Trend Micro
™
Deep Edge
™
solution offers a new level of simplicity for deployment, configuration,
and management of a next
‐
generation firewall appliance.
Use this Quick Start Guide to get Deep Edge up and running on your network. For more
information, see:
Readme — Covers basic getting started instructions, new features, known issues, and
late
‐
breaking information.
Deployment Guide — Describes installation, planning, deployment, and initial configuration.
Administrator’s Guide — Contains a comprehensive overview of Deep Edge. It also provides
detailed configuration and management information.
Online help — Explains product screens and discusses administrative tasks and relevant
concepts.
For the latest versions of Deep Edge documentation, visit Trend Micro’s Download Center at:
http://docs.trendmicro.com
Planning your traffic flow
3 of 6
1 of 6
2 of 6
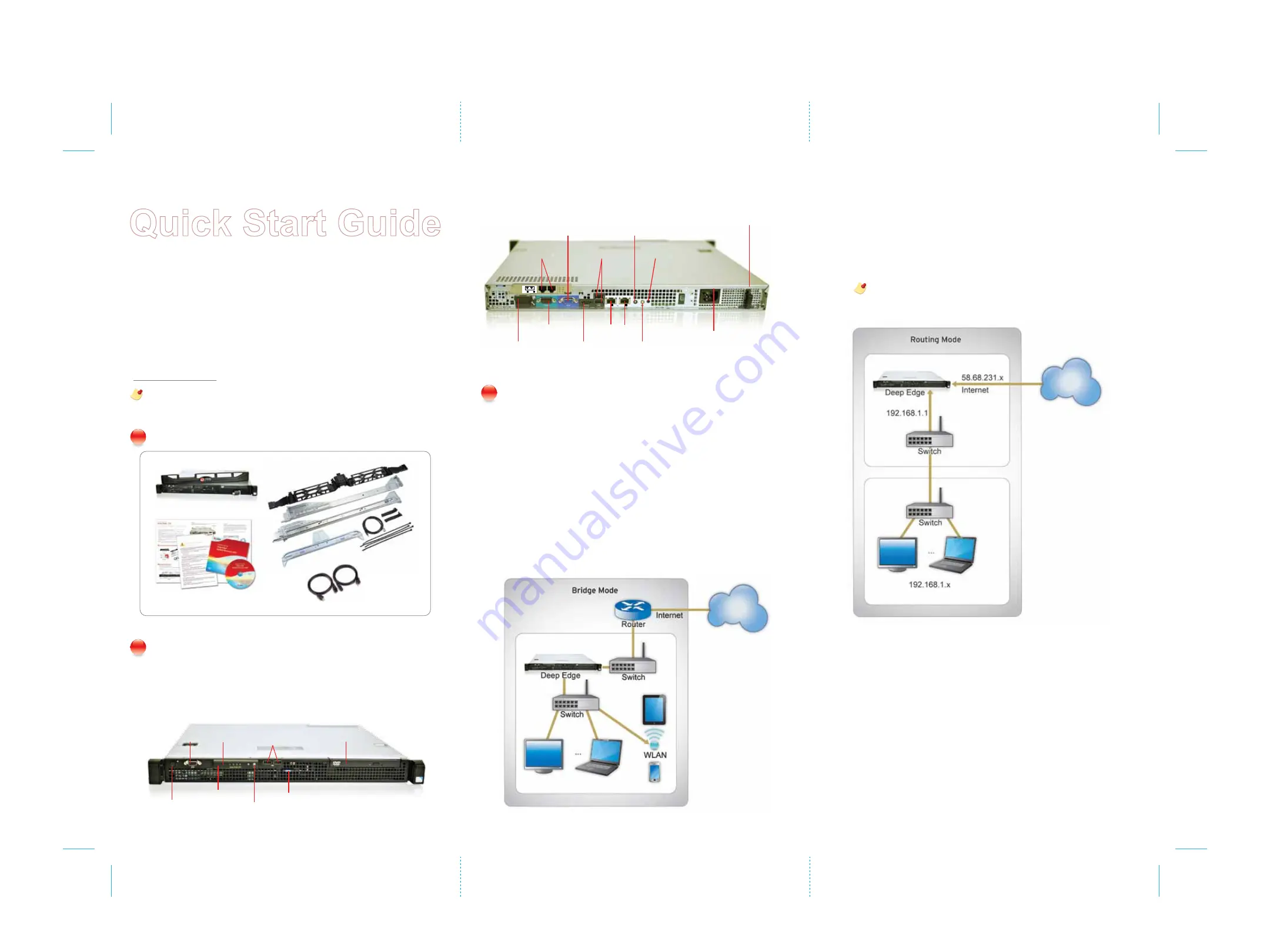
Routing Mode
In Routing mode, each Deep Edge unit is visible to the network to which it is
connected. All of its interfaces are on different subnets. Each interface connected to
a network must be configured with an IP address that is valid for that network.
