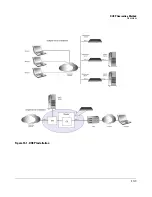
802.1X Quarantine Method
About 802.1X
11-2
About 802.1X
802.1X is a port-based authentication protocol that can dynamically vary
encryption keys, and has three components as follows:
■
Supplicant – The client; the endpoint that wants to access the
network.
■
Authenticator– The access point, such as a switch, that prevents
access when authentication fails. The authenticator can be simple and
dumb.
■
Authentication server – The server that authenticates the user creden-
tials; usually a Remote Authentication Dial-In User Service (RADIUS)
server.
802.1X is an authentication framework that sends Extensible Authentication
Protocol (EAP) messages packaged in Ethernet frames over LANs (EAPOL).
This method provides a savings in overhead resources because it does not use
all of the resources the typical Point-to-Point protocol requires.
EAP supports multiple authentication methods such as:
■
Kerberos – An authentication system that uses an encrypted ticket to
authenticate users.
■
One-time passwords – An authentication system that uses a set of
rotating passwords, each of which is used for only one login session.
■
Certificates – A method for identifying a user that links a public key
to the user’s or company’s identity, allowing them to send digitally
signed electronic messages.
■
Tokens – A credit-card or key-fob sized authentication endpoint that
displays a number that is synchronized with the authentication server.
The number changes over time, and the user is required to enter the
current number as part of the authentication process.
■
Public key authentication – In an asymmetric encryption system, two
keys are required; a public key and a private key. Either key can
encrypt and decrypt messages, but cannot encrypt and decrypt the
same message; that is, if the public key encrypts a message, the private
key must decrypt the message.
The typical 802.1X connections are shown in Figure 11-1 on page 11-3; The
typical communication flow is as follows:
1.
A Client (supplicant) requests access from the access point (AP)
(authenticator).
Содержание ProCurve NAC 800
Страница 1: ...HP ProCurve Network Access Controller 800 Users Guide ...
Страница 2: ......
Страница 3: ...ProCurve Network Access Controller 800 Release 1 1 Users Guide ...
Страница 32: ...Introduction Technical Support 1 14 Technical Support Technical support is available through www procurve com ...
Страница 43: ...2 1 2 Clusters and Servers Chapter Contents Overview 2 2 Installation Examples 2 3 ...
Страница 71: ...System Configuration Management Server 3 23 Figure 3 9 System Configuration Management Server ...
Страница 80: ...System Configuration User Accounts 3 32 Figure 3 12 System Configuration User Accounts ...
Страница 88: ...System Configuration User Roles 3 40 Figure 3 16 System Configuration User Roles ...
Страница 100: ...System Configuration Quarantining General 3 52 1 Select a cluster Figure 3 23 System Configuration Quarantining ...
Страница 171: ...System Configuration Cluster Setting Defaults 3 123 Figure 3 55 System Configuration Agentless Credentials ...
Страница 180: ... This page intentionally left blank ...
Страница 208: ... This page intentionally left blank ...
Страница 234: ...End user Access Mac OS X Endpoint Settings 5 26 Figure 5 14 Mac System Preferences ...
Страница 288: ... This page intentionally left blank ...
Страница 302: ... This page intentionally left blank ...
Страница 303: ...8 1 8 High Availability and Load Balancing Chapter Contents High Availability 8 2 Load Balancing 8 6 ...
Страница 306: ...High Availability and Load Balancing High Availability 8 4 Figure 8 2 DHCP Installation ...
Страница 307: ...High Availability and Load Balancing High Availability 8 5 Figure 8 3 802 1X Installation ...
Страница 309: ...9 1 9 Inline Quarantine Method Chapter Contents Inline 9 2 ...
Страница 312: ... This page intentionally left blank ...
Страница 315: ...DHCP Quarantine Method Overview 10 3 Figure 10 1 DHCP Installation ...
Страница 318: ... This page intentionally left blank ...
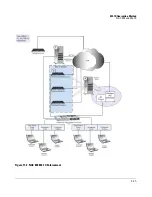
Страница 323: ...802 1X Quarantine Method NAC 800 and 802 1X 11 5 Figure 11 2 NAC 800 802 1X Enforcement ...
Страница 324: ...802 1X Quarantine Method NAC 800 and 802 1X 11 6 Figure 11 3 802 1X Communications ...
Страница 380: ... This page intentionally left blank ...
Страница 418: ... This page intentionally left blank ...
Страница 425: ...Reports Viewing Report Details 14 7 Figure 14 3 Test Details Report ...
Страница 459: ...System Administration Creating and Replacing SSL Certificates 15 31 10 Save and exit the file ...
Страница 468: ... This page intentionally left blank ...
Страница 480: ... This page intentionally left blank ...
Страница 526: ...Tests Help Security Settings Windows B 34 http www pcworld com article id 112138 article html ...
Страница 532: ... This page intentionally left blank ...
Страница 535: ...Important Browser Settings Pop up Windows C 3 1 Clear the Block Popup Windows check box 2 Close the Content window ...
Страница 562: ... This page intentionally left blank ...
Страница 590: ... This page intentionally left blank ...