RUGGEDCOM ROX II
User Guide
Chapter 5
Setup and Configuration
Configuring the Layer 2 Tunnel Daemon
647
Section 5.29.4
Configuring the Layer 2 Tunnel Daemon
To configure the Layer 2 tunnel daemon, do the following:
IMPORTANT!
Make sure there are no traffic loops possible between the substation LAN and other LANs that could
forward GOOSE frames to the LAN. Do not employ a GOOSE gateway between substations that are
already connected. The GOOSE daemon issues packets to the network with a built in Time-To-Live
(TTL) count that is decremented with each transmission. This prevents an infinite loop of packets, but
will not prevent excessive network utilization.
1. Change the mode to
Edit Private
or
Edit Exclusive
.
2. Navigate to
tunnel
»
l2tunneld
. The
L2 Tunnel Daemon
form appears.
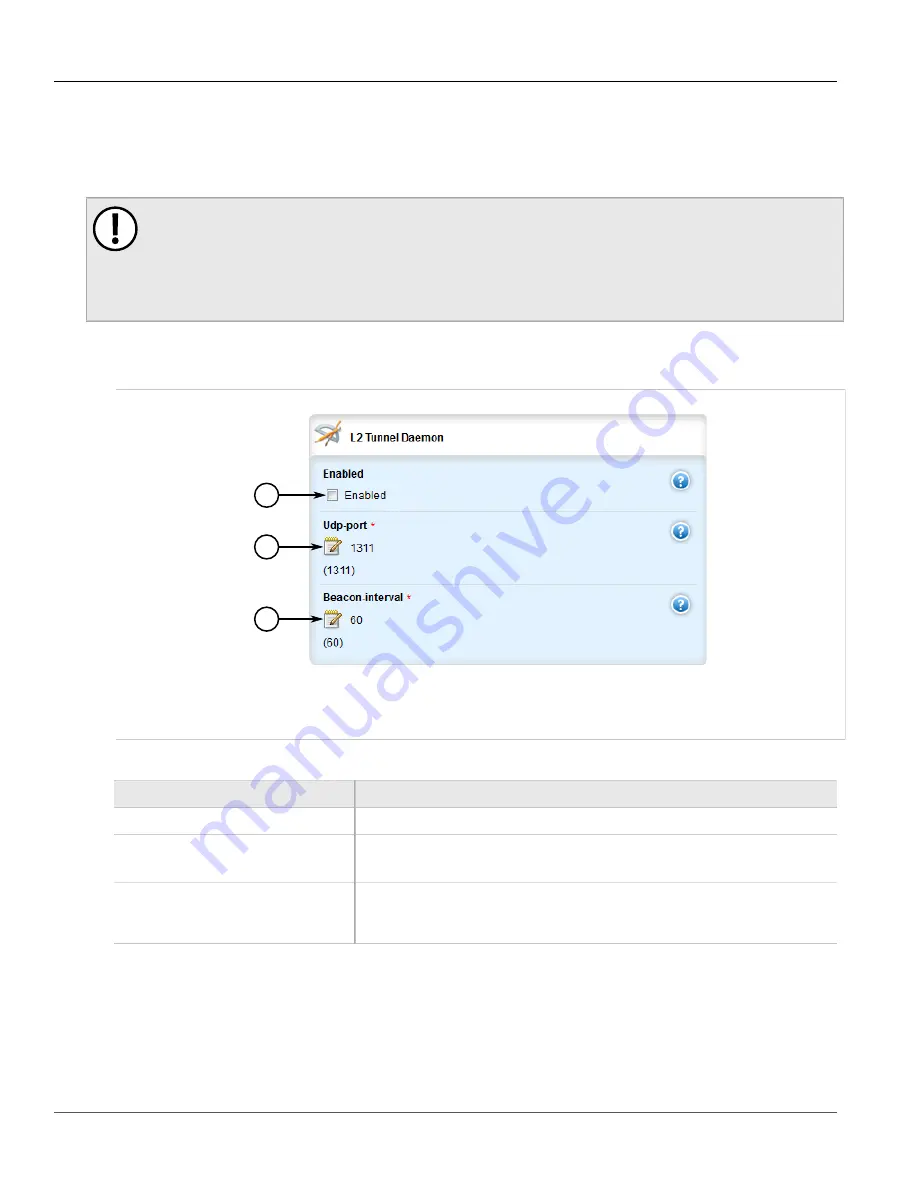
1
2
3
Figure 759: L2 Tunnel Daemon Form
1.
Enabled Check Box
2.
UDP Port Box
3.
Beacon Interval Box
3. Configure the following parameter(s) as required:
Parameter
Description
enabled
Enables the Layer 2 protocols server.
udp-port
Default:
1311
The UDP port to communicate with the other daemon.
beacon-interval
Synopsis:
off
Default:
60
The Round Trip Time (RTT) of the sent message
4. Add GOOSE or generic tunnels as required. For more information, refer to
Section 5.29.7.3, “Adding a Generic Tunnel”
5. Click
Commit
to save the changes or click
Revert All
to abort. A confirmation dialog box appears. Click
OK
to proceed.
6. Click
Exit Transaction
or continue making changes.
Содержание RUGGEDCOM RX1510
Страница 32: ...RUGGEDCOM ROX II User Guide Preface Customer Support xxxii ...
Страница 44: ...RUGGEDCOM ROX II User Guide Chapter 1 Introduction User Permissions 12 ...
Страница 62: ...RUGGEDCOM ROX II User Guide Chapter 2 Using ROX II Using the Command Line Interface 30 ...
Страница 268: ...RUGGEDCOM ROX II User Guide Chapter 4 System Administration Deleting a Scheduled Job 236 ...
Страница 852: ...RUGGEDCOM ROX II User Guide Chapter 5 Setup and Configuration Enabling Disabling an LDP Interface 820 ...






























