
Страница 358: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 358 ...
Страница 372: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 372 Figure 269 Configuration Network Interface Bridge Add Edit ...
Страница 373: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 373 ...
Страница 565: ...Chapter 25 Walled Garden ZyWALL USG Series User s Guide 565 Figure 399 Walled Garden Login Example ...
Страница 613: ...Chapter 30 IPSec VPN ZyWALL USG Series User s Guide 613 Figure 431 Configuration VPN IPSec VPN VPN Connection Add Edit ...
Страница 621: ...Chapter 30 IPSec VPN ZyWALL USG Series User s Guide 621 Figure 433 Configuration VPN IPSec VPN VPN Gateway Add Edit ...
Страница 651: ...Chapter 31 SSL VPN ZyWALL USG Series User s Guide 651 Figure 454 Create a Web Application SSL Application Object ...
Страница 664: ...Chapter 32 SSL User Screens ZyWALL USG Series User s Guide 664 4 Next run and log into the SecuExtender client ...
Страница 730: ...Chapter 38 IDP ZyWALL USG Series User s Guide 730 Figure 508 Configuration UTM Profile IDP Custom Signatures Add Edit ...
Страница 784: ...Chapter 42 Device HA ZyWALL USG Series User s Guide 784 Figure 541 Configuration Device HA Device HA ...
Страница 929: ...Chapter 44 System ZyWALL USG Series User s Guide 929 Figure 648 Configuration System WWW Login Page Desktop View ...
Страница 978: ...Chapter 45 Log and Report ZyWALL USG Series User s Guide 978 Figure 696 Log Category Settings AC ...
Страница 1011: ...Chapter 47 Diagnostics ZyWALL USG Series User s Guide 1011 Figure 720 Maintenance Diagnostics Network Tool ...