Chapter 9 Wireless LAN
P-2602HWLNI User’s Guide
131
Unauthorized wireless devices can still see the information that is sent in the wireless network,
even if they cannot use the wireless network. Furthermore, there are ways for unauthorized
wireless users to get a valid user name and password. Then, they can use that user name and
password to use the wireless network.
9.2.4 Encryption
Wireless networks can use encryption to protect the information that is sent in the wireless
network. Encryption is like a secret code. If you do not know the secret code, you cannot
understand the message.
The types of encryption you can choose depend on the type of authentication. (See
for information about this.)
For example, if the wireless network has a RADIUS server, you can choose
WPA
or
WPA2
. If
users do not log in to the wireless network, you can choose no encryption,
Static WEP
,
WPA-
PSK
, or
WPA2-PSK
.
Usually, you should set up the strongest encryption that every device in the wireless network
supports. For example, suppose you have a wireless network with the ZyXEL Device and you
do not have a RADIUS server. Therefore, there is no authentication. Suppose the wireless
network has two devices. Device A only supports WEP, and device B supports WEP and
WPA. Therefore, you should set up
Static WEP
in the wireless network.
"
It is recommended that wireless networks use
WPA-PSK
,
WPA
, or stronger
encryption. The other types of encryption are better than none at all, but it is
still possible for unauthorized wireless devices to figure out the original
information pretty quickly.
When you select
WPA2
or
WPA2-PSK
in your ZyXEL Device, you can also select an option
(
WPA compatible
) to support WPA as well. In this case, if some of the devices support WPA
and some support WPA2, you should set up
WPA2-PSK
or
WPA2
(depending on the type of
wireless network login) and select the
WPA compatible
option in the ZyXEL Device.
Many types of encryption use a key to protect the information in the wireless network. The
longer the key, the stronger the encryption. Every device in the wireless network must have the
same key.
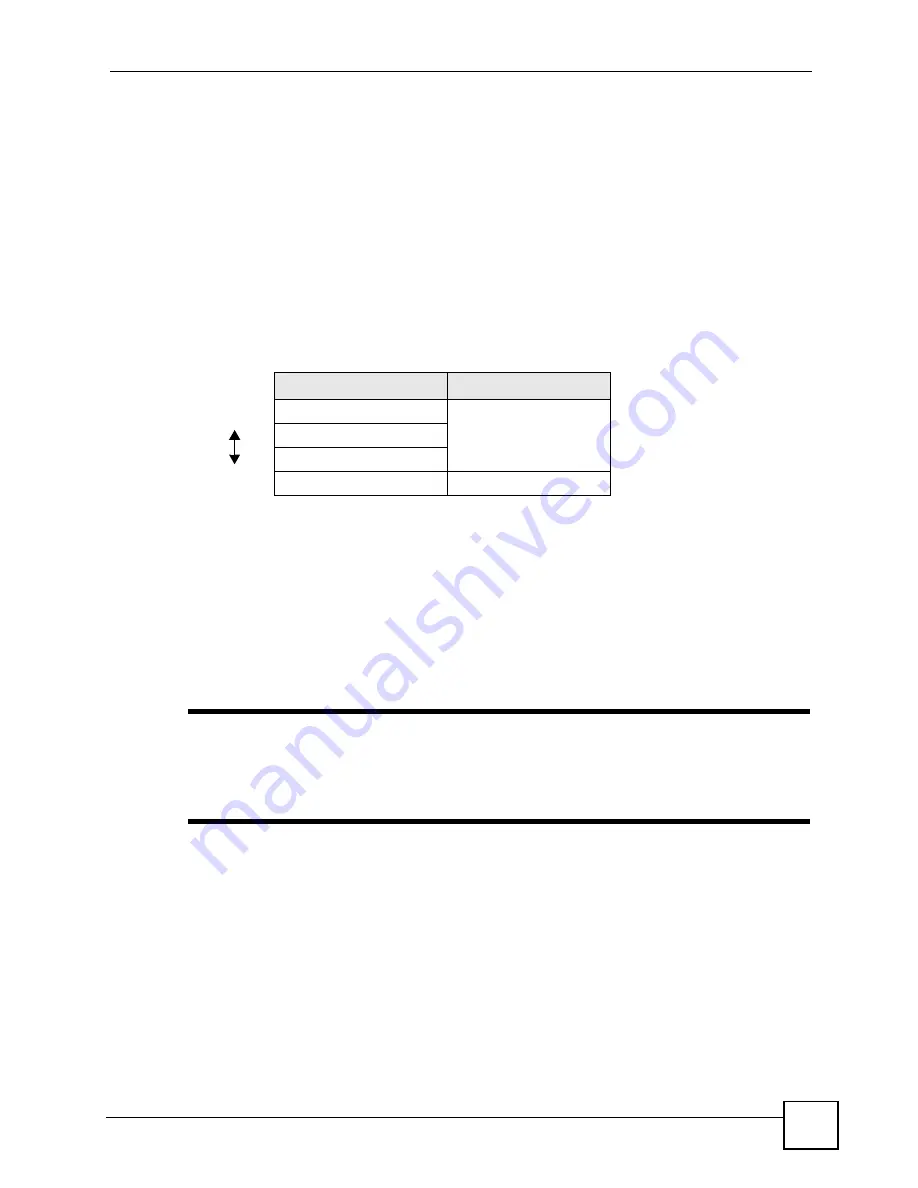
Table 34
Types of Encryption for Each Type of Authentication
NO AUTHENTICATION
RADIUS SERVER
Weakest
No Security
WPA
Static WEP
WPA-PSK
Strongest
WPA2-PSK
WPA2
Содержание P-2602HWLNI
Страница 2: ......
Страница 7: ...Safety Warnings P 2602HWLNI User s Guide 7...
Страница 8: ...Safety Warnings P 2602HWLNI User s Guide 8...
Страница 24: ...Table of Contents P 2602HWLNI User s Guide 24...
Страница 32: ...List of Figures P 2602HWLNI User s Guide 32...
Страница 38: ...List of Tables P 2602HWLNI User s Guide 38...
Страница 39: ...39 PART I Introduction Introducing the ZyXEL Device 41 Introducing the Web Configurator 49...
Страница 40: ...40...
Страница 60: ...Chapter 2 Introducing the Web Configurator P 2602HWLNI User s Guide 60...
Страница 62: ...62...
Страница 86: ...Chapter 5 Bandwidth Management Wizard P 2602HWLNI User s Guide 86...
Страница 98: ...Chapter 6 Status Screens P 2602HWLNI User s Guide 98...
Страница 99: ...99 PART III Network WAN Setup 101 LAN Setup 117 Wireless LAN 129 Network Address Translation NAT Screens 155...
Страница 100: ...100...
Страница 154: ...Chapter 9 Wireless LAN P 2602HWLNI User s Guide 154...
Страница 166: ...Chapter 10 Network Address Translation NAT Screens P 2602HWLNI User s Guide 166...
Страница 167: ...167 PART IV VoIP Voice 169 VoIP Trunking 211 Phone Usage 227...
Страница 168: ...168...
Страница 226: ...Chapter 12 VoIP Trunking P 2602HWLNI User s Guide 226...
Страница 230: ...Chapter 13 Phone Usage P 2602HWLNI User s Guide 230...
Страница 232: ...232...
Страница 264: ...Chapter 15 Firewall Configuration P 2602HWLNI User s Guide 264...
Страница 268: ...Chapter 16 Content Filtering P 2602HWLNI User s Guide 268...
Страница 274: ...Chapter 17 Introduction to IPSec P 2602HWLNI User s Guide 274...
Страница 309: ...Chapter 19 Certificates P 2602HWLNI User s Guide 309 Figure 173 My Certificate Details...
Страница 320: ...Chapter 19 Certificates P 2602HWLNI User s Guide 320 Figure 181 Trusted Remote Host Details...
Страница 326: ...326...
Страница 330: ...Chapter 20 Static Route P 2602HWLNI User s Guide 330...
Страница 338: ...Chapter 21 Bandwidth Management P 2602HWLNI User s Guide 338...
Страница 342: ...Chapter 22 Dynamic DNS Setup P 2602HWLNI User s Guide 342...
Страница 360: ...Chapter 23 Remote Management Configuration P 2602HWLNI User s Guide 360...
Страница 372: ...Chapter 24 Universal Plug and Play UPnP P 2602HWLNI User s Guide 372...
Страница 374: ...374...
Страница 380: ...Chapter 25 System P 2602HWLNI User s Guide 380...
Страница 406: ...Chapter 28 Troubleshooting P 2602HWLNI User s Guide 406...
Страница 422: ...Chapter 30 Diagnostic P 2602HWLNI User s Guide 422...
Страница 432: ...Chapter 31 Product Specifications P 2602HWLNI User s Guide 432...
Страница 434: ...434...
Страница 446: ...Appendix A Setting up Your Computer s IP Address P 2602HWLNI User s Guide 446...
Страница 482: ...Appendix F Legal Information P 2602HWLNI User s Guide 482...
Страница 488: ...Appendix G Customer Support P 2602HWLNI User s Guide 488...






























