P-660H/HW-T Series User’ Guide
Chapter 10 Firewalls
124
All SMTP commands are illegal except for those displayed in the following tables.
10.4.2.3 Traceroute
Traceroute is a utility used to determine the path a packet takes between two endpoints.
Sometimes when a packet filter firewall is configured incorrectly an attacker can traceroute
the firewall gaining knowledge of the network topology inside the firewall.
Often, many DoS attacks also employ a technique known as "
IP Spoofing
" as part of their
attack. IP Spoofing may be used to break into systems, to hide the hacker's identity, or to
magnify the effect of the DoS attack. IP Spoofing is a technique used to gain unauthorized
access to computers by tricking a router or firewall into thinking that the communications are
coming from within the trusted network. To engage in IP spoofing, a hacker must modify the
packet headers so that it appears that the packets originate from a trusted host and should be
allowed through the router or firewall. The Prestige blocks all IP Spoofing attempts.
10.5 Stateful Inspection
With stateful inspection, fields of the packets are compared to packets that are already known
to be trusted. For example, if you access some outside service, the proxy server remembers
things about your original request, like the port number and source and destination addresses.
This “remembering” is called
saving the state.
When the outside system responds to your
request, the firewall compares the received packets with the saved state to determine if they
are allowed in. The Prestige uses stateful packet inspection to protect the private LAN from
hackers and vandals on the Internet. By default, the Prestige’s stateful inspection allows all
communications to the Internet that originate from the LAN, and blocks all traffic to the LAN
that originates from the Internet. In summary, stateful inspection:
• Allows all sessions originating from the LAN (local network) to the WAN (Internet).
• Denies all sessions originating from the WAN to the LAN.
RETARGET:
KEEPALIVE:
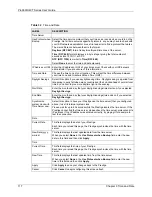
Table 36
Legal SMTP Commands
AUTH
DATA
EHLO
ETRN
EXPN
HELO
HELP
NOOP
QUIT
RCPT
RSET
SAML
SEND
SOML
TURN
VRFY
Table 35
Legal NetBIOS Commands
Содержание P-660H Series
Страница 2: ......
Страница 10: ...P 660H HW T Series User Guide 9 Customer Support ...
Страница 32: ...P 660H HW T Series User Guide 31 List of Figures ...
Страница 38: ...P 660H HW T Series User Guide 37 List of Tables ...
Страница 42: ...P 660H HW T Series User Guide 41 Introduction to DSL ...
Страница 62: ...P 660H HW T Series User Guide 61 Chapter 3 Wizard Setup for Internet Access ...
Страница 90: ...P 660H HW T Series User Guide 89 Chapter 5 Wireless LAN ...
Страница 132: ...P 660H HW T Series User Guide 131 Chapter 10 Firewalls ...
Страница 162: ...P 660H HW T Series User Guide 161 Chapter 13 Remote Management Configuration ...
Страница 176: ...P 660H HW T Series User Guide 175 Chapter 14 Universal Plug and Play UPnP ...
Страница 182: ...P 660H HW T Series User Guide 181 Chapter 15 Logs Screens ...
Страница 196: ...P 660H HW T Series User Guide 195 Chapter 16 Media Bandwidth Management Advanced Setup ...
Страница 208: ...P 660H HW T Series User Guide 207 Chapter 17 Maintenance ...
Страница 218: ...P 660H HW T Series User Guide 217 Chapter 19 Menu 1 General Setup ...
Страница 222: ...P 660H HW T Series User Guide 221 Chapter 20 Menu 2 WAN Backup Setup ...
Страница 226: ...P 660H HW T Series User Guide 225 Chapter 21 Menu 3 LAN Setup ...
Страница 230: ...P 660H HW T Series User Guide 229 Chapter 22 Wireless LAN Setup ...
Страница 236: ...P 660H HW T Series User Guide 235 Chapter 23 Internet Access ...
Страница 250: ...P 660H HW T Series User Guide 249 Chapter 25 Static Route Setup ...
Страница 254: ...P 660H HW T Series User Guide 253 Chapter 26 Bridging Setup ...
Страница 270: ...P 660H HW T Series User Guide 269 Chapter 27 Network Address Translation NAT ...
Страница 286: ...P 660H HW T Series User Guide 285 Chapter 29 Filter Configuration ...
Страница 306: ...P 660H HW T Series User Guide 305 Chapter 32 System Information and Diagnosis ...
Страница 318: ...P 660H HW T Series User Guide 317 Chapter 33 Firmware and Configuration File Maintenance ...
Страница 324: ...P 660H HW T Series User Guide 323 Chapter 34 System Maintenance ...
Страница 328: ...P 660H HW T Series User Guide 327 Chapter 35 Remote Management ...
Страница 338: ...P 660H HW T Series User Guide 337 Chapter 36 IP Policy Routing ...
Страница 342: ...P 660H HW T Series User Guide 341 Chapter 37 Call Scheduling ...
Страница 354: ...P 660H HW T Series User Guide 353 Chapter 38 Troubleshooting Figure 233 Security Setting ActiveX Controls ...
Страница 358: ...P 660H HW T Series User Guide 357 Appendix A ...
Страница 360: ...P 660H HW T Series User Guide 359 Appendix B ...
Страница 384: ...P 660H HW T Series User Guide 383 Appendix D ...
Страница 388: ...P 660H HW T Series User Guide 387 Appendix F ...
Страница 394: ...P 660H HW T Series User Guide 393 Appendix G ...
Страница 398: ...P 660H HW T Series User Guide 397 Appendix H ...
Страница 401: ...P 660H HW T Series User Guide Appendix I 400 ...
Страница 402: ...P 660H HW T Series User Guide 401 Appendix I ...
Страница 456: ...P 660H HW T Series User Guide 455 Appendix M ...