IPSec VPN
Manual Key
FortiGate Version 4.0 Administration Guide
01-400-89802-20090424
541
•
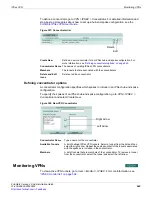
Manual Key
If required, you can manually define cryptographic keys for establishing an IPSec VPN
tunnel. You would define manual keys in situations where:
•
You require prior knowledge of the encryption or authentication key (that is, one of the
VPN peers requires a specific IPSec encryption or authentication key).
•
You need to disable encryption and authentication.
In both cases, you do not specify IPSec phase 1 and phase 2 parameters; you define
manual keys by going to
VPN > IPSEC > Manual Key
instead.
For general information about how to configure an IPSec VPN, see the
Quick Mode
Selector
Optionally specify the source and destination IP addresses to be used as selectors
for IKE negotiations. If the FortiGate unit is a dialup server, you should keep the
default value 0.0.0.0/0 unless you need to circumvent problems caused by
ambiguous IP addresses between one or more of the private networks making up
the VPN. You can specify a single host IP address, an IP address range, or a
network address. You may optionally specify source and destination port numbers
and a protocol number.
If you are editing an existing phase 2 configuration, the
Source address
and
Destination address
fields are unavailable if the tunnel has been configured to use
firewall addresses as selectors. This option exists only in the CLI. For more
information, see the
dst-addr-type
,
dst-name
,
src-addr-type
and
src-
name
keywords for the
vpn ipsec phase2
.
Source address
If the FortiGate unit is a dialup server, type the source IP
address that corresponds to the local senders or network
behind the local VPN peer (for example,
172.16.5.0/24
or
172.16.5.0/255.255.255.0
for a subnet, or
172.16.5.1/32
or
172.16.5.1/255.255.255.255
for a
server or host, or
192.168.10.[80-100]
or
192.168.10.80-192.168.10.100
for an address range).
A value of
0.0.0.0/0
means all IP addresses behind the
local VPN peer.
If the FortiGate unit is a dialup client, source address must
refer to the private network behind the FortiGate dialup client.
Source port
Type the port number that the local VPN peer uses to
transport traffic related to the specified service (protocol
number). The range is from 0 to 65535. To specify all ports,
type
0
.
Destination
address
Type the destination IP address that corresponds to the
recipients or network behind the remote VPN peer (for
example,
192.168.20.0/24
for a subnet, or
172.16.5.1/32
for a server or host, or
192.168.10.[80-
100]
for an address range). A value of
0.0.0.0/0
means all
IP addresses behind the remote VPN peer.
Destination port
Type the port number that the remote VPN peer uses to
transport traffic related to the specified service (protocol
number). The range is from 0 to 65535. To specify all ports,
type
0
.
Protocol
Type the IP protocol number of the service. The range is from
0
to
255
. To specify all services, type
0
.
Note:
You should use manual keys only if it is unavoidable. There are potential difficulties in
keeping keys confidential and in propagating changed keys to remote VPN peers securely.
Содержание Gate 60D
Страница 678: ...Reports Log Report FortiGate Version 4 0 Administration Guide 678 01 400 89802 20090424 http docs fortinet com Feedback...
Страница 704: ...Index FortiGate Version 4 0 Administration Guide 704 01 400 89802 20090424 http docs fortinet com Feedback...
Страница 705: ...www fortinet com...
Страница 706: ...www fortinet com...