11.1 SMB related settings (Solarish CIFS)
SMB Service
The SMB service is started automatically when you enable a share.
Some modifications (like share level ACL) require a service restart. This is done automatically by napp-it.
On problems with the SMB server or if you are in a AD Domain that was temporarely unavailable,
it may be needed to restart the service manually in menu „Services >> SMB“
If you import a pool with shares enabled and SMB service disabled, you may get a warning that the SMB
service is not enabled. You can ignore as the service is started automatically or after a share off/on.
Set netbios_enable=true (allow Windows network browsing) in menu Services > SMB > properties
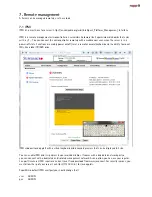
SMB Share On
As SMB Sharing is a in Solarish and ZFS integrated property of filesystem, you can enable a share in menu
ZFS Filesystems when you click on off in the row of a filesystem under SMB with the following options:
- sharename: The share is visible to a client like Windows under this name
if you add a „$“ to the name, the share is hidden, example userdata$
To connect such a hidden share, you must connect from Windows like \\datanode-01\userdata$
- guest allowed: You do not need to login with a name and password to access the share (ex from Windows)
- ABE (access based enumeration): Only files and folders are visible where you have permissions
SMB Share off
To disable a share, click on the sharename in the row of the filesystem and set sharesmb = off
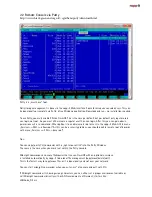
SMB permissions
In contrast to other Unix services, Solarish CIFS uses Windows alike NFS4 ACL with permission inheritance,
not traditional Unix permissions like 755 or Posix ACLs ( https://en.wikipedia.org/wiki/Access_control_list ).
This is the reason why you should not set Unix permissions like 755 on files/folders that are shared over SMB
as this would delete ACL inheritance settings that are not know in traditional Unix.
Always use ACL to set permissions on Solarish. As tradititional Unix permissions are a subset of the ACL
possibilities, they are reduced automatically to fit the ACL permissions.
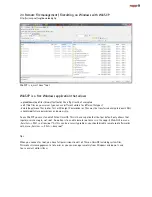
As ZFS is a Unix filesystem, it must use Unix UID and GID as file security attributes. Solarish CIFS additionally
store Windows Security ID‘s (SID) as extended ZFS attributs. They are used by the CIFS server only and allows
file movements/ backups where Windows NTFS alike permissions were preserved - does not matter what UID a
user has. This is an advantage especially in an AD environment.
When you create a new ZFS filesystem with napp-it, the default permission is set to
root = full access
everyone@ = modify
This allows that any user can connect a SMB share with read/write permissions as default.
If you do not create new users, only root has (full) access to regular SMB shares at the moment
unless you do not had enabled the guest option that allows a connect without login.
If you replicate or move a pool to another Solarish server that is also a domain-member,
all permissions stay intact as the Windows SID/ security ID is stored as an extended ZFS attribute.
This is unique for a Unix filesystem.
Содержание ZFS Storage
Страница 8: ...3 1 ZFS Configurations...
Страница 45: ...Example Map Chenbro 50 x 3 5 Bay...