Release 6.0
443
Appendix O CHAP Authentication
Challenge Handshake Authentication Protocol (CHAP) is an authentication method. This appendix describes
the CHAP authentication and its settings.
O.1 General
A random text string called a “challenge” is sent from the server to the client, and the client uses it as
the basis for encrypting its own “Secret” (password), which it returns. Because the server has the
client's Secret (password), it performs the same encryption and compares the result to the encrypted
code returned from the client to enable authentication of users.
O.2 Constraints on Secrets
Although this device enables use of 12- to 32-character string lengths, typically Initiator restricts the
CHAP Secrets to 16-character (128-bit) strings. (As of February 2009)
Do not set the same values to the Initiator CHAP Secret and the target CHAP Secret that are used
for bidirectional CHAP authentication.
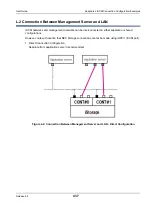
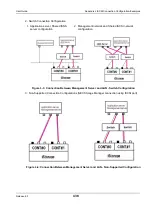
O.3 Description of Operation Modes
1. CHAP authentication for Initiator
Only authentication of the application server (Initiator) from the disk array unit (iSCSI target) is
performed.
Only target CHAP Secret is set.
2. Bidirectional CHAP authentication
Authentication is performed mutually for the disk array unit (iSCSI target) and the application server
(Initiator). Both a target CHAP Secret and an Initiator CHAP Secret are set.
O.4 CHAP Username Setting
1. Set the target name (when it can be set) as the CHAP username (target side).
2. Unless otherwise specified, set the Initiator name as the CHAP username (Initiator side).
(If using another name, maximum length is 256 characters.)
Microsoft iSCSI Software Initiator refers to this as "Mutual CHAP".
Содержание M100
Страница 25: ...Release 6 0 25 User Guide About Warning Labels Power Supply AC Power Supply ...
Страница 27: ...Release 6 0 27 User Guide About Warning Labels Battery ...
Страница 29: ...Release 6 0 29 User Guide About Warning Labels Power Cable AC Power Supply ...
Страница 40: ...Release 6 0 40 User Guide Chapter 1 Overview 1 2 1 4 Controller CONT ...
Страница 48: ...Release 6 0 48 User Guide Chapter 1 Overview 1 2 3 3 Controller CONT ...
Страница 75: ...Release 6 0 75 User Guide Chapter 3 Installing the Disk Array System Figure 3 10 Securing Unit 2 ...
Страница 88: ...Release 6 0 88 User Guide Chapter 4 NEC Storage Manager Figure 4 1 Example of Recommended Configuration ...
Страница 125: ...Release 6 0 125 User Guide Chapter 4 NEC Storage Manager d Click Login to open the main screen Figure 4 26 Main Screen ...
Страница 194: ...Release 6 0 194 User Guide Chapter 6 Initializing a Disk Array iSCSI Figure 6 16 Hot Spare Bind View Display ...
Страница 260: ...Release 6 0 260 User Guide Chapter 8 Installing Optional Parts Figure 8 12 Removing the DIMMs ...
Страница 388: ...Release 6 0 388 User Guide Appendix F How to Set Check Application Server Linux iSCSI Figure F 3 Configuration Example ...
Страница 459: ...NEC Corporation 7 1 Shiba 5 chome Minato ku Tokyo 108 8001 Japan URL http www necstorage com ...