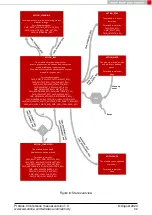
As soon as one module closes the connection using a
, both devices
will inform their host by a
message that the connection is no longer
open. If a device is no longer within range, the
message is triggered
by a timeout.
An example of setting up an unsecured connection is shown in chapter
. How to set-
up a secured connection is shown in the preceding chapters. See also the application note
"ANR009 advanced developer guide" to get detailed information about the connection setup
with foreign devices.
5.4.1. Further information for a secure connection setup
The
parameter of the module determines the security mode. If a certain se-
curity mode of a Proteus-III peripheral device is set, its security level has to be met by the
connecting central device to be able to exchange data. As long as the defined security level
is not met by the central device, no access to the peripheral’s profiles will be granted.
When connecting from a Proteus-III to a Proteus-III, you shall not use different
security modes.
To get further information about the secured connection setup, when using
a foreign device (i.e. mobile phone with a custom APP), please refer to the
Proteus-III application note "ANR009 advanced developer guide".
5.4.1.1. Just works mode
In case of the "Just works" mode, each time a connection is established, a new random key
is exchanged in advance to be used for data encryption. Since no authentication will be
performed, also devices without input and output capabilities (like keyboard or display) are
able to connect to each other.
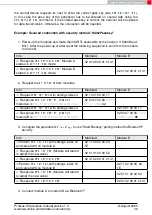
Example: Secured connection with LE Legacy security method "Just Works" without
bonding
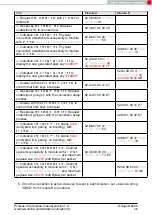
1. Power-up the modules and make their UARTs accessible by the host(s) (115200 Baud,
8n1). After the power-up or after reset the following sequence is sent from the module
to the host.
Proteus-III reference manual version 1.3
© August 2020
www.we-online.com/wireless-connectivity
35