either
a
SSH
version
1.5
or
SSH
version
2
client.
For
security,
the
secure
shell
server
private
key
is
not
backed-up
during
a
configuration
save
and
restore
operation.
The
following
third-party
SSH
clients
are
available.
While
some
SSH
clients
have
been
tested,
support
or
non-support
of
any
particular
SSH
client
is
not
implied.
v
The
SSH
clients
distributed
with
operating
systems
such
as
Linux,
AIX
®
,
and
UNIX
®
(see
your
operating-system
documentation
for
information).
The
SSH
client
of
Red
Hat
Linux
7.3
was
used
to
test
the
command-line
interface.
v
The
SSH
client
of
cygwin
(see
for
information)
The
following
table
shows
the
types
of
encryption
algorithms
that
are
supported,
based
on
the
SSH
version
that
is
being
used.
Algorithm
SSH
version
1.5
clients
SSH
version
2.0
clients
Public
key
exchange
SSH
1-key
exchange
algorithm
Diffie-Hellman-group
1-sha-1
Host
key
type
RSA
(1024-bit)
DSA
(1024-bit)
Bulk
cipher
algorithms
3-des
3-des-cbc
or
blowfish-cbc
MAC
algorithms
32-bit
crc
Hmac-sha1
Complete
the
following
steps
to
create
a
new
secure
shell
server
key:
1.
In
the
navigation
pane,
click
MM
Control
→
Security
.
2.
Scroll
to
the
Secure
Shell
(SSH)
Server
section
and
make
sure
that
the
secure
shell
server
is
disabled.
If
it
is
not
disabled,
select
Disabled
in
the
SSH
Server
field
and
then
click
Save
.
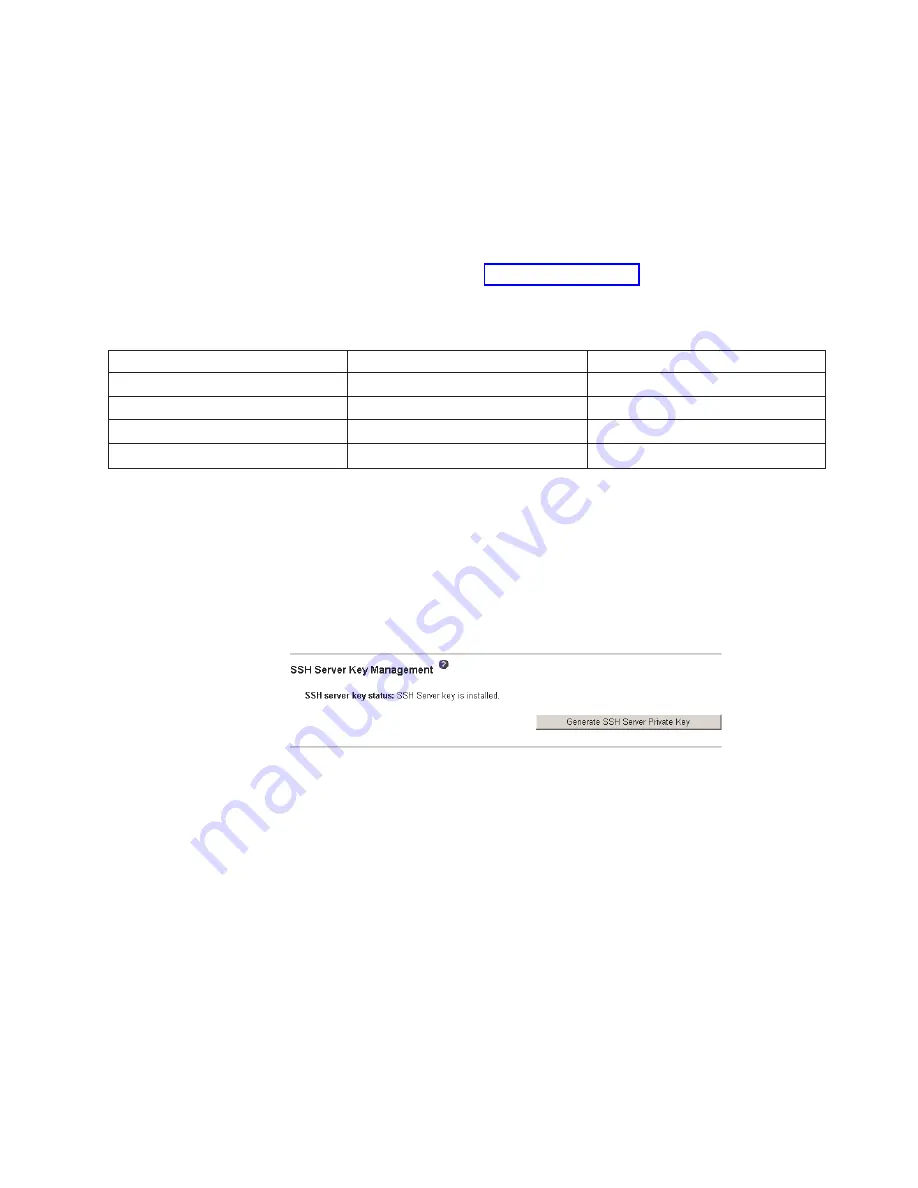
3.
Scroll
to
the
SSH
Server
Key
Management
section.
A
page
similar
to
the
one
in
the
following
illustration
is
displayed.
4.
Click
Generate
SSH
Server
Private
Key
.
A
progress
window
is
displayed.
Wait
for
the
operation
to
finish.
This
step
might
take
several
minutes
to
complete.
Enabling
the
secure
shell
server
From
the
Security
page
you
can
enable
or
disable
the
secure
shell
server.
The
selection
that
you
make
takes
effect
only
after
the
management
module
is
restarted.
The
value
displayed
on
the
screen
(Enabled
or
Disabled)
is
the
last
value
selected
and
is
the
value
used
when
the
management
module
is
restarted.
Note:
You
can
enable
the
secure
shell
server
only
if
a
valid
secure
shell
server
private
key
is
installed.
Complete
the
following
steps
to
enable
the
secure
shell
server:
1.
In
the
navigation
pane,
click
Security
.
Chapter
3.
Using
the
management-module
Web
interface
53
Содержание BladeCenter Management Module
Страница 1: ...BladeCenter Management Module User s Guide ERserver...
Страница 2: ......
Страница 3: ...BladeCenter Management Module User s Guide ERserver...
Страница 10: ...viii BladeCenter Management Module User s Guide...
Страница 20: ...10 BladeCenter Management Module User s Guide...
Страница 74: ...64 BladeCenter Management Module User s Guide...
Страница 77: ......
Страница 78: ...Part Number 13N0318 Printed in USA 1P P N 13N0318...






























