•
limit user access to authenticate to the directory.
•
limit the ability of an authenticated user to receive LOM privileges based on
rights specified in one or more roles.
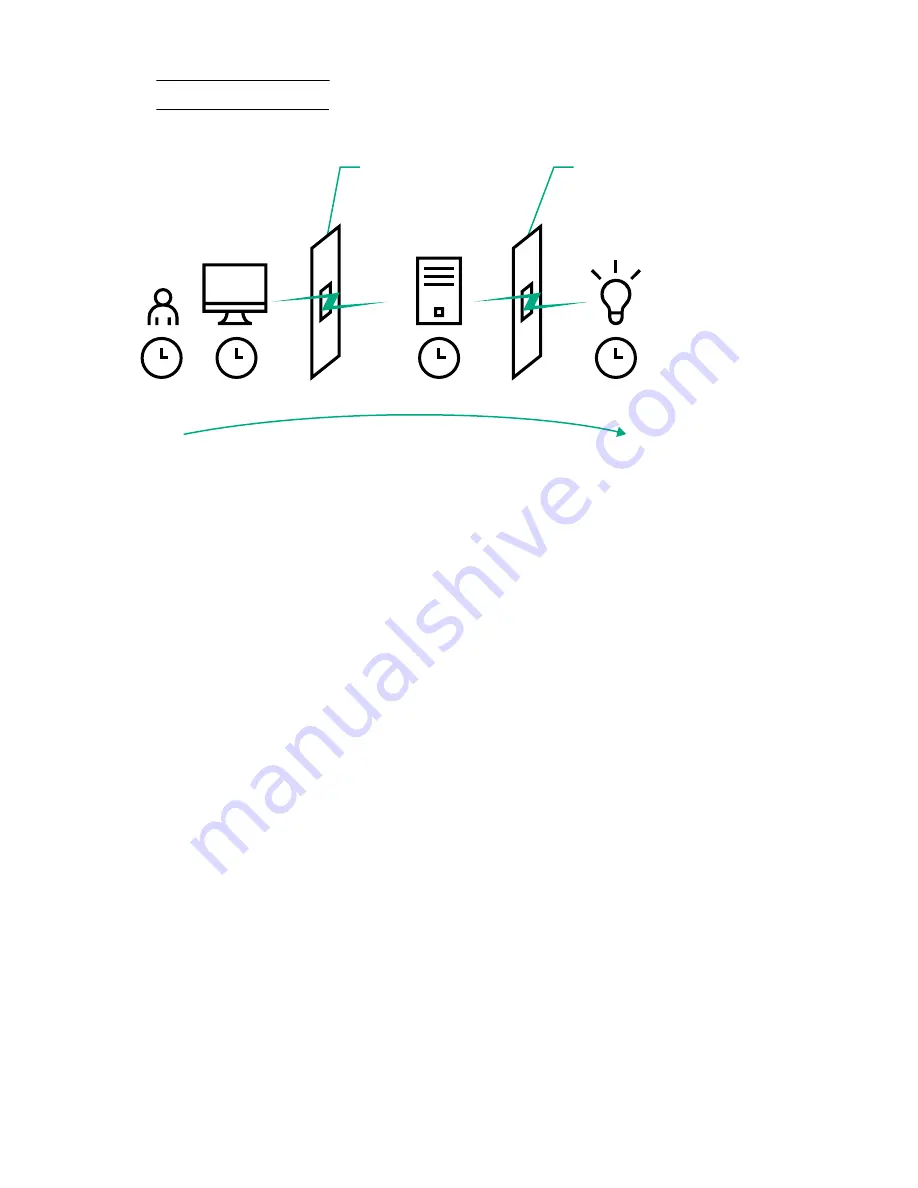
User
LOM
Client
Workstation
Directory
Server
User restrictions must be met to
authenticate to the directory.
Enforced by the directory
server.
Role restrictions must be
met to receive rights
granted by one or more roles.
Enforced by LOM.
Role access
restrictions
User access
restrictions
12
6
3
9
12
6
3
9
12
6
3
9
12
6
3
9
Figure 10: Directory login restrictions
User access restrictions
User address restrictions
Administrators can place network address restrictions on a directory user account. The directory server
enforces these restrictions.
For information about the enforcement of address restrictions on LDAP clients, such as a user logging in
to a LOM device, see the directory service documentation.
Network address restrictions placed on a user in a directory might not be enforced as expected when a
directory user logs in through a proxy server. When a user logs in to a LOM device as a directory user,
the LOM device attempts authentication to the directory as that user, which means that address
restrictions placed on the user account apply when the user accesses the LOM device. When a proxy
server is used, the network address of the authentication attempt is that of the LOM device, not that of the
client workstation.
IPv4 address range restrictions
IP address range restrictions enable the administrator to specify network addresses that are granted or
denied access.
The address range is typically specified in a low-to-high range format. An address range can be specified
to grant or deny access to a single address. Addresses that fall within the low-to-high IP address range
meet the IP address restriction.
IPv4 address and subnet mask restrictions
IP address and subnet mask restrictions enable the administrator to specify a range of addresses that are
granted or denied access.
This format is similar to an IP address range restriction, but it might be more native to your networking
environment. An IP address and subnet mask range is typically specified through a subnet address and
address bit mask that identifies addresses on the same logical network.
User access restrictions
329