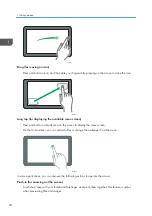
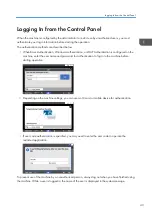
Logging In from the Control Panel
When the machine is configured by the administrator to restrict use by unauthorized users, you must
authenticate your login information before starting the operation.
The authentication methods are described below.
• When Basic Authentication, Windows Authentication, or LDAP Authentication is configured on the
machine, enter the user name and password for authentication to log in to the machine before
starting operation.
• Depending on the machine settings, you can use an IC card or mobile device for authentication.
• If user code authentication is specified, you may need to enter the user code to operate the
restricted application.
To prevent use of the machine by an unauthorized person, always log out when you have finished using
the machine. While a user is logged in, the name of the user is displayed in the system message.
Logging In from the Control Panel
43
Содержание IM C530 Series
Страница 2: ......
Страница 82: ...3 Fax 80 ...
Страница 144: ...5 Scan 142 ...
Страница 150: ...6 Web Image Monitor 148 ...
Страница 275: ...Function Reference Option Quick Card Authentication NFC card reader Functions Requiring Optional Configurations 273 ...
Страница 278: ...9 Specifications for The Machine 276 ...
Страница 287: ... 2020 ...
Страница 288: ...D0CS 7013 US EN GB EN ...