319
c.
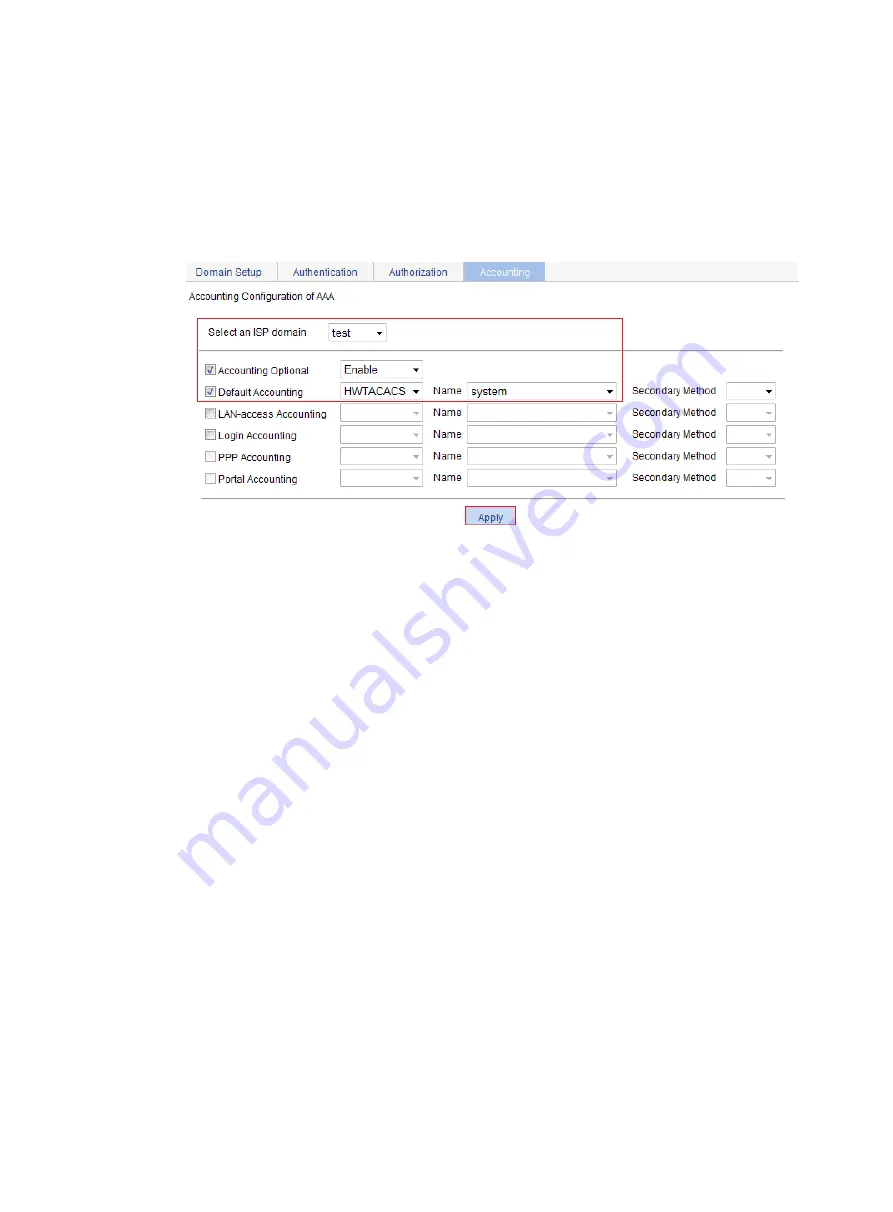
Select
Accounting Optional
, and then select
Enable
from the list.
d.
Select
Default Accounting
, and then select
HWTACACS
from the list.
e.
Select
system
from the
Name
list.
f.
Click
Apply
.
A progress dialog box appears.
g.
When the configuration progress is complete, click
Close
.
Figure 345 Configuring an accounting method for the ISP domain
Verifying the configuration
# Initiate a connection to the HPE NJ5000 5G PoE+ switch from the host, and enter the username
hello@test
and the password
123456
. Verify that you can access the user interface of the HPE
NJ5000 5G PoE+ switch. (Details not shown.)
# Display online user connection information.
<HPE> display connection
Slot: 1
Index=0 , Username=hello
IP=192.168.1.12
IPv6=N/A
Index=5 , Username=hello
IP=0.0.0.0
Ipv6=N/A
Total 2 connection(s) matched on slot 1.
Total 2 connection(s) matched.
Configuration guidelines
When you configure the HWTACACS client, follow these guidelines:
•
You cannot delete an HWTACACS scheme that is being used for users, nor can you change the
server IP addresses of the scheme.
•
Except for deleting HWTACACS schemes and changing the IP addresses of the HWTACACS
servers, you can make any changes to HWTACACS parameters, no matter whether there are
users online or not.
Содержание FlexNetwork NJ5000
Страница 12: ...x Index 440 ...
Страница 39: ...27 Figure 16 Configuration complete ...
Страница 67: ...55 Figure 47 Displaying the speed settings of ports ...
Страница 78: ...66 Figure 59 Loopback test result ...
Страница 158: ...146 Figure 156 Creating a static MAC address entry ...
Страница 183: ...171 Figure 171 Configuring MSTP globally on Switch D ...
Страница 243: ...231 Figure 237 IPv6 active route table ...
Страница 293: ...281 Figure 298 Ping operation summary ...






























