Table 6. Wep key description
(Note: 65 is the ASCII value of ‘A’ and 66 is that of ‘B”, and so on. The bold fonts are added to
distinguish the numbers from each other.)
When using WEP, the modes “Open” and “Shared” are interchangeable.
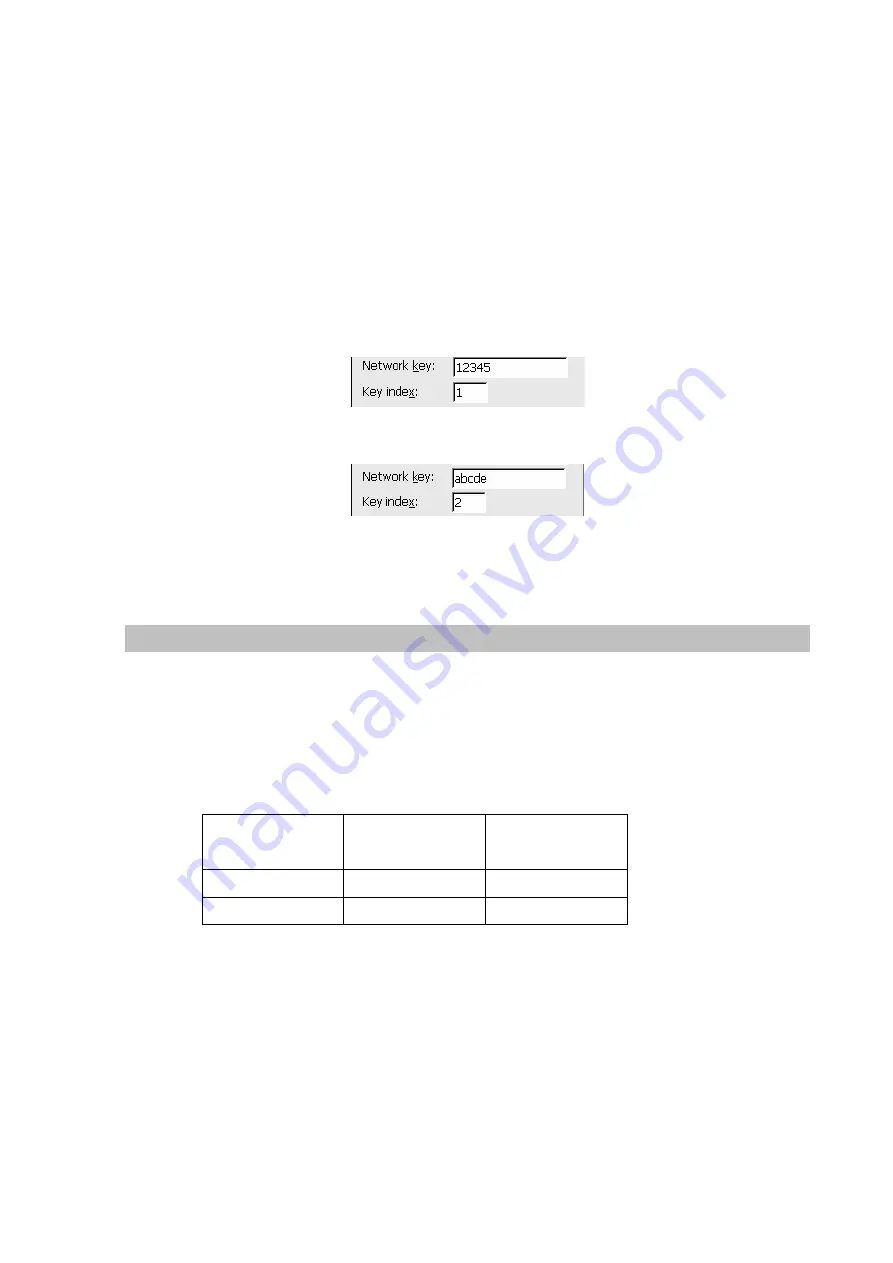
Also, some APs allow you to have more than 1 key. If you are using such AP, you can specify your keys
by changing the Key Index field. For example, you can have the 1
st
key at “12345” by specifying the
Key Index field to be 1, and another key at “abcde” with Key Index to be 2, just as shown below:
Figure 204. Wep 1
st
key
Figure 205. Wep 2
nd
When using such AP, the phone will transmit and receive by randomly picking one of the available keys.
WPA (Wifi Protected Access)
WiFi Protected Access (WPA and WPA2) was created in response to several serious weaknesses
found in WEP. WPA is designed for use with an 802.1X authentication server, which distributes different
keys to each user. However, it can also be used in a less secure "pre-shared key" (PSK) mode, where
every user is given the same password.
The following table shows the difference in authentication and encryption between these 2 modes:
Authentication
Method
Encryption
Method
Enterprise Mode
IEEE 802.1X/EAP
TKIP
Personal Mode
PSK TKIP
Table 7. WPA encryption description
P e r s on a l M o d e
WPA-PSK is a special mode of WPA for users without an enterprise authentication server and provides
the same strong encryption protection as WPA. It provides encryption with a mechanism known as
rekeying where encryption keys are automatically generated, changed and authenticated between the
phone and the AP after a specified period of time, or after a specified number of packets has been
transmitted. This duration is called the rekey interval.
116















