You would typically use Routing mode when the Deep Edge unit is deployed as a
gateway between private and public networks. In the Routing mode configuration,
the unit functions as a firewall. Firewall policies control communications through the
Deep Edge unit. The Deep Edge unit scans traffic for malware using the default
policy until you create a custom policy.
Monitoring Mode
In Monitoring mode, Deep Edge is invisible to the network. Establish the settings for
your switch and mirror the traffic to the port that connects to the Deep Edge. Deep
Edge monitors your network traffic and only logs violation
‐
related information.
Network traffic is never blocked in this mode even if policies exist.
In Monitoring Mode, network traffic does not pass directly through the Deep Edge
device. Traffic goes outside of Deep Edge, and Deep Edge runs independently
outside the network (logically) aided by the switches of the network which mirror the
specified traffic to interface(s) on which Deep Edge listens. Deep Edge monitors the
status of the traffic and presents the information to the Deep Edge admin.
Trend Micro suggests Deep Edge be deployed at the core Internet switch in order to
see a copy of all Internet traffic leaving and entering your corporate network.
Rack Rail Box
Power Cords
Your package should include the following items
1
3
Note
:
Trend Micro recommends reading the Deep Edge Deployment and Administrator’s
Guides before setting up the Deep Edge appliance.
Note
:
To use routing mode, you must switch from the default bridge mode.
Device with bezel
TREND MICRO
TM
Deep Edge
TM
Before connecting the Deep Edge unit:
1. Place the unit on a stable surface or rack.
2. Review the interfaces on the front and back panels of the Deep Edge device.
Front panel
The front panel provides a quick way to connect a keyboard and a VGA monitor to the device.
Reviewing the device ports
2
VGA Port
Power Button
Hard drive
activity indicator
Device
ID button
System ID panel
Diagnostic
indicator
DVD drive
USB
connectors
Before configuring the Deep Edge appliance, plan how to integrate the unit into your
network. Your configuration plan depends on the operating mode you select: Inline
Mode (Routing Mode or Bridge Mode) or Monitoring Mode.
Bridge Mode
In Bridge mode, the Deep Edge unit is invisible to the network. All of its interfaces are
on the same subnet. You only have to configure a management IP address so that you
can make configuration changes.
You would typically use Bridge mode on a private network behind an existing firewall or
behind a router. Position Deep Edge between layer 2 and layer 3 switches to scan all
packets entering and leaving that section of the network. In the default Bridge mode
configuration, the device functions as a firewall. The Deep Edge unit scans traffic for
malware using the default policy until you create a custom policy. Under the default
policy:
Deep Edge scans and blocks malware on all traffic.
Deep Edge also monitors and detects all types of violations in the network traffic.
Documentation
Rear panel
The back panel contains all the network interface ports. These ports are grouped into the
management interface ports and the data interface ports.
Fold
Fold
Fold
Fold
Data Ports
iDRAC port
eSATA
Device ID Button
Power Supply Connector
Serial Connector
Ethernet
Connectors
USB 2.0
Connectors
System ID
Connector
Video Connector
Status Indicator
Retention Clip
Eth
Eth
0
1
Eth
2
3
Eth



















