What’s new in FortiOS 4.0
User authentication monitor
FortiGate Version 4.0 Administration Guide
01-400-89802-20090424
39
•
User authentication monitor
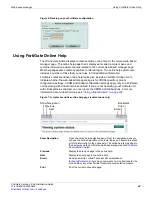
You can now go to
User > Authentication > User Authentication Monitor
to view a list of
currently authenticated users. For each authenticated user, the list includes the user
name, user group, how long the user has been authenticated (duration), how long until the
user’s session times out (time-left), the user’s source IP Address, the amount of traffic
through the FortiGate unit caused by the user (traffic volume), and the authentication
method used by the FortiGate unit for the user. The authentication methods can be FSAE,
firewall authentication (FW-auth), or NTLM. You can sort and filter the information on the
authentication monitor according to any of the columns in the monitor.
For more information, see
.
OCSP and SCEP certificate over HTTPS
FortiGate units now support OCSP and SCEP communication between FortiGate units
and SCEP servers over HTPPS. The SCEP URLs that you add to the FortiGate System
Certificate configuration can be HTTPS URLs or URLs supported by your SCEP server.
For more information, see
“System Certificates” on page 243
.
Adding non-standard ports for firewall authentication
By default, when a communication session is accepted by an identity-based firewall policy,
the user must authenticate with the firewall by using the FTP, HTTP, HTTPS, or Telnet
protocol to enter a user name and password before being able to communicate through
the FortiGate unit. And, by default, users can authenticate only with a communication
session that uses the standard FTP, HTTP, HTTPS, or Telnet TCP ports (21, 80, 443, and
23 respectively).
You can now use the following command if your firewall users need to authenticate with
the FortiGate unit and if they use a non-standard port for FTP, HTTP, HTTPS, or Telnet
sessions.
config user setting
config auth-ports
edit <auth_port_table_id_int>
set port <port_integer>
set type { ftp | http | https | telnet }
end
end
end
Where
<auth_port_table_id_int>
is any integer. You can add multiple non-standard
port tables.
<port_integer>
is the non-standard TCP authentication port number.
Adding non-standard authentication ports does not change the standard authentication
port for any protocol. You use this command only to add more non-standard
authentication ports. The standard authentication port is still valid and cannot be changed.
For example, if some users on your network web browse using HTTP on ports 8080 and
8008 and use telnet on port 4523, you could use the following commands to add HTTP
authentication on ports 8080 and 8008 and Telnet authentication on port 4523:
config user setting
config auth-ports
edit 1
set port 8080
Содержание Gate 60D
Страница 678: ...Reports Log Report FortiGate Version 4 0 Administration Guide 678 01 400 89802 20090424 http docs fortinet com Feedback...
Страница 704: ...Index FortiGate Version 4 0 Administration Guide 704 01 400 89802 20090424 http docs fortinet com Feedback...
Страница 705: ...www fortinet com...
Страница 706: ...www fortinet com...