auto configured. After this, the IPsec SA (Phase 2) settings, which allow actual IPsec transmission, are
auto configured.
Also, for further security, the SA can be periodically auto updated by applying a validity period (time
limit) for its settings. This machine only supports IKEv1 for encryption key auto exchange.
Note that it is possible to configure multiple SAs.
Settings 1-4 and default setting
Using the auto exchange method, you can configure four separate sets of SA details (such as
different shared keys and IPsec algorithms). In the default settings of these sets, you can include
settings that the fields of sets 1 to 4 cannot contain.
When IPsec is enabled, set 1 has the highest priority and set 4 has the lowest. You can use this
priority system to target IP addresses more securely. For example, set the broadest IP range at the
lowest priority (4), and then set specific IP addresses at a higher priority level (3 and higher). This
way, when IPsec transmission is enabled for a specific IP address, the higher level settings will be
applied.
IPsec Settings
IPsec settings for this machine can be made on Web Image Monitor. The following table explains
individual setting items.
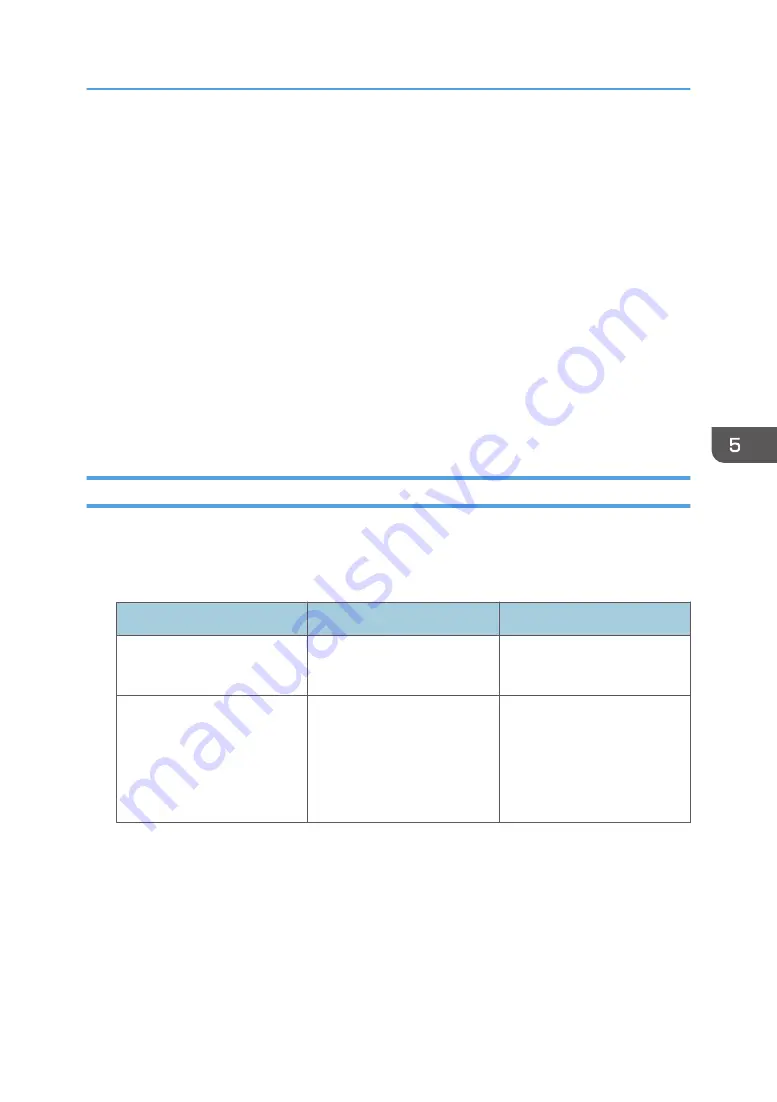
IPsec settings items
Setting
Description
Setting value
IPsec
Specify whether to enable or
disable IPsec.
• Active
• Inactive
Exclude HTTPS
Communication
Specify whether to enable
IPsec for HTTPS transmission.
• Active
• Inactive
Specify "Active" if you do not
want to use IPsec for HTTPS
transmission.
The IPsec setting can also be configured from the control panel.
Encryption key auto exchange security level
When you select a security level, certain security settings are automatically configured. The
following table explains security level features.
Configuring IPsec Settings
93
Содержание PRO C9100
Страница 2: ......
Страница 8: ...List of Operation Privileges for Address Books 229 INDEX 231 6...
Страница 24: ...1 Getting Started 22...
Страница 72: ...4 Preventing Leakage of Information from Machines 70...
Страница 116: ...5 Enhanced Network Security 114...
Страница 176: ...6 Managing the Machine 174...
Страница 188: ...7 Troubleshooting 186...
Страница 218: ...System Log Settings User Mach N W File Unset Set System Log R R R R R 8 List of Operation Privileges for Settings 216...
Страница 220: ...Settings User Mach N W File Unset Set Device Access Violation R W 8 List of Operation Privileges for Settings 218...
Страница 235: ......
Страница 236: ...EN GB EN US EN AU M238 1022 2014...
















































