DefensePro User Guide
Security Configuration
138
Document ID: RDWR-DP-V0602_UG1201
Configuring Global DNS Flood Protection
DNS Flood Protection, which you can use in your network-protection policy, defends your network
from zero-day DNS-flood attacks. These attacks fill available DNS bandwidth with irrelevant traffic,
denying legitimate users DNS lookups. The attacks originate in the public network and threaten
Internet-connected organizations.
The DNS Flood profiles detect traffic anomalies and prevent zero-day, unknown, DNS flood attacks
by identifying the footprint of the anomalous traffic.
DNS Flood Protection types can include the following DNS query types:
•
A
•
MX
•
PTR
•
AAAA
•
Text
•
SOA
•
NAPTR
•
SRV
•
Other
DNS Flood Protection can detect statistical anomalies in DNS traffic and generate an accurate attack
footprint based on a heuristic protocol information analysis. This ensures accurate attack filtering
with minimal risk of false positives. The default average time for a new signature creation is between
10 and 18 seconds. This is a relatively short time, because flood attacks can last for minutes and
sometimes hours.
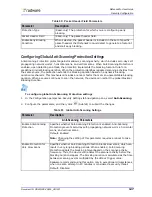
Before you configure DNS Flood Protection profiles, ensure that DNS Flood Protection is enabled. You
can also change the default global device settings for DNS Flood Protection. The DNS Flood
Protection global settings apply to all the network protection-policy rules with DNS Flood profiles on
the device.
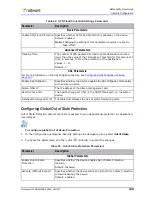
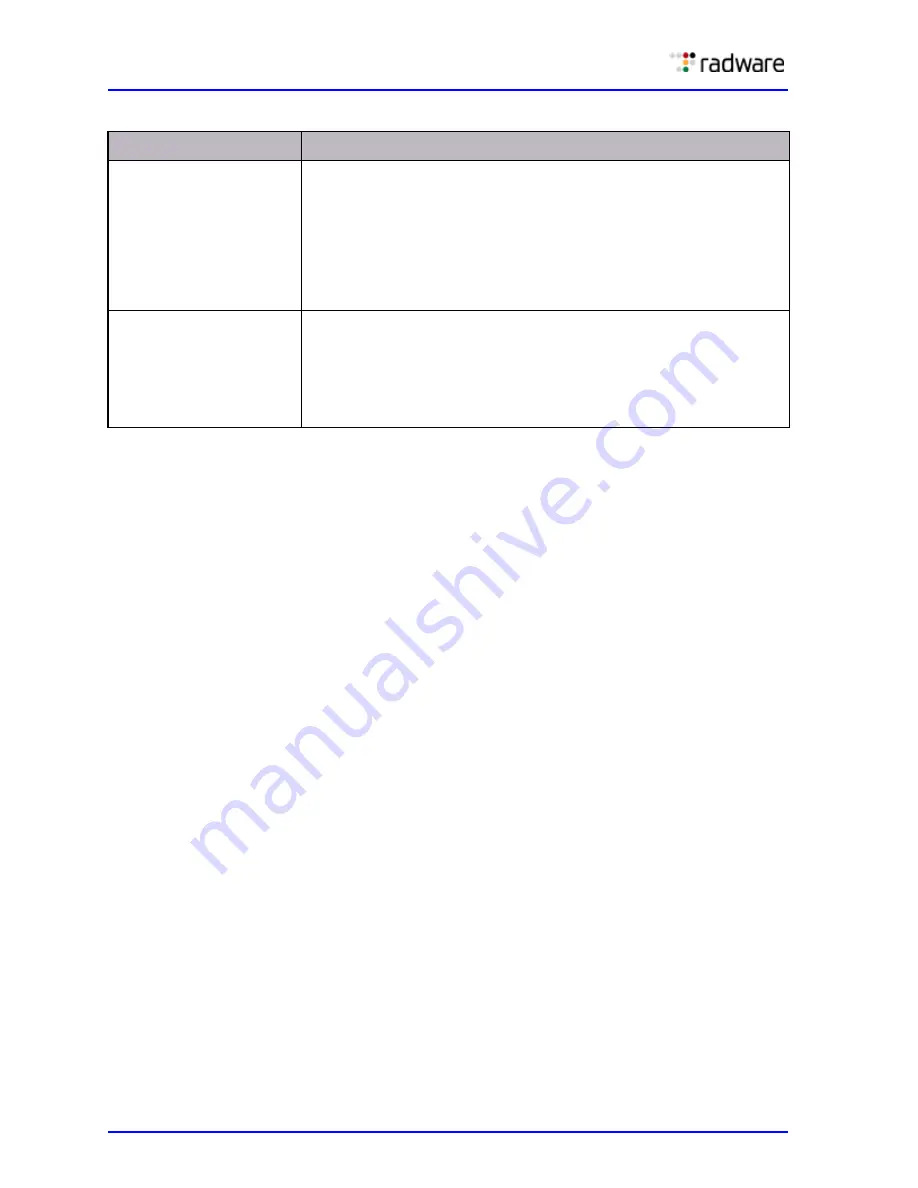
Source Address same as
Dest. Address (Land
Attack)
The source IP address and the destination IP address in the packet
header are the same. This is referred to as a LAND, Land, or LanD
attack.
ID: 120
Default Action: Drop
Default Risk: Info
Note:
All DefensePro platforms support this anomaly type.
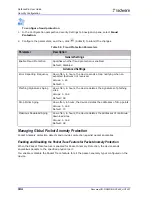
L4 Source or Dest. Port
Zero
The Layer 4 source port or destination port equals zero.
ID: 125
Default Action: Drop
Default Risk: Info
Note:
All DefensePro platforms support this anomaly type.
1 – This parameter is available only on OnDemand Switch 3 platforms with the hardware-based
mitigator component.
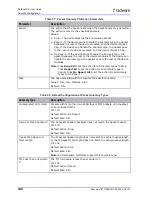
Table 68: Default Configuration of Packet Anomaly Types
Anomaly Type
Description
Содержание DefensePro 6.02
Страница 1: ...DefensePro User Guide Software Version 6 02 Document ID RDWR DP V0602_UG1201 January 2012 ...
Страница 2: ...DefensePro User Guide 2 Document ID RDWR DP V0602_UG1201 ...
Страница 20: ...DefensePro User Guide 20 Document ID RDWR DP V0602_UG1201 ...
Страница 28: ...DefensePro User Guide Table of Contents 28 Document ID RDWR DP V0602_UG1201 ...
Страница 116: ...DefensePro User Guide Device Network Configuration 116 Document ID RDWR DP V0602_UG1201 ...
Страница 256: ...DefensePro User Guide Managing Device Operations and Maintenance 256 Document ID RDWR DP V0602_UG1201 ...
Страница 274: ...DefensePro User Guide Monitoring DefensePro Devices and Interfaces 274 Document ID RDWR DP V0602_UG1201 ...
Страница 302: ...DefensePro User Guide Real Time Security Reporting 302 Document ID RDWR DP V0602_UG1201 ...
Страница 308: ...DefensePro User Guide Administering DefensePro 308 Document ID RDWR DP V0602_UG1201 ...
Страница 324: ...DefensePro User Guide Troubleshooting 324 Document ID RDWR DP V0602_UG1201 ...