| Authentication and Authorization |
289
Success:
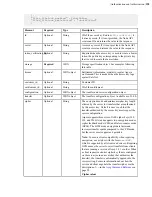
The following example shows a successful verification for one root certificate and two intermediary
certificates in the chain:
Certificate chain
0
s:/C=US/ST=California/L=Emeryville/O=IBM/OU=Aspera Inc IT Department/
CN=*.asperafiles.com
i:/C=US/O=Symantec Corporation/OU=Symantec Trust Network/CN=Symantec
Class 3 Secure Server CA - G4
1
s:/C=US/O=Symantec Corporation/OU=Symantec Trust Network/CN=Symantec
Class 3 Secure Server CA - G4
i:/C=US/O=VeriSign, Inc./OU=VeriSign Trust Network/OU=(c) 2006
VeriSign, Inc. - For authorized use only/CN=VeriSign Class 3 Public
Primary Certification Authority - G5
2
s:/C=US/O=VeriSign, Inc./OU=VeriSign Trust Network/OU=(c) 2006
VeriSign, Inc. - For authorized use only/CN=VeriSign Class 3 Public
Primary Certification Authority - G5
i:/C=US/O=VeriSign, Inc./OU=Class 3 Public Primary Certification
Authority
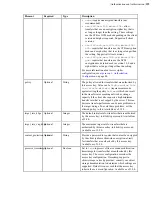
Failure:
The following example shows an unsuccessful verification, since only the root certificate is
displayed.
Certificate chain
0 s:/C=US/ST=California/L=Emeryville/O=IBM/OU=Aspera Inc IT Department/
CN=*.asperafiles.com
i:/C=US/O=Symantec Corporation/OU=Symantec Trust Network/CN=Symantec
Class 3 Secure Server CA - G4
b) If verification fails, inspect your certificate content by running the following command:
# /opt/aspera/bin/openssl x509 -in certificate.crt -text -noout
Authentication and Authorization
Introduction to Aspera Authentication and Authorization
HST Server can be configured to support SSH or HTTPS authentication and authorization for browsing and transfers.
For both methods, the client
ascp
process connects to the server by using the SSH protocol and initiates the server-
side
ascp
process. Therefore, SSH connectivity and authentication to the server is always used.
SSH:
SSH authentication is the original method for authentication, and is typically used for transfers between Aspera
clients and servers. SSH authentication requires a system user account that is configured with a docroot or restriction
in
aspera.conf
. The user can authenticate by providing a system password or SSH key.
HTTPS:
HTTPS (Node API) authentication was introduced to support browsing and transfers that are initiated
through Aspera web applications (IBM Aspera Faspex, IBM Aspera Shares, and IBM Aspera on Cloud), and uses a
token-based authorization security layer in addition to SSH.
Authorization Tokens:
When the server is configured for token authorization, the server-side
ascp
process requires
a valid token from the client before it can start. It is the responsibility of the client to provide this token. The Aspera
web applications do this automatically through HTTPS (Node API). The IBM Aspera Desktop Client GUI and IBM
Aspera Command-Line Interface do this automatically when connecting to Aspera web applications.
Types of Tokens
Aspera uses three types of tokens: transfer tokens, basic tokens, and bearer tokens.