Configuring SSL/TLS Settings
Configuring the machine to use SSL/TLS enables encrypted communication. Doing so helps prevent
data from being intercepted, cracked, or tampered with during transmission.
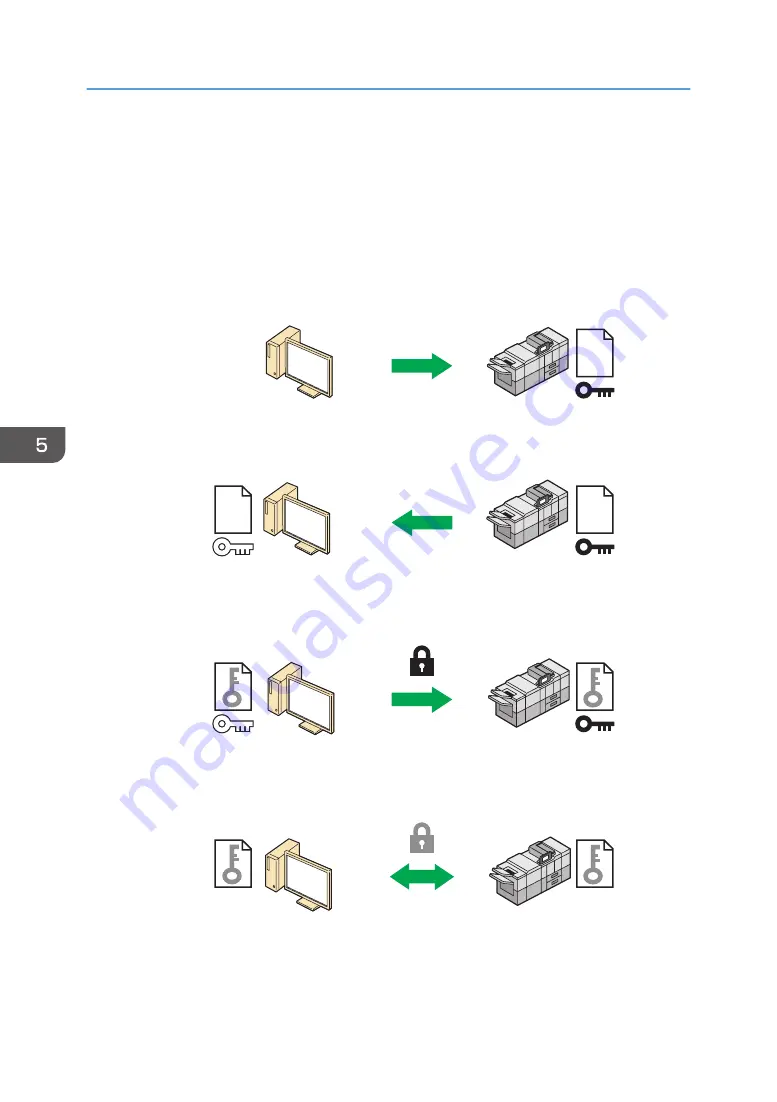
Flow of SSL/TLS encrypted communications
1. To access the machine from a user's computer, request the SSL/TLS device certificate and
public key.
CZB002
2. The device certificate and public key are sent from the machine to the user's computer.
CZB003
3. The shared key created with the computer is encrypted using the public key, sent to the
machine, and then decrypted using the private key in the machine.
CZB004
4. The shared key is used for data encryption and decryption, thus achieving secure
transmission.
CZB005
Configuration flow when using a self-signed certificate
1. Creating and installing the device certificate:
5. Enhanced Network Security
86
Содержание PRO C9100
Страница 2: ......
Страница 8: ...List of Operation Privileges for Address Books 229 INDEX 231 6...
Страница 24: ...1 Getting Started 22...
Страница 72: ...4 Preventing Leakage of Information from Machines 70...
Страница 116: ...5 Enhanced Network Security 114...
Страница 176: ...6 Managing the Machine 174...
Страница 188: ...7 Troubleshooting 186...
Страница 218: ...System Log Settings User Mach N W File Unset Set System Log R R R R R 8 List of Operation Privileges for Settings 216...
Страница 220: ...Settings User Mach N W File Unset Set Device Access Violation R W 8 List of Operation Privileges for Settings 218...
Страница 235: ......
Страница 236: ...EN GB EN US EN AU M238 1022 2014...