Common Errors and Asynchronous Events
105
SWRU455A – February 2017 – Revised March 2017
Copyright © 2017, Texas Instruments Incorporated
Secure Socket
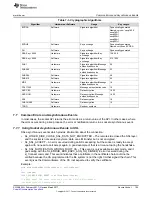
Table 7-3. Cryptographic Algorithms
Algorithm
Hardware or Software
Usage
Key Length
ECDSA
Software
Signature algorithm
Dynamically generated
Named curves – secp160r1
secp192r1
secp224r1
secp256r1
secp384r1
secp521r1
ECDHE
Software
Key exchange
Dynamically generated
Named curves as ECDSA
DH
Software
Key exchange
Dynamically generated
RSA Key < 4096
Hardware
Signature algorithm/Key
exchange
128, 256
RSA Key > 4096
Software
Signature algorithm/Key
exchange
512,1024
SHA1
Hardware
Signature algorithm/Message
authentication code
20
SHA256
Hardware
Signature algorithm/Message
authentication code
32
SHA384
Software
Signature algorithm
48
SHA512
Software
Signature algorithm
64
MD5
Hardware
Signature algorithm/Message
authentication code
16
POLY1305
Software
Message authentication code
16
AES CBC
Hardware
Data encryption
16, 32
AES GCM
Hardware
Data encryption/Message
authentication code
16, 32
RC4
Software
Data encryption
16
CHACHA20
Software
Data encryption
16
TRNG
Hardware
Random numbers
7.7
Common Errors and Asynchronous Events
In most cases, the socket API returns the error code as a return value of the API. In other cases, where
the error occurs during a live process, the error or notification returns in a socket asynchronous event.
7.7.1 Using Socket Asynchronous Events in SSL
SSL asynchronous events which provide information about the connection:
•
SL_OTHER_SIDE_CLOSE_SSL_DATA_NOT_ENCRYPTED – The remote side closed the SSL layer,
and the socket is not secured anymore; data can still transfer but is not encrypted.
•
SL_SSL_ACCEPT – An error occurred during an SSL accepting, but the socket is ready to accept
again with no need to call accept again. A good example of that is a time-out during the handshake.
•
SL_SSL_NOTIFICATION_WRONG_ROOT_CA – This event is only available in client mode, and it
goes along with the SL_ERROR_BSD_ESEC_ASN_NO_SIGNER_E error received during the
sl_Connect command. This event indicates that a certificate in the certificate chain could not be
verified because the CA programmed to the file system is not the right CA that signed the chain. This
event gives the CommonName of the CA root expected to verify the certificate.
Example:
void
slcbSockEvtHdlr(SlSockEvent_t* pSlSockEvent)
{
char
*CAname;
if
(SL_SOCKET_ASYNC_EVENT == pSlSockEvent->Event)
{
/* debug print "an event received on socket %d\n",pSlSockEvent-
>SocketAsyncEvent.SockAsyncData.Sd */