P a g e
|
19
UCM Security Manual
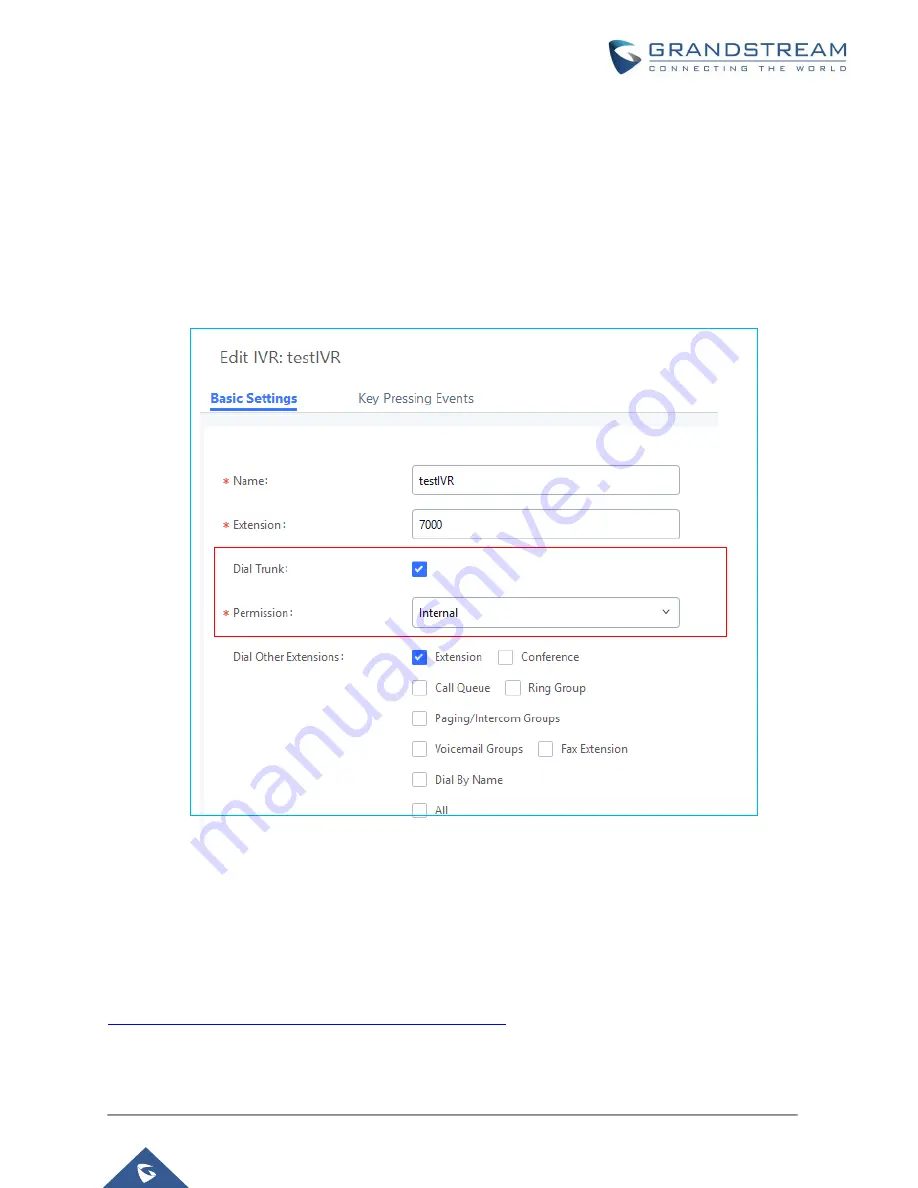
IVR Dial Trunk
When creating/editing an IVR, the administrator could decide whether to allow the calls entering the IVR to
make outbound calls through trunks by configuring “Dial Trunk” and “Permission”. If “Dial Trunk” option is
enabled, the caller calling into the IVR will be able to dial external numbers through a trunk if the IVR’S
permission is higher than or equal to the privilege of the trunk. The potential risk here is that unwanted
users may call into IVR and then dial external number. This could possibly generate expected high charges
especially if an IVR is configured as the destination of an inbound route of a PSTN trunk, in which case,
anyone can call into the IVR and then dial out to long distance or international calls.
Figure 14: IVR Dial Trunk
We recommend disabling “Dial Trunk” option unless the risk associated with it is clearly understood or the
PBX administrator intentionally configures it to do so for specific reasons. If it has to be enabled, please
configure the “permission” as secure as possible to restrict the authorized callers to be known users.
For more information about IVR permissions, please refer to IVR PERMISSION section in white paper:
How to manage inbound/outbound route on UCM6510/6100













































