DefensePro User Guide
Basic Device Configuration
88
Document ID: RDWR-DP-V0602_UG1201
Configuring Session Table Settings
DefensePro includes a Session table, which tracks sessions bridged and forwarded by the device.
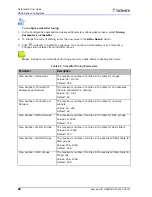
To configure Session table settings
1. In the Configuration perspective Advanced Parameters tab navigation pane, select Session
Table Settings.
2. Configure the parameters; and then, click
(Submit) to submit the changes.
SSH User Name
The name of the SSH user.
SSH Password
The password of the SSH user.
Verify SSH Password
Verification of password for the SSH user.
Router Interface for
Receiving Traffic
The router interface that is being monitored, and traffic from it will be
redirected.
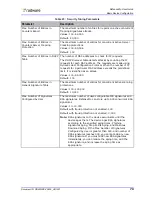
Table 31: Session Table Parameters
Parameter
Description
Enable Session Table
When enabled, the device uses the Session table.
Default: Enabled
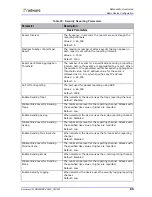
Remove Session Entry at
Session End
When enabled, the device removes sessions from the Session
Table five seconds after receiving a FIN or RST packet if no
additional packets are received on the same session within the
five seconds. This option is available only for Full Layer 4 Lookup
Mode (default mode).
Default: Enabled
Send Reset to Destination When
No Data is Received
Specifies whether the DefensePro device sends a RST packet for
TCP sessions where the device has seen the three-way
handshake (SYN and then ACK from the source) but has not seen
subsequent data packets.
Values:
•
Enabled—DefensePro sends reset a RST packet to the
destination and cleans the entry in the DefensePro Session
table.
•
Disabled—DefensePro ages the session normally (using
short SYN timeout), but the destination might hold the
session for quite some time.
Default: Disabled
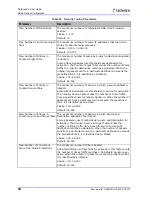
Table 30: Out of Path Parameters
Parameter
Description
Содержание DefensePro 6.02
Страница 1: ...DefensePro User Guide Software Version 6 02 Document ID RDWR DP V0602_UG1201 January 2012 ...
Страница 2: ...DefensePro User Guide 2 Document ID RDWR DP V0602_UG1201 ...
Страница 20: ...DefensePro User Guide 20 Document ID RDWR DP V0602_UG1201 ...
Страница 28: ...DefensePro User Guide Table of Contents 28 Document ID RDWR DP V0602_UG1201 ...
Страница 116: ...DefensePro User Guide Device Network Configuration 116 Document ID RDWR DP V0602_UG1201 ...
Страница 256: ...DefensePro User Guide Managing Device Operations and Maintenance 256 Document ID RDWR DP V0602_UG1201 ...
Страница 274: ...DefensePro User Guide Monitoring DefensePro Devices and Interfaces 274 Document ID RDWR DP V0602_UG1201 ...
Страница 302: ...DefensePro User Guide Real Time Security Reporting 302 Document ID RDWR DP V0602_UG1201 ...
Страница 308: ...DefensePro User Guide Administering DefensePro 308 Document ID RDWR DP V0602_UG1201 ...
Страница 324: ...DefensePro User Guide Troubleshooting 324 Document ID RDWR DP V0602_UG1201 ...