ZyWALL USG Series User’s Guide
1040
A
PPENDIX
A
Customer Support
In the event of problems that cannot be solved by using this manual, you should contact your vendor. If
you cannot contact your vendor, then contact a Zyxel office for the region in which you bought the
device.
See
http://www.zyxel.com/homepage.shtml
and also
http://www.zyxel.com/about_zyxel/zyxel_worldwide.shtml
for the latest information.
Please have the following information ready when you contact an office.
Required Information
• Product model and serial number.
• Warranty Information.
• Date that you received your device.
• Brief description of the problem and the steps you took to solve it.
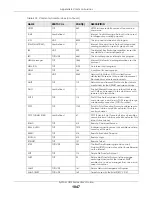
Corporate Headquarters (Worldwide)
Taiwan
• Zyxel Communications Corporation
• http://www.zyxel.com
Asia
China
• Zyxel Communications (Shanghai) Corp.
Zyxel Communications (Beijing) Corp.
Zyxel Communications (Tianjin) Corp.
• http://www.zyxel.cn
India
• Zyxel Technology India Pvt Ltd
• http://www.zyxel.in
Kazakhstan
• Zyxel Kazakhstan
• http://www.zyxel.kz
Содержание USG110
Страница 27: ...27 PART I User s Guide ...
Страница 67: ...Chapter 2 Initial Setup Wizard ZyWALL USG Series User s Guide 67 Figure 41 Object Service Service Group HTTPS ...
Страница 195: ...195 PART II Technical Reference ...
Страница 282: ...Chapter 9 Wireless ZyWALL USG Series User s Guide 282 Figure 229 Configuration Wireless AP Management AP Group Add Edit ...
Страница 309: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 309 ...
Страница 310: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 310 Configuration Network Interface Ethernet Edit External Type ...
Страница 312: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 312 Configuration Network Interface Ethernet Edit Internal Type ...
Страница 313: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 313 ...
Страница 314: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 314 Figure 246 Configuration Network Interface Ethernet Edit OPT ...
Страница 315: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 315 Configuration Network Interface Ethernet Edit OPT ...
Страница 334: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 334 Figure 255 Configuration Network Interface PPP Add ...
Страница 342: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 342 Figure 257 Configuration Network Interface Cellular Add Edit ...
Страница 357: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 357 Figure 267 Configuration Network Interface VLAN Add Edit ...
Страница 358: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 358 ...
Страница 372: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 372 Figure 269 Configuration Network Interface Bridge Add Edit ...
Страница 373: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 373 ...
Страница 565: ...Chapter 25 Walled Garden ZyWALL USG Series User s Guide 565 Figure 399 Walled Garden Login Example ...
Страница 613: ...Chapter 30 IPSec VPN ZyWALL USG Series User s Guide 613 Figure 431 Configuration VPN IPSec VPN VPN Connection Add Edit ...
Страница 621: ...Chapter 30 IPSec VPN ZyWALL USG Series User s Guide 621 Figure 433 Configuration VPN IPSec VPN VPN Gateway Add Edit ...
Страница 651: ...Chapter 31 SSL VPN ZyWALL USG Series User s Guide 651 Figure 454 Create a Web Application SSL Application Object ...
Страница 664: ...Chapter 32 SSL User Screens ZyWALL USG Series User s Guide 664 4 Next run and log into the SecuExtender client ...
Страница 730: ...Chapter 38 IDP ZyWALL USG Series User s Guide 730 Figure 508 Configuration UTM Profile IDP Custom Signatures Add Edit ...
Страница 784: ...Chapter 42 Device HA ZyWALL USG Series User s Guide 784 Figure 541 Configuration Device HA Device HA ...
Страница 929: ...Chapter 44 System ZyWALL USG Series User s Guide 929 Figure 648 Configuration System WWW Login Page Desktop View ...
Страница 978: ...Chapter 45 Log and Report ZyWALL USG Series User s Guide 978 Figure 696 Log Category Settings AC ...
Страница 1011: ...Chapter 47 Diagnostics ZyWALL USG Series User s Guide 1011 Figure 720 Maintenance Diagnostics Network Tool ...